Web applications are able to protect your Web assets from attack – especially websites. Discover the best Web application firewalls, as we explore the market and recommend our top choices.
Websites and other Web applications communicate with the outside world. They can form a point of entry or an opportunity for mischief for hackers. If you make an asset accessible to everyone, you need to control what people can do with it. Web application firewalls (WAF) protect these systems.
Here is our list of the best Web application firewalls:
- Imperva Web Application Firewall: This Web application protection system can be integrated into the Imperva content delivery network.
- Azure Web Application Firewall: This cloud-based system is a proxy service that protects Web servers both on your premises and on the cloud.
- Indusface AppTrana Web Application Firewall: This is a hosted edge service that is combined with other proxy systems, such as a content delivery network and DDoS protection.
- Barracuda Web Application Firewall: This package has a lot of deployment options, and it includes a reverse firewall for data loss prevention.
- Cloudflare WAF: is A very popular package that includes DDoS protection, a global threat intelligence network, and caching for fast page delivery.
- Akamai App and API Protection: This WAAP provides malware blocking and DDoS protection from one of the leading cybersecurity brands.
How are websites attacked?
A website is a bunch of code that is sent out on request. Most of the traffic in an exchange during a Web page visit is mostly in the direction from the server to the browser. Some traffic travels in the other direction and that provides hackers with an opportunity.
Conceptually, it isn’t true to say that a website gets attacked. In fact, in every case, the Web server is the target. The exchange of messages that occur between a Web server and a visitor’s Web browser provides a path to transport malicious code to the Web server.
Many sites include forms that enable visitors to enter data. These provide a gateway for hackers to get into a target company’s system, trap the data of other visitors, or piggyback malicious code on the website for delivery to others.
A hacking attack doesn’t even need to load up the website into a browser; exchanges can be implemented programmatically. Several well-known attack strategies can be launched against Web servers. With several attack methods, the website becomes a delivery method to infect third-party computers with malware.
Typical and unusual attacks
WAFs are written to defend against a series of known attack strategies. These are detailed by the Open Web Application Security Project (OWASP) in the famous OWASP Top Ten. OWASP calls these well-known techniques Common Weakness Enumerations (CWEs).
The types of attacks that can occur include cross-site scripting and other code injection techniques. These insert malicious scripts into the package of code that will be delivered to every visitor requesting the infected page. Hackers can attach fileless malware to a Web page, which will download into the memory of a visitor’s computer.
Other well-known malicious acts that can be implemented against websites include password cracking, encryption cracking, DDoS attacks, and database credentials probing. Hackers have a suite of familiar software that they use to look for opportunities for these attacks and to implement them. Cybersecurity software includes standard routines to block them. Your WAF should at least detect and stop these types of attacks.
There are many hackers in the world and once in a while, one of them will come up with a new idea on how to break into or damage a publicly accessible IT system, such as a Web server. This is going to be a variation on one of the CWEs, a discovered vulnerability in a piece of Web server software, or a flaw in a connection technology or a Web development framework. As these attacks have never been seen by cybersecurity software, they are called zero-day attacks.
The producers of software systems that contain weaknesses will soon find out about them and produce a patch to close down the exploit. However, the zero-day attack will run successfully against several systems before the world’s cybersecurity researchers notice it.
Only a few systems in the world will be hit by a new zero-day attack before it is blocked, you don’t want your Web applications to be among them. So, you need a WAF that can spot and block zero-day attacks as well as CWEs.
The best Web application firewalls
The attacks on Web applications are sometimes targeted but are usually the product of sweeps across the Web by automated reconnaissance systems that look for weaknesses. It isn’t just controversial websites or disliked corporations that get hit. So, you can’t assume that your site is too nice or harmless to be attacked; every site could be attacked at any time. So, every Web server needs the protection of a Web application firewall.
