
4/30/24: Update added below about Change Healthcare Citrix credentials previously stolen by information-stealing malware.
UnitedHealth confirms that Change Healthcare's network was breached by the BlackCat ransomware gang, who used stolen credentials to log into the company's Citrix remote access service, which did not have multi-factor authentication enabled.
This was revealed in UnitedHealth CEO Andrew Witty's written testimony published ahead of a House Energy and Commerce subcommittee hearing scheduled for tomorrow.
The ransomware attack on Change Healthcare occurred in late February 2024, leading to severe operational disruptions on Optum's Change Healthcare platform.
This impacted a wide range of critical services used by healthcare providers across the U.S., including payment processing, prescription writing, and insurance claims, and caused financial damages estimated at $872 million.
Previously, the BlackCat ransomware gang claimed they had received a $22 million ransom payment from UnitedHealth, which was stolen from the affiliate who conducted the attack in an exit scam. Shortly after, the affiliate claimed to still have the data and partnered with RansomHub to initiate an additional extortion demand by leaking stolen data.
The healthcare org recently admitted that it paid a ransom to protect people's data post-compromise, but no details about the attack or who carried it out were officially disclosed.
RansomHub has since removed the Change Healthcare entry from its site, indicating that an additional ransom was paid.
An easy break-in
In testimony by Andrew Witty, the CEO confirmed that the attack occurred on the morning of February 21 when the threat actors began encrypting systems and rendering them inaccessible to the organization's employees.
For the first time, the company also officially confirmed BleepingComputer's report that the ALPHV/BlackCat ransomware operation was behind the attack.
While the actual public-facing attack occurred on February 21, Witty revealed that the attacker had access to the company's network for approximately ten days before deploying their encryptors. During this time, the threat actors spread through the network and stole corporate and patient data that would be used in their extortion attempts.
The investigations, which are still ongoing, revealed that the attackers first gained access to Change Healthcare's Citrix portal on February 12, 2024, using stolen employee credentials. It is unknown whether those credentials were initially stolen via a phishing attack or information-stealing malware.
"On February 12, criminals used compromised credentials to remotely access a Change Healthcare Citrix portal, an application used to enable remote access to desktops," explained Witty.
"The portal did not have multi-factor authentication. Once the threat actor gained access, they moved laterally within the systems in more sophisticated ways and exfiltrated data. Ransomware was deployed nine days later."
The CEO also shared a personal moment, stating that the choice to pay a ransom was entirely his and one of the hardest decisions he had to make.
"As chief executive officer, the decision to pay a ransom was mine. This was one of the hardest decisions I've ever had to make. And I wouldn't wish it on anyone," Witty wrote in his testimony.
Remediation efforts
Witty further outlined their immediate actions to secure their systems following the attack, characterizing them as "swift and forceful," noting that the threat was successfully contained by taking everything down despite knowing the impact this would have on people.
Following the attack, the organization's IT team replaced thousands of laptops, rotated credentials, and completely rebuilt Change Healthcare's data center network and core services in just a few weeks. Witty states such a task would usually have taken several months.
Although data samples that leaked online contained protected health information (PHI) and personally identifiable information (PII), Witty notes that, so far, they have seen no evidence of exfiltration of materials such as doctors' charts or complete medical histories.
Concerning the status of the impacted services, pharmacy networks operate at a fraction of a percent below normal, medical claims flow nearly at normal levels, and payment processing at approximately 86% of pre-incident levels.
Update 4/30/24: After publishing our story, Hudson Rock CTO Alon Gal told BleepingComputer that on February 8 the company's threat intelligence platform detected a Change Healthcare employee's Citrix credentials stolen through information-stealing malware.
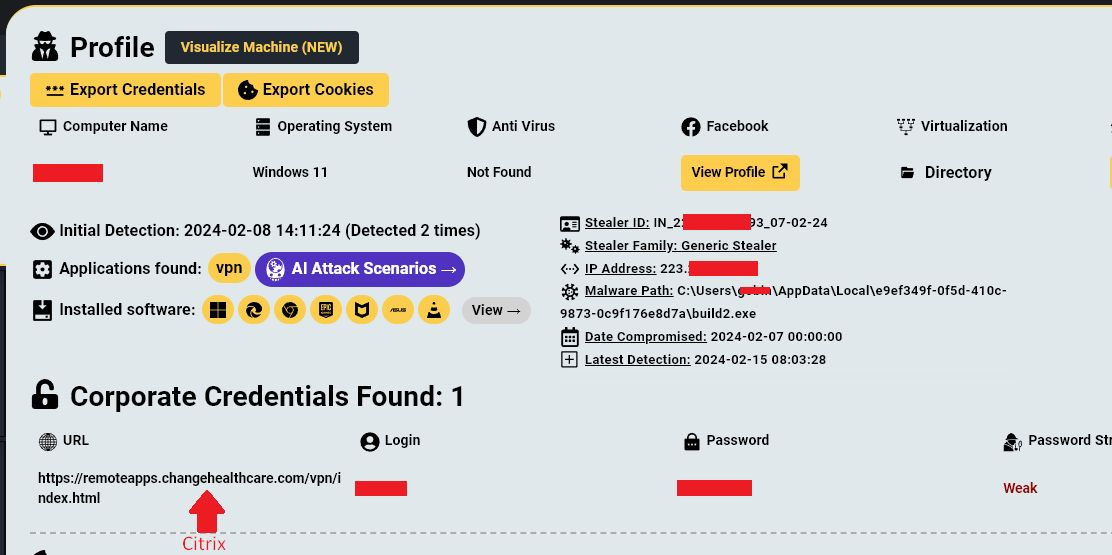
Source: Hudson Rock
The stolen credentials are associated with the URL remoteapps[.]changehealthcare[.]com/vpn/index.htm, and while that site is no longer accessible, BleepingComputer has confirmed it to be the URL for Change Healthcare's Citrix Gateway login page.
It is unknown if these are the credentials used to gain access to Change Healthcare's networks and conduct the ransomware attack.



Comments
Mahhn - 2 months ago
I hope UHG has to pay billions in fines. I have a "very" bad opinion of them.
powerspork - 2 months ago
I hope they saved $872 million not deploying MFA on a public service. MFA sure can be pricey at a few dollars, or free, depending on implementation.
Network_Dude - 2 months ago
This is utter incompetence. This would be negligence for a small business to open a publicly accessible Citrix portal without MFA, let alone a large corporation like this.
There needs to be some type of accountability for this type of thing.
Lefty4444 - 1 month ago
How long have lack of MFA been a way in for threat actors?
When I started as a junior sysadmin 2000 it was. Now it's 2024 and it still is.