Table of Contents
- How to get help with CryptorBit
- What is CryptorBit or the HowDecrypt Ransomware
- How to recover files encrypted by CryptorBit
- How to restore files encrypted by CryptorBit using Shadow Volume Copies
- How to fix files encrypted by CryptorBit using DecrypterFixer's Tools
- Information about the Malware Developer's CryptorBit Decryptor Site
- Known Bitcoin Payment addresses for CryptorBit
- How to prevent your computer from becoming infected by CryptorBit
- How to allow specific applications to run when using Software Restriction Policies
How to get help with CryptorBit
BleepingComputer.com was one of the first support sites to have reports of the CryptorBit, or HowDecrypt, ransomware. At the time, though, we were unable to help as this infection has been incredibly elusive and any supposed samples would not work. Recently, a member known as DecrypterFixer, has been able to recover some files that were supposedly encrypted by this malware. Due to our ability to now help users with this infection we have put together a guide that contains all known information about the CryptorBit infection.
All of this information has been compiled from reports by victims and consultants who contributed to our over 31 page CryptorBit support topic. Big thanks to everyone who contributed, especially DecrypterFixer, Piglet 65, Dalicar, Cody Johnston, and Happy Heretic for their assistance in working on the repair process. This guide will continue to be updated as new information or approaches are gathered. If you have anything that you think should be added, clarified, or revised please let us know in the support topic linked to below.
What is CryptorBit or the HowDecrypt Ransomware
CryptorBit is a ransomware program that was released around the beginning of December 2013 that targets all versions of Windows including Windows XP, Windows Vista, Windows 7, and Windows 8. When infected, this ransomware will scan your computer and encrypt any data file it finds regardless of the file type or extension. When it encrypts a file, it will also create a HowDecrypt.txt file and a HowDecrypt.gif in every folder that a file was encrypted. The GIF and TXT files will contain instructions on how to access a payment site that can be used to send in the ransom. This payment site is located on the Tor network and you can only make the payment in Bitcoins.
When CryptorBit modifies your files it is actually not encrypting the entire file, but rather corrupting it by replacing the first 512 bytes of the file. What it appears to be doing is copying the first 512 bytes of the file's original file header, encrypting those bytes, and storing them at the end of the file. It will then create a different 512 byte header and replace the file's normal header with it. This effectively corrupts the file because a program that would normally open this type of file would see an unknown header and not be able to open it. The good news is that a technique has been found that can repair the file's header and thus allow you to recover your corrupted files.
As for the registry and file paths this infection is using, not much is known at this time. We have not been able to acquire a working dropper or samples that will run and thus can't give definitive information on what files and registry entries it creates. What we do know is that it will create random files and folders under the %AppData%, %LocalAppData%, or %ProgramData% system folders. It will also create HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run and HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce entries to start the infection when Windows starts.
Another component that is commonly bundled with CryptorBit is a cryptocoin miner. This component will utilize your computer's CPU to mine digital coins, such as Bitcoin or other coins, for the malware developer that will then be deposited into their wallet. This generates further revenue for the malware developer.
Unfortunately, no dropper for this infection has been actively seen in the wild at this time. Victim's reports indicate that their files had become corrupted right after installing a fake Flash update or being infected by a rogue anti-virus program of some sort. At this time, none of these reports have been corroborated.
