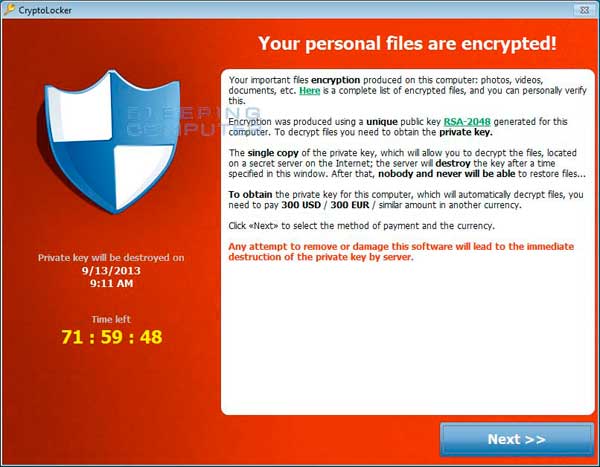
As was discovered back in September 2013, the main distribution method for CryptoLocker were ZBOT executables disguised as PDF files being mass emailed to company email addresses. These emails pretended to be from tax companies, Fedex, UPS, Xerox, and other business related organizations. Once a ZBOT attachment was opened, ZBOT would be installed and would eventually download and install CryptoLocker on the infected machine.
All in all, there is no doubt that this was a hugely successful operation and one that benefits everyone who uses a computer, but is it really the end of CryptoLocker? Furthermore, are the creators of the Zeus Botnet and CryptoLocker one and the same? What we do know is that McAfee, one of the companies involved with the takedown, prematurely posted a blog post about Operation Tovar before it was officially announced. This blog post was only public for a brief period before it was taken down. Unfortunately, it may have been enough time to let the Gameover or CryptoLocker developers know what was going on as the CryptoLocker Decryption Service page was replaced with a simple message. "stupid mcafee
 ". Unfortunately, this page is no longer accessible and showing a "Bad Gateway" message.
". Unfortunately, this page is no longer accessible and showing a "Bad Gateway" message.For now, more information about Operation Tovar can be found in the official United States Department of Justice complaint, their press release, and other court documents regarding Operation Tovar.




 Back to top
Back to top