Our methodology for selecting a Web application firewall
We reviewed the market for Web application firewalls and assessed them with the following selection criteria:
- Protection against traffic floods
- Identification of brute force attacks for password or encryption cracking
- A proxy server that receives all incoming traffic and scans it for threats
- A discovery logging service to record attack attempts
- Analysis for attacks underway
- Historical analysis of previous attacks
- A free trial or a demo to enable an assessment before buying
- Value for money from a package that is sold at an appropriate price given the services that are on offer
With these selection criteria, we looked for Web application firewalls that include solutions for all sizes of businesses. The majority of these systems are delivered as cloud platforms but some are available as network appliances that pre-filter traffic before it arrives at any other network equipment. These are known as edge services.
1. Imperva Web Application Firewall
Imperva Web Application Firewall is available as a cloud-based SaaS platform or as a network appliance. It is also possible to get the software and set up a virtual appliance on your site or an AWS, Azure, or GCP account. In all deployment options, the expectation is that the unit will catch all traffic before it gets to the network. This is an edge service.
Key features:
- Stands between the Web server and the outside world: No traffic gets to the Web server directly
- Provides a failover service: Maintains a copy of all files held on the Web server
- Protects Web applications and APIs: This is a WAAP
- DevOps protection: Secures applications under development as well as live systems
Why do we recommend it?
Imperva Web Application Firewall filters traffic on the way into your Web server and it provides a virtual patching service that makes up for discovered weaknesses in the Web server system and the software and files that it holds. The server also absorbs DDoS attacks and blocks bot activity.
Imperva offers a content delivery network and subscribers to the SaaS platform version of the Web Application Firewall can combine the service with that system to improve delivery as well as protect Web applications. Naturally, as the CDN alters DNS records to catch your traffic, it prevents any request from getting to your Web server.
Who is it recommended for?
This service’s different configurations will appeal to different types of businesses. For example, companies that develop Web applications will get more control from the on-premises options, whereas companies that want to combine the service with the CDN package will be better off with the FWaaS option.
Pros:
- Scans Web assets for vulnerabilities: Implements virtual patching if an actual patch isn’t available
- Configuration improvements: Provides a more secure environment on its server than your Web server settings
- Delivery improvements: Makes your website more appealing by speeding up response times
- DDoS protection: Washes superfluous traffic
Cons:
- Addresses different audiences: The on-premises, cloud-platform software, and FWaaS options cater to different business activities
Imperva is a strong brand in the cybersecurity market and its combination of Web application security, traffic cleaning, and content delivery improvements provides value for money. However, the service is a little too pricey for small businesses. You can examine the service by accessing a demo.
2. Azure Web Application Firewall
Microsoft Azure offers a Web Application Firewall on its cloud platform. This system isn’t limited to protecting Web applications hosted on its own platform; it can protect applications hosted elsewhere, including on-premises. This service protects against the OWASP Top 10 attacks. It also lets you set up your own threat-scanning rules.
Key features:
- A proxy service: Receives all of your Web traffic and hides your own Web server’s real IP address
- API deployment: Enables security checks to be integrated into a development pipeline
- Real-time reporting: Events are shown in the dashboard
Why do we recommend it?
Microsoft Azure Web Application Firewall is a WAF offered on the Azure platform. The system is robust with continuous service guaranteed. The Web assets that this package offers do not need to be hosted on the Azure platform. The system offers out-of-the-box detection rules and you can also create your own.
This cloud-based system provides a new destination for all requests coming to your Web server. The tool alters all the DNS records for your websites so that Web browsers are directed to your Azure account to access your website instead of to your own server. This enables the WAF to filter all traffic and only pass through valid requests. As well as blocking malware and intruders, this strategy absorbs DDoS attacks.
Who is it recommended for?
Azure Web Application Firewall is a metered service with invoicing at the end of each month. This is unusual for SaaS packages because they usually demand an advanced payment – often for a whole year. So, many businesses will appreciate that there are no upfront costs to taking up the Azure WAF. There is no enrollment fee and you don’t need to purchase any hardware.