If you find that you are infected with CryptorBit it is suggested that you automatically scan your computer with an antivirus or antimalware program. We have seen that many antivirus vendors are able to detect the infection files and clean them. As these files are widely detected by AV programs, it has been discussed that this infection may actually be installed remotely by someone hacking into a server or computer. This would allow them to disable any AV programs, install the encrypter, encrypt your files, and then clean up the installer. This would also explain why no one has been able to find the installer for this infection. With that said, make sure you change your passwords on your computer and if you use remote desktop, please consider changing your remote desktop port as described in the following tutorial:
How to recover files encrypted by CryptorBit
The first method is to try and restore your files from a backup. If a backup is unavailable, then you should attempt to restore your files from Shadow Volume Copies. Windows XP Service Pack 2 and higher utilize a feature called Shadow Volume Copies that, if enabled, automatically create backup copies of some your data files for you. For more information on how to restore files via the Shadow Volume Copies, please see this section of the guide:
How to restore files encrypted by CryptorBit using Shadow Volume Copies
If a backup does not exist and you are unable to restore from the Shadow Volume Copies, then there is still good news! A BleepingComputer.com member named Nathan Scott, aka DecrypterFixer, has come up with a program that will allow you to recover JPG, PST, MP3, PDF, .DOC, .XLS, .XLSX, .PPTX, .and DOCX documents that have been encrypted by CryptorBit. To use DecrypterFixer's tools, please use the link below:
How to fix files encrypted by CryptorBit using DecrypterFixer's Tools
How to restore files encrypted by CryptorBit using Shadow Volume Copies
If you had System Restore enabled on the computer, Windows creates shadow copy snapshots that contain copies of your files from that point of time when the system restore snapshot was created. These snapshots may allow us to restore a previous version of our files from before they had been encrypted. This method is not fool proof, though, as even though these files may not be encrypted they also may not be the latest version of the file. Please note that Shadow Volume Copies are only available with Windows XP Service Pack 2, Windows Vista, Windows 7, & Windows 8.
In this section we provide two methods that you can use to restore files and folders from the Shadow Volume Copy. The first method is to use native Windows features and the second method is to use a program called ShadowExplorer. It does not hurt to try both and see which methods work better for you.
Using native Windows Previous Versions:
To restore individual files you can right-click on the file, go into Properties, and select the Previous Versions tab. This tab will list all copies of the file that have been stored in a Shadow Volume Copy and the date they were backed up as shown in the image below.
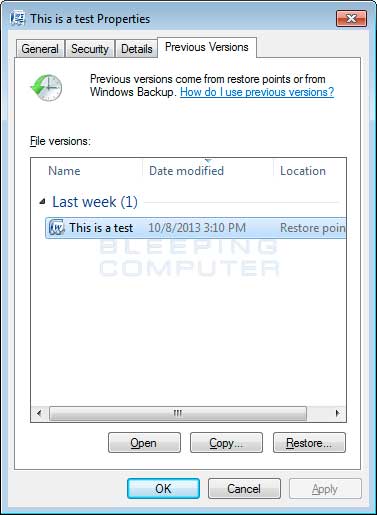
To restore a particular version of the file, simply click on the Copy button and then select the directory you wish to restore the file to. If you wish to restore the selected file and replace the existing one, click on the Restore button. If you wish to view the contents of the actual file, you can click on the Open button to see the contents of the file before you restore it.
This same method can be used to restore an entire folder. Simply right-click on the folder and select Properties and then the Previous Versions tabs. You will then be presented with a similar screen as above where you can either Copy the selected backup of the folder to a new location or Restore it over the existing folder.
Using ShadowExplorer:
You can also use a program called ShadowExplorer to restore entire folders at once. When downloading the program, you can either use the full install download or the portable version as both perform the same functionality.
When you start the program you will be shown a screen listing all the drives and the dates that a shadow copy was created. Select the drive (blue arrow) and date (red arrow) that you wish to restore from. This is shown in the image below.
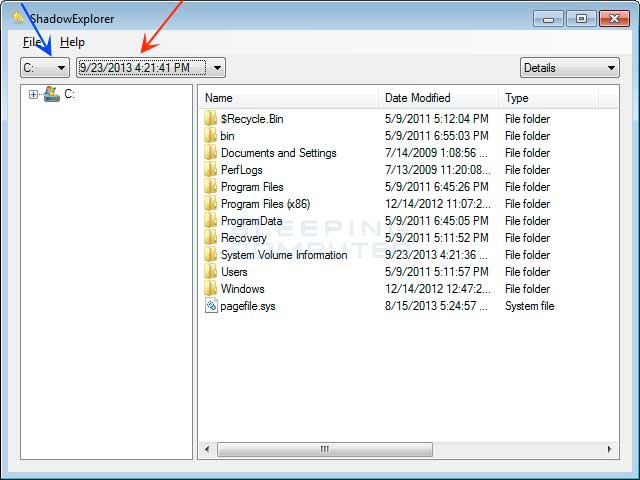
To restore a whole folder, right-click on a folder name and select Export. You will then be prompted as to where you would like to restore the contents of the folder to.
