Update 12/4/14: Dedicated guide with all known information can be found here:
Added new information guide and FAQ:
TorrentLocker (fake CryptoLocker) Ransomware Information Guide and FAQ
Also contains country specific information. If you are from a country listed, or not listed, and have further info please feel free to shoot me a PM.
http://www.bleepingcomputer.com/virus-removal/torrentlocker-cryptolocker-ransomware-information#regions
TorrentLocker is a ransomware that was released in late August to early September that pretends to be CryptoLocker. This ransomware will encrypt all of your data files and then display a ransom screen that demands 1.14 BTC in order to get a decrypter. If you wait too long, this ransom amount will double to a cap of 2.28 BTC. Many people are confusing this infection with the original CryptoLocker infection, but the only similarities is that this ransomware is using the same name. If you have been infected with something called CryptoLocker after June 2nd, 2014 then you are not infected with the original CryptoLocker, but instead by a new ransomware using the same name. If you have been infected recently with an infection called CryptoLocker, it is probably the TorrentLocker infection that this topic discusses.
Main Startup Window and Ransom Note
In the past, this infection was using an easy to decrypt XOR encryption method. Unfortunately, some researchers decided to publicly blog about this encryption method, which caused the malware developer to change the encryption to a much stronger and unbreakable decryption using AES. Due to this change, Nathan Scott's TorrentLocker decrypter no longer works on this infection.
When infected, this infection will scan your drive for data files and encrypt them using AES encryption. The infection uses a open source library called LibTom, which easily allows the malware developers to use a variety of encryption methods. Once your data has been encrypted, it will leave ransom notes in each folder that has encrypted files and then display a ransom note requesting payment.
The file extensions targetted by this ransomware are:
*.wb2,*.psd,*.p7c,*.p7b,*.p12,*.pfx,*.pem,*.crt,*.cer,*.der,*.pl,*.py,*.lua,*.css,*.js,*.asp,*.php,*.incpas,*.asm,*.hpp,*.h,*.cpp,*.c,*.7z,*.zip,*.rar,*.drf,*.blend,*.apj,*.3ds,*.dwg,*.sda,*.ps,*.pat,*.fxg,*.fhd,*.fh,*.dxb,*.drw,*.design,*.ddrw,*.ddoc,*.dcs,*.csl,*.csh,*.cpi,*.cgm,*.cdx,*.cdrw,*.cdr6,*.cdr5,*.cdr4,*.cdr3,*.cdr,*.awg,*.ait,*.ai,*.agd1,*.ycbcra,*.x3f,*.stx,*.st8,*.st7,*.st6,*.st5,*.st4,*.srw,*.srf,*.sr2,*.sd1,*.sd0,*.rwz,*.rwl,*.rw2,*.raw,*.raf,*.ra2,*.ptx,*.pef,*.pcd,*.orf,*.nwb,*.nrw,*.nop,*.nef,*.ndd,*.mrw,*.mos,*.mfw,*.mef,*.mdc,*.kdc,*.kc2,*.iiq,*.gry,*.grey,*.gray,*.fpx,*.fff,*.exf,*.erf,*.dng,*.dcr,*.dc2,*.crw,*.craw,*.cr2,*.cmt,*.cib,*.ce2,*.ce1,*.arw,*.3pr,*.3fr,*.mpg,*.jpeg,*.jpg,*.mdb,*.sqlitedb,*.sqlite3,*.sqlite,*.sql,*.sdf,*.sav,*.sas7bdat,*.s3db,*.rdb,*.psafe3,*.nyf,*.nx2,*.nx1,*.nsh,*.nsg,*.nsf,*.nsd,*.ns4,*.ns3,*.ns2,*.myd,*.kpdx,*.kdbx,*.idx,*.ibz,*.ibd,*.fdb,*.erbsql,*.db3,*.dbf,*.db-journal,*.db,*.cls,*.bdb,*.al,*.adb,*.backupdb,*.bik,*.backup,*.bak,*.bkp,*.moneywell,*.mmw,*.ibank,*.hbk,*.ffd,*.dgc,*.ddd,*.dac,*.cfp,*.cdf,*.bpw,*.bgt,*.acr,*.ac2,*.ab4,*.djvu,*.pdf,*.sxm,*.odf,*.std,*.sxd,*.otg,*.sti,*.sxi,*.otp,*.odg,*.odp,*.stc,*.sxc,*.ots,*.ods,*.sxg,*.stw,*.sxw,*.odm,*.oth,*.ott,*.odt,*.odb,*.csv,*.rtf,*.accdr,*.accdt,*.accde,*.accdb,*.sldm,*.sldx,*.ppsm,*.ppsx,*.ppam,*.potm,*.potx,*.pptm,*.pptx,*.pps,*.pot,*.ppt,*.xlw,*.xll,*.xlam,*.xla,*.xlsb,*.xltm,*.xltx,*.xlsm,*.xlsx,*.xlm,*.xlt,*.xls,*.xml,*.dotm,*.dotx,*.docm,*.docx,*.dot,*.doc,*.txtWhen you click on the links in the ransom note you will be brought to the CryptoLocker Decryption Software site where you can learn how to purchase the decrypter. Like other infections, this site will require you to send the specified amount of bitcoins to a particular address and then input the transaction ID to verify payment. Once payment has been established, you will be offered a decryption program that you can download to decrypt your files. The decryption site also offers a customer support form, frequently asked questions section, and the ability to decrypt one file for free.
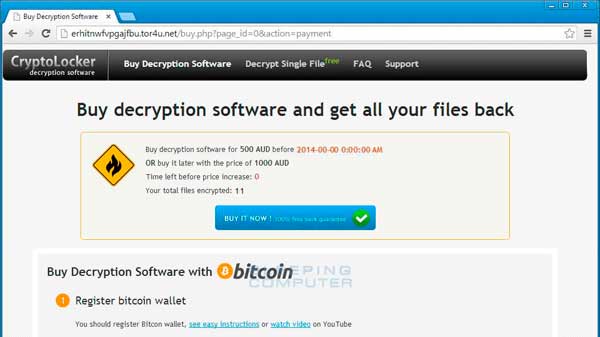
Click above to see the full image.
Originally, this infection used a static bitcoin address of 13qm2ezhWSHWzMsGcxtKDhKNnchfP5Sp3X to receive payments. Later versions switched to using a unique bitcoin address for each victim.
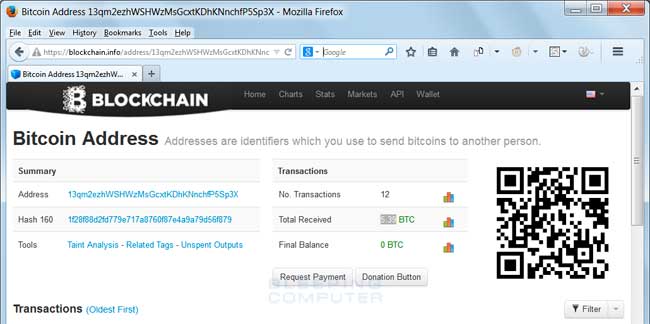
Click above to see the full image.
This infection does not use a secure deletion method of your original files. Due to this you can may be able to use a file recovery software such as R-Studio or Photorec to recover some of your original files. It is important to note that the more you use your computer after the files are encrypted the more difficult it will be for file recovery programs to recover the deleted un-encrypted files.
Files used by this infection are:
C:\ProgramData\<random>.exe C:\ProgramData\<random>.html C:\Users\All Users\<random>.exe C:\Users\All Users\<random>.htmlRegistry keys used by this infection are:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\<random> C:\ProgramData\<random>.exe HKCU\Software\<Random>




 Back to top
Back to top


 as for my decrypter, perhaps read further on the thread you first found it on, and you will see that because security researchers releasing information, my decrypter gor patched with v2. Had you had the first one (which is no longer used) it would have been able to help you.
as for my decrypter, perhaps read further on the thread you first found it on, and you will see that because security researchers releasing information, my decrypter gor patched with v2. Had you had the first one (which is no longer used) it would have been able to help you.