Pros:
- Integration with SIEM tools: Can send a live activity stream to a SIEM of your choice
- Compliance management: Complies with the requirements of PCI DSS
- DDoS protection: Absorbs all traffic flood attacks
Cons:
- The risk of runaway costs: If you don’t keep track of throughput over the month, you could get a nasty surprise when the invoice arrives
The charge rate for Azure Web Application Firewall is calculated as a combination of time and throughput. Azure gives all account holders 10 TB of data per month for free. That rises to 40 TB for accounts with high throughput. Azure provides some services for free and there is a 12-month free trial period for others. However, the Web Application Firewall is not included in either of these offers. Azure offers a $200 voucher to new customers.
3. Indusface AppTrana Web Application Firewall
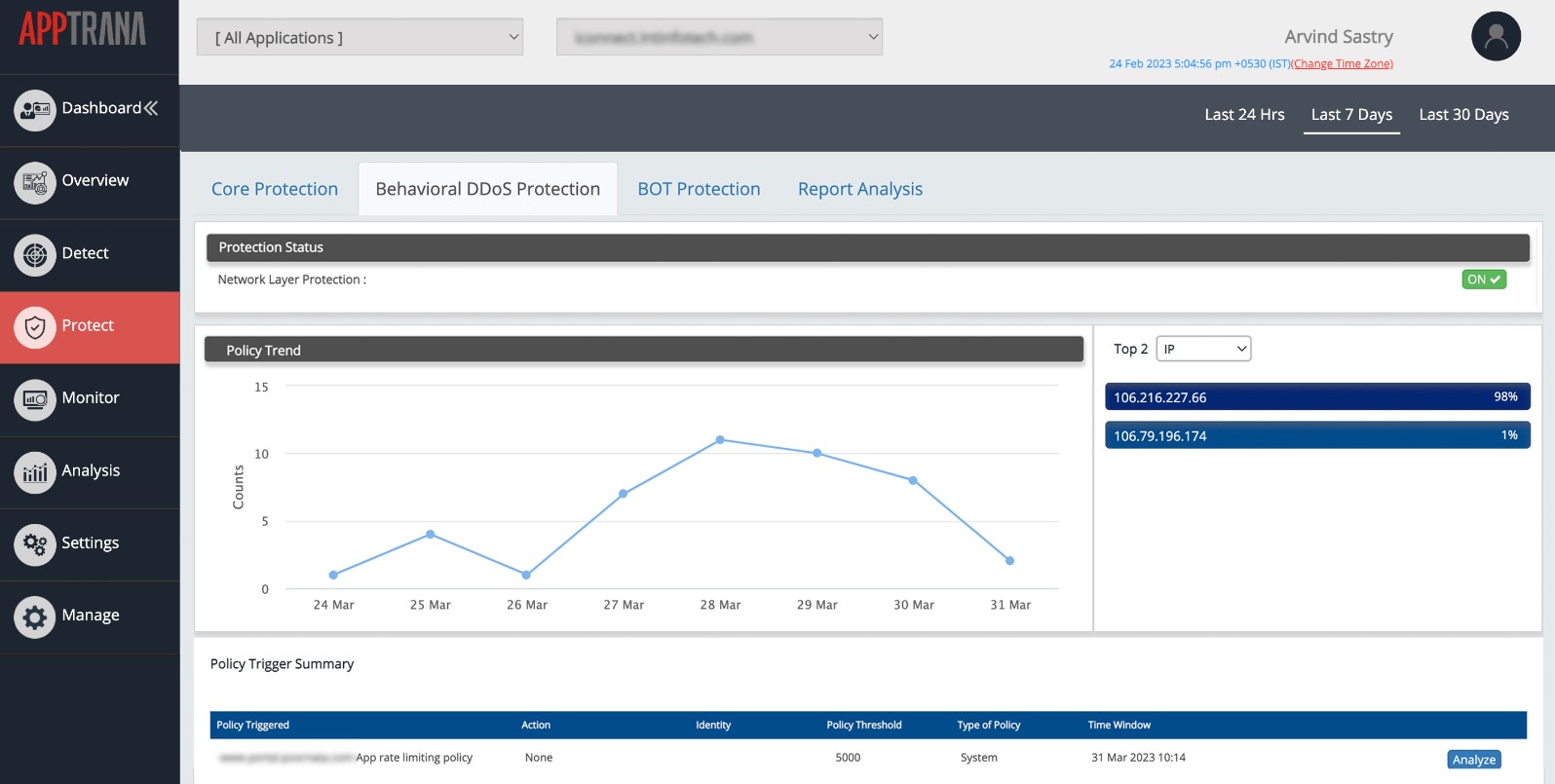
Indusface AppTrana is a package of edge services that are hosted on the cloud. The AppTrana package specifically protects Web applications and APIs. This combination of services is now known as WAAP, which stands for Web application and API protection. Many Web application firewalls on this list prefer to use the WAAP term instead of referring to their packages as WAFs.