How to fix files encrypted by CryptorBit using DecrypterFixer's Tools
Nathan Scott, aka DecrypterFixer, has developed tools that can fix various types of files that have been encrypted by CryptorBit. Currently his tools can recover corrupted PST, JPG, PDF, MP3, DOC, and XLS files. In order to use his tool you must have Microsoft Net Framework 4.0 or higher installed on your computer. If you using Windows XP, you will need to have service pack 3 installed before you can install Net 4.0. If you find that his tools have helped you recover your files, please feel free to send him a tip using one of the methods below:
To recover JPEG/JPG, .PDF, .WAV, .PST, .DOC, .XLS, .XLSX, .PPTX, .DOCX, and .MP3 files, you need to download Anti-CryptorBit.exe from the following links.
http://download.bleepingcomputer.com/cryptorbit/Anti-CryptorBitV2.zip (ZIP)
Once the file has been downloaded, extract the zip file, and run the Anti-CryptorBit.exe program. This will open the main dashboard for Anti-CryptorBit as shown below.

Simply click on the recovery method that you wish to run and follow the instructions. If you need any help with Anti-CryptorBit please post your questions in the CryptorBit support topic.
Information about the Malware Developer's CryptorBit Decryptor Site
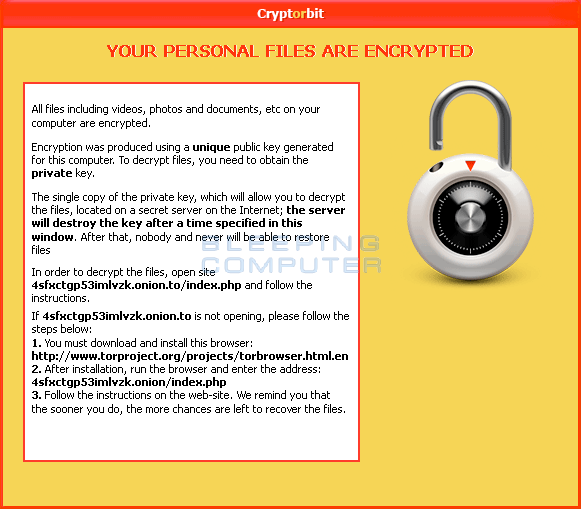
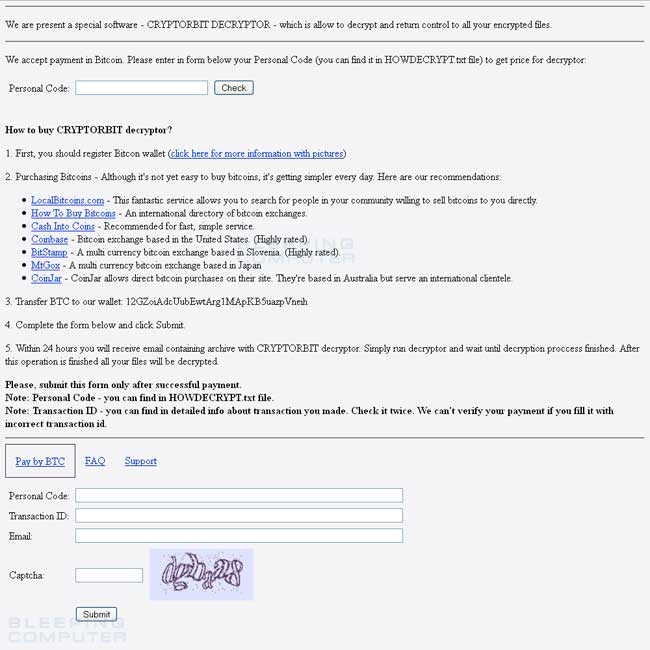
When you are infected with CryptorBit, the infection will create HowDecrypt.txt and HowDecrypt.gif files that contain information on how to pay the ransom. Below is the contents of the HowDecrypt.txt and HowDecrypt.gif messages:
HowDecrypt.txt:
HowDecrypt.gif
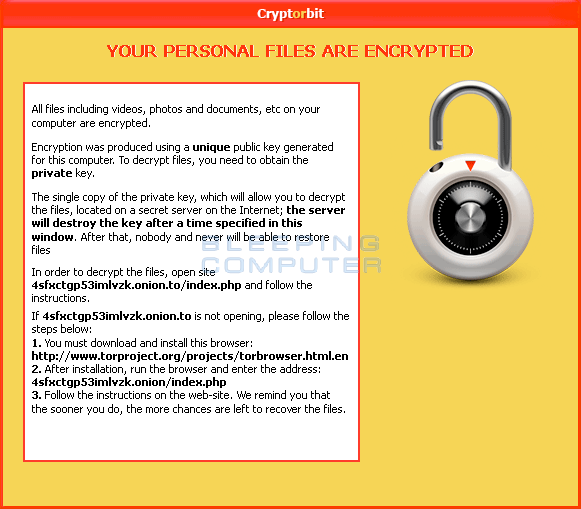
The instructions tell the victim that in order to pay the ransom they need to install a special program called Tor. Once Tor is installed they can use it to access their hidden web site at the TOR address 4sfxctgp53imlvzk.onion. When a user visits that address using the Tor browser they will be shown a page that gives instructions on how to pay Bitcoins in order to receive a CryptorBit decryptor. The current cost for the decryptor as of 02/13/2014 is .6 BTC.
Click on the image above to see full size and other associated images.
In order to submit the payment you will need to first enter the Personal Code from your HowDecrypt.txt files. The site will report back how many bitcoins you need to send as your ransom payment. Once you send the bitcoins to the requested address and fill in the rest of the information, you will supposedly be sent a CryptorBit Decryptor program. I have no first-hand knowledge of anyone paying the ransom and have not seen the decryptor. Based on the payments sent to known CryptorBit Bitcoin addresses, though, quite a few people appear to have paid the ransom.
Previous CryptorBit Decryptor Purchase page screenshots:
| Date | Link to Image |
|---|---|
| 12/12/13 | https://www.bleepstatic.com/swr-guides/c/cryptorbit/tor-decryption-service-old.png |
Known Bitcoin Payment addresses for CryptorBit
CryptorBit allows you to pay the ransom by sending bitcoins to an address shown in the CryptorBit Decryptor Purchase page. Bitcoins are currently worth over $600 USD on some bitcoins exchanges. CryptorBit has used different bitcoin payment addresses for those who were infected. Some of these addresses are below:
https://blockchain.info/address/15JTKDkU4U6Tn5MBc9Pt52mMzXDmvmaanR
https://blockchain.info/address/12GZoiAdcUubEwtArg1MApKB5uazpVneih
https://blockchain.info/address/1CgMiXHjLFUM3E79USnVM5Sikf5j9gTdXy
https://blockchain.info/address/17FSkXDULjtK6R9G3cpwmLMYbWRZJ9c8vZ
You can use the links above to see transactions into the wallet and out of the wallet. You can typically tell which payments to this address are from ransom victims as there will be many payments with the same amount.
How to prevent your computer from becoming infected by CryptorBit
You can use the Windows Group or Local Policy Editor to create Software Restriction Policies that block executables from running when they are located in specific paths. For more information on how to configure Software Restriction Policies, please see these articles from MS:
http://support.microsoft.com/kb/310791
http://technet.microsoft.com/en-us/library/cc786941(v=ws.10).aspx
The file paths that have been used by this infection and its droppers are:
C:\<random>\<random>.exe
C:\Users\<User>\AppData\Local\<random>.exe (Vista/7/8)
C:\Users\<User>\AppData\Local\<random>.exe (Vista/7/8)
C:\Documents and Settings\<User>\Application Data\<random>.exe (XP)
C:\Documents and Settings\<User>\Local Application Data\<random>.exe (XP)
%Temp%
In order to block the CryptorBit you want to create Path Rules so that they are not allowed to execute. To create these Software Restriction Policies, you can either use the CryptoPrevent tool or add the policies manually using the Local Security Policy Editor or the Group Policy Editor. Both methods are described below.
How to use the CryptoPrevent Tool:
FoolishIT LLC was kind enough to create a free utility called CryptoPrevent that automatically adds the suggested Software Restriction Policy Path Rules listed above to your computer. This makes it very easy for anyone using Windows XP SP 2 and above to quickly add the Software Restriction Policies to your computer in order to prevent CryptorBit and Zbot from being executed in the first place. This tool is also able to set these policies in all versions of Windows, including the Home versions.