Key features:
- A cloud-based system: This WAF is hosted on the cloud and mediates all communication with the outside world
- Combined services: Efficiency and value for money from multiple services sharing a traffic feed
- Content delivery network: Offers a failover service and speeds up delivery
- Virtual patching: Filters incoming traffic and adjusts responses to provide temporary cover for identified security weaknesses
- DDoS protection: Absorbs traffic flood attacks
Why do we recommend it?
Indusface AppTrana Web Application Firewall is part of an edge service package that receives all traffic on behalf of a website and filters out all harmful communications. The platform also provides assurance features, which include dynamic application security testing for vulnerability scanning and the services of a human penetration testing team to identify system weaknesses.
DDoS attacks can be expensive for the target because they require the rental of extra capacity to enable the full throughput of bogus connection requests to be absorbed. AppTrana will add on this emergency space for no extra cost. The package identifies other automated traffic such as crawling and indexing for reconnaissance or scraping for content theft.
The platform includes several preventative measures to fortify protected assets against attack. These are its DAST features that run APIs and access websites with all of their features to probe all possible permutations of inputs. This automated probe is explored further by a team of human penetration testers who will produce a guide on all the security weaknesses that were found and how to fix them.
The combination of system hardening and live traffic scanning should be enough to block all threats. The AppTrana package is in operation around the world and the team quickly spots new threats and updates its central threat intelligence database so that all of its customers are instantly protected against them.
Indusface AppTrana Web Application Firewall provides preventative scanning as well as live defense for Web applications and APIs. Delivered from the cloud as an edge service, the WAF processes all traffic going in and out of a Web server. The website’s DNS records are changed to direct browsers to the Indusface IP address. This hides the true location and IP address of the site, providing an extra layer of security. The site is still fully available to the general public. The package ensures constant availability and speeds up access through its content delivery network. Bots don’t get to your server; Indusface blocks DDoS attacks and other bot activity, such as scraping and crawling.
Who is it recommended for?
This package is suitable for any business that runs a website. There are two editions and the top plan, which includes the services of a penetration testing team, is pricey. The lower package, however, is much more accessible to mid-sized businesses. The package is perhaps a little out of reach for low-traffic small businesses.
Pros:
- No upfront costs: This is a subscription service with no enrollment fees
- Input from cybersecurity experts: The top package includes the services of a penetration testing team
- Free SSL certificate: Includes SSL certificate management
- Compliance management: For PCI DSS
- Hosted on AWS: Provides multi-region constant availability
Cons:
- Expensive: Out of the budgets of small businesses, however, you get industry-leading protection
Indusface offers two plan levels for its WAAP and there is also an API-only protection system available. You can get a 14-day free trial to assess the platform.
4. Barracuda Web Application Firewall

Barracuda Web Application Firewall is a network device and it is also available as a virtual appliance. Other deployment options include a Marketplace service on AWS, Azure, or GCP. Barracuda also offers its Web application protection system in a WAF-as-a-Service format.
Key features:
- Deployment options: Available as virtual or physical appliances, software for cloud accounts, or a SaaS package
- Malware blocking: Protects against the OWASP Top 10 and zero-day attacks
- Reverse firewall: Scans outgoing traffic for data theft attempts
Why do we recommend it?
Barracuda Web Application Firewall comes from one of the world’s leading network security brands. This tool is available in a SaaS version, which cuts down the cost of acquisition. The system will absorb DDoS attacks, block malware, identify intruders, and scan for data theft attempts. It can implement security policies that incorporate blacklisting and whitelisting.
The Barracuda service implements several traffic management functions as well as security protection. This is a load-balancing system that is ideal for businesses that expect very large volumes of traffic to a cluster of servers. Services also offer caching and traffic optimization for faster delivery.
Who is it recommended for?
The on-premises version of the Web application firewall acts as a traffic manager, distributing requests to a series of servers that can provide the same content. This means that the tool is suitable for very large companies that host their own sites or data centers. The virtual appliance and cloud options share a much wider market.
Pros:
- Traffic management: Checks incoming traffic and then assigns each request to an available server
- Deals with bot activity: Absorbs DDoS attacks and blocks scraping and probing by bots
- Compliance management: Functions can be tuned to comply with PCI DSS, FISMA, HIPAA, and SOX
Cons:
- The network device option is expensive: Smaller businesses should look at the virtual and cloud options
Barracuda offers its Firewall-as-a-Service option for the Web Application Server on a 30-day free trial.
5. Cloudflare WAF
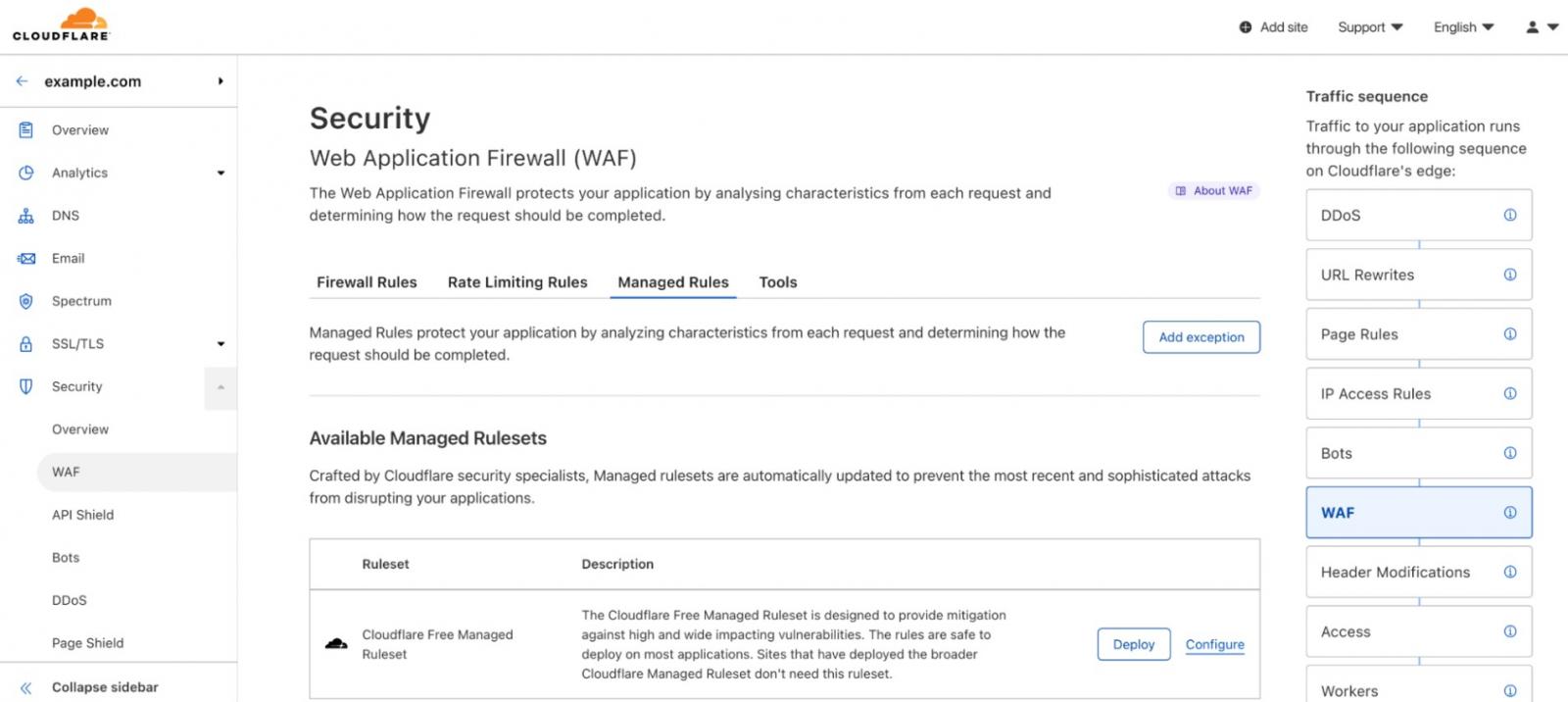
Cloudflare made its name through its DDoS protection system and has now expanded into a provider of edge services and Web application protection. The Cloudflare WAF is a core product of the company and is available for free to small businesses. The system protects the entire range of entities that operate a Web site from individuals starting a hobby website right up to multi-billion dollar multi-nationals.