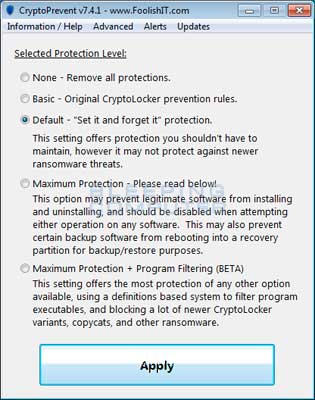
A new feature of CryptoPrevent is the option to whitelist any existing programs in %AppData% or %LocalAppData%. This is a useful feature as it will make sure the restrictions that are put in place do not affect legitimate applications that are already installed on your computer. To use this feature make sure you check the option labeled Whitelist EXEs already located in %appdata% / %localappdata% before you press the Block button.
You can download CryptoPrevent from the following page:
For more information on how to use the tool, please see this page:
Once you run the program, simply click on the Apply Protection button to add the default Software Restriction Policies to your computer. If you wish to customize the settings, then please review the checkboxes and change them as necessary. If CryptoPrevent causes issues running legitimate applications, then please see this section on how to enable specific applications. You can also remove the Software Restriction Policies that were added by clicking on the Undo button.
How to manually create Software Restriction Policies to block CryptorBit:
In order to manually create the Software Restriction Policies you need to be using Windows Professional or Windows Server. If you want to set these policies for a particular computer you can use the Local Security Policy Editor. If you wish to set these policies for the entire domain, then you need to use the Group Policy Editor. Unfortunately, if you are a Windows Home user, the Local Policy Editor ir not available and you should use the CryptoPrevent tool instead to set these policies. To open the Local Security Policy editor, click on the Start button and type Local Security Policy and select the search result that appears. You can open the Group Policy Editor by typing Group Policy instead. In this guide we will use the Local Security Policy Editor in our examples.
Once you open the Local Security Policy Editor, you will see a screen similar to the one below.
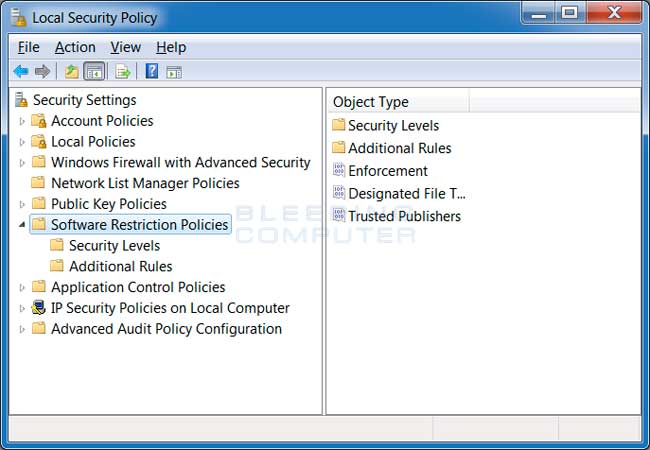
Once the above screen is open, expand Security Settings and then click on the Software Restriction Policies section. If you do not see the items in the right pane as shown above, you will need to add a new policy. To do this click on the Action button and select New Software Restriction Policies. This will then enable the policy and the right pane will appear as in the image above. You should then click on the Additional Rules category and then right-click in the right pane and select New Path Rule.... You should then add a Path Rule for each of the items listed below.
If the Software Restriction Policies cause issues when trying to run legitimate applications, you should see this section on how to enable specific applications.
Below are a few Path Rules that are suggested you use to not only block the infections from running, but also to block attachments from being executed when opened in an e-mail client.