Key features:
- Free plan: Suitable for small businesses
- SSL certificate included: Provides SSL management with expiry warnings
- Failover protection: This system never goes offline and has vast capacity
Why do we recommend it?
From its early days providing an innovative solution that blocks DDoS attacks and automated access attempts, Cloudflare has grown into a security service provider that serves more than 20 percent of the entire World Wide Web. Cloudflare uses its market dominance to offer low-cost and comprehensive packages that keep its market share expanding.
Cloudflare benefits from economies of scale to offer free services and very low prices. This service is provided as a proxy system with a large capacity that can absorb DDoS attacks of any size. The platform examines events for all clients and protects against a new attack as soon as it is launched against one of its many customers.
Who is it recommended for?
Cloudflare works with many Web hosting companies and offers its free plan to new signups. The most attractive offer of this package is its free SSL certificate. Many new website owners who sign up for the plan are attracted by the SSL cost saving and aren’t aware that they are also getting the WAF in with that certificate.
Pros:
- Pooled threat intelligence: An attack on one client is translated into protection for all
- Virtual patching: Guards for known software weaknesses where no patch is available
- Response time improvement: Caching resulting in faster delivery for the more popular Web assets
Cons:
- Not free for everyone: Plenty of low-throughput sites qualify for the free plan.
Check out the Cloudflare Free package for small websites or access a free trial of the Business Edition.
6. Akamai App and API Protector
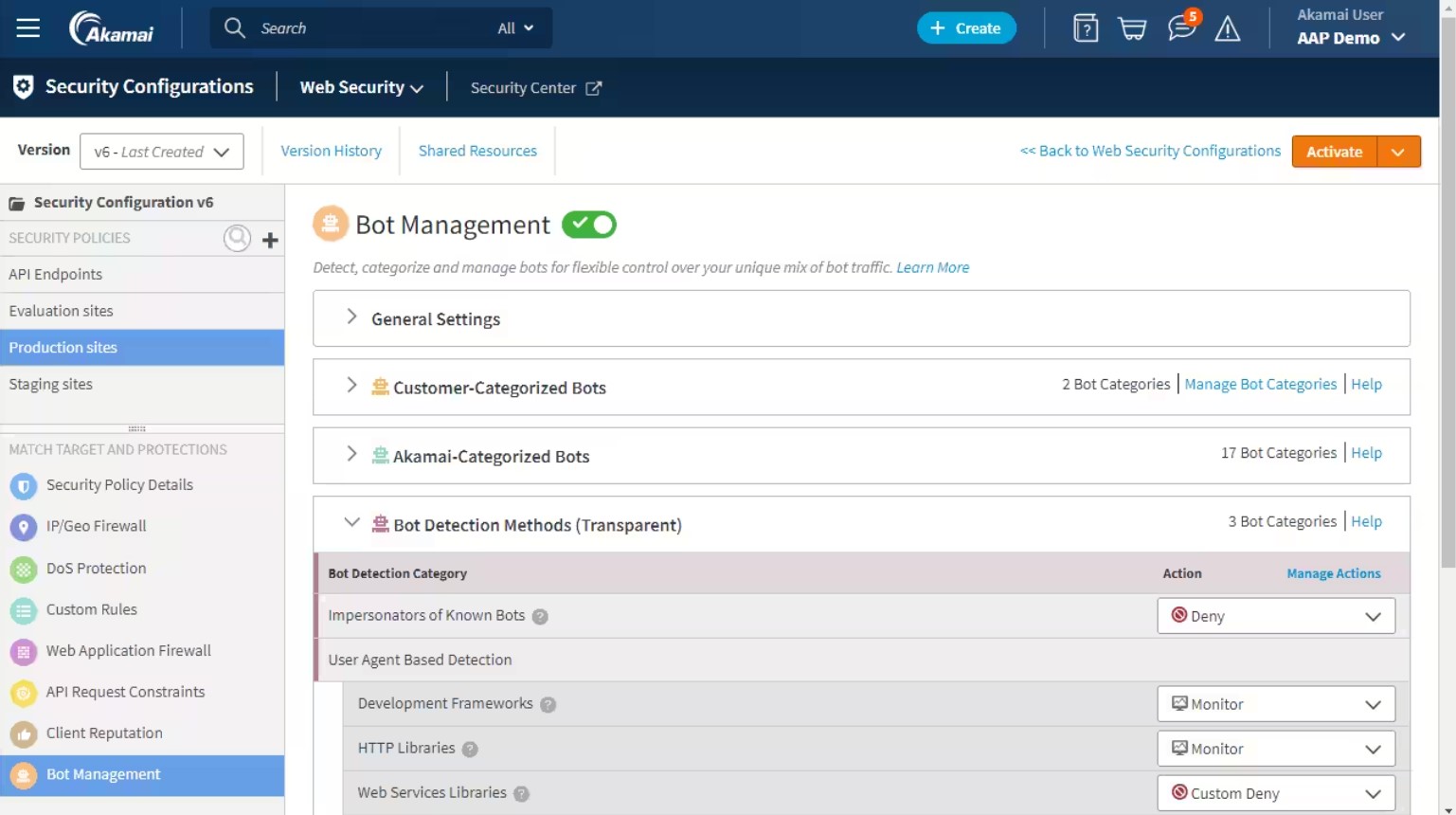