Block CryptorBit executable in %AppData%
Path: %AppData%\*.exe
Security Level: Disallowed
Description: Don't allow executables to run from %AppData%.Block CryptorBit executable in %LocalAppData%
Path if using Windows XP: %UserProfile%\Local Settings\*.exe
Path if using Windows Vista/7/8: %LocalAppData%\*.exe
Security Level: Disallowed
Description: Don't allow executables to run from %AppData%.Block Zbot executable in %AppData%
Path: %AppData%\*\*.exe
Security Level: Disallowed
Description: Don't allow executables to run from immediate subfolders of %AppData%.Block Zbot executable in %LocalAppData%
Path if using Windows XP: %UserProfile%\Local Settings\*\*.exe
Path if using Windows Vista/7/8: %LocalAppData%\*\*.exe
Security Level: Disallowed
Description: Don't allow executables to run from immediate subfolders of %AppData%.Block executables run from archive attachments opened with WinRAR:
Path if using Windows XP: %UserProfile%\Local Settings\Temp\Rar*\*.exe
Path if using Windows Vista/7/8: %LocalAppData%\Temp\Rar*\*.exe
Security Level: Disallowed
Description: Block executables run from archive attachments opened with WinRAR.Block executables run from archive attachments opened with 7zip:
Path if using Windows XP: %UserProfile%\Local Settings\Temp\7z*\*.exe
Path if using Windows Vista/7/8: %LocalAppData%\Temp\7z*\*.exe
Security Level: Disallowed
Description: Block executables run from archive attachments opened with 7zip.Block executables run from archive attachments opened with WinZip:
Path if using Windows XP: %UserProfile%\Local Settings\Temp\wz*\*.exe
Path if using Windows Vista/7/8: %LocalAppData%\Temp\wz*\*.exe
Security Level: Disallowed
Description: Block executables run from archive attachments opened with WinZip.Block executables run from archive attachments opened using Windows built-in Zip support:
Path if using Windows XP: %UserProfile%\Local Settings\Temp\*.zip\*.exe
Path if using Windows Vista/7/8: %LocalAppData%\Temp\*.zip\*.exe
Security Level: Disallowed
Description: Block executables run from archive attachments opened using Windows built-in Zip support.
You can see an event log entry and alert showing an executable being blocked:
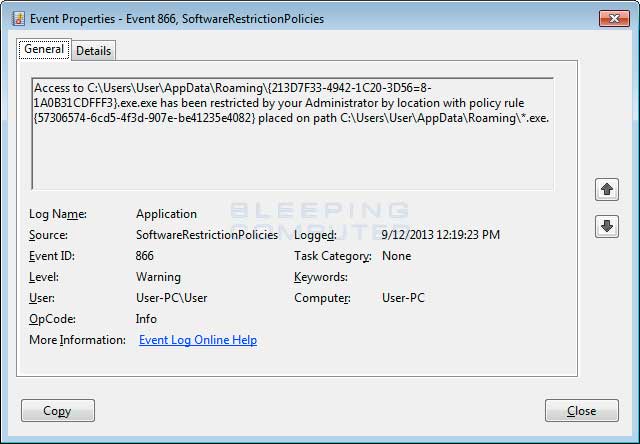
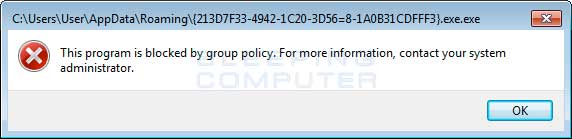
If you need help configuring this, feel free to ask in the CryptorBit help topic.
How to allow specific applications to run when using Software Restriction Policies
If you use Software Restriction Policies, or CryptoPrevent, to block CryptorBit you may find that some legitimate applications no longer run. This is because some companies mistakenly install their applications under a user's profile rather than in the Program Files folder where they belong. Due to this, the Software Restriction Policies will prevent those applications from running.
Thankfully, when Microsoft designed Software Restriction Policies they made it so a Path Rule that specifies a program is allowed to run overrides any path rules that may block it. Therefore, if a Software Restriction Policy is blocking a legitimate program, you will need to use the manual steps given above to add a Path Rule that allows the program to run. To do this you will need to create a Path Rule for a particular program's executable and set the Security Level to Unrestricted instead of Disallowed as shown in the image below.
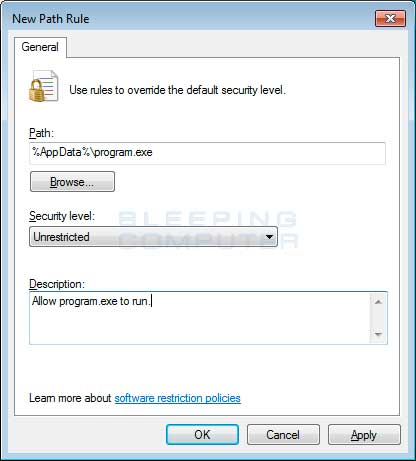
Once you add these Unrestricted Path Rules, the specified applications will be allowed to run again.