The Akamai App and API Protector protects against the OWASP Top 10 threats and also absorbs traffic attacks, such as DDoS floods. The tool can spot bot activity for probing and scraping and blocks it. This is a cloud-based system, so it operates as a proxy. In general, wthis package blocks all automated and manual attack strategies.
Key features:
- Bot defense: Blocks all types of bot activity, including DDoS attacks
- Threat intelligence: Akamai sifts through events from all its customers to spot new attack strategies
- Proxy service: Alters all your site’s DNS records to point to the Akamai server
Why do we recommend it?
Akamai App and API Protector is a proxy service, which means that no one ever learns the true IP address of your Web server. No one can get around the Akamai WAF and try to attack your Web server directly. As all traffic passes through Akamai’s server, the system filters out traffic floods, probing exercises, and malware.
Akamai is a leading brand and so it competes very well with Cloudflare. The App and API Protector has constant availability – it will never go down and block access to your website. This system can also be applied to application security testing for development.
Who is it recommended for?
The Akamai brand has equal prestige as the Cloudflare name. However, the company doesn’t stand a chance against Cloudflare in the startup and small business market because of Cloudflare’s association agreements with Web hosting services. Therefore, this is a good solution for mid-sized and large businesses.
Pros:
- DevOps protection: Suitable for development testing as well as live defense
- Live reporting: See attack notifications as they occur
- Historical analysis: Identify which of your assets are most attacked
Cons:
- No price list: No free forever plan
Get the Akamai App and API Protector on a 30-day free trial.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now