Cloudflare has fixed a critical vulnerability in its free and open-source CDNJS potentially impacting 12.7% of all websites on the internet.
CDNJS serves millions of websites with over 4,000 JavaScript and CSS libraries stored publicly on GitHub, making it the second-largest JavaScript CDN.
The vulnerability exploits comprised publishing packages to Cloudflare's CDNJS using GitHub and npm, to trigger a Path Traversal vulnerability, and eventually remote code execution.
If exploited, the vulnerability would lead to a complete compromise of CDNJS infrastructure.
From "ZIP Slip" to remote code execution
This week, security researcher RyotaK explains how he was able to find a method to completely compromise Cloudflare's CDNJS network while researching supply-chain attacks.
Content delivery networks (CDNs) perform a critical role in upholding the security, integrity, and availability of the Internet as a vast majority of websites rely on these services to load popular JavaScript libraries and CSS scripts.
CDNs can become a choice of targets for adversaries as, if compromised, the attack can have far-reaching consequences for many websites, online stores, and their customers.
While glancing over cdnjs.com, RyotaK noticed that for libraries that did not yet exist in CDNJS, he could suggest the addition of a new library via CDNJS' GitHub repository.
After exploring this GitHub repository and the adjacent ones that together make the CDNJS ecosystem work, RyotaK figured a way to trick the servers into executing arbitrary code.
Particularly, the researcher studied the scripts present in cdnjs/bot-ansible and cdnjs/tools, including an autoupdate script that facilitated automatic retrieval of library updates.
These scripts would periodically update the CDNJS server with newer versions of software libraries released by their authors on the corresponding npm registry.
In other words, for every library published to CDNJS' GitHub repo, its newer version would be downloaded from the linked npm registry, with the npm version also maintained by the library author.
RyotaK wondered what would happen if a library he had published to CDNJS had its corresponding npm version containing a Path Traversal exploit.
Note, npm packages are published as TGZ (.tar.gz) archives which can easily be crafted with path traversal exploits hiding within.
The researcher first published a test library called hey-sven to CDNJS using GitHub, and then began releasing newer versions of "hey-sven" on the npm registry.
In the newer "hey-sven" versions published to npm, which would eventually get processed by CDNJS' update bots, the researcher injected Bash scripts at strange-looking paths.
These distinct paths are nothing other than Path Traversal exploits hidden inside ZIP/TGZ archives, a concept popularized in 2018 as "ZIP Slip."
Source: BleepingComputer
Once CDNJS servers processed the crafted "hey-sven" npm archives, the contents of these Bash scripts would be executed on the server.
But, the researcher did not want to accidentally overwrite an existing script so he first used a symlink vulnerability to read the contents of the file he was about to overwrite, during this proof-of-concept (PoC) test.
"As Git supports symbolic links by default, it may be possible to read arbitrary files from the cdnjs library update server by adding symlink into the Git repository."
"If the regularly executed script file is overwritten to execute arbitrary commands, the automatic update function may be broken, so I decided to check the arbitrary file reading first," said the researcher.
As soon as his crafted PoC hit the server, RyotaK was able to unexpectedly dump sensitive secrets such as GITHUB_REPO_API_KEY and WORKERS_KV_API_TOKEN into scripts served by the CDN at https://cdnjs.cloudflare.com/...

Source: BleepingComputer
GITHUB_REPO_API_KEY is an API key granting write permissions—enabling an attacker to alter any library on the CDNJS, or tamper with the cdnjs.com website itself!
WORKERS_KV_API_TOKEN secret on the other hand could be used to tamper with the libraries present in the cache of Cloudflare Workers.
"By combining these permissions, the core part of CDNJS, such as the origin data of CDNJS, the KV cache, and even the CDNJS website, could be completely tampered [with]," explains the researcher.
Cloudflare issues many fixes to squash the bug
The researcher reported this vulnerability to Cloudflare via HackerOne's vulnerability disclosure program on April 6th, 2021, and saw Cloudflare's team applying an intermittent fix within hours.
The initial fix seen by BleepingComputer is aimed at resolving the symlink vulnerability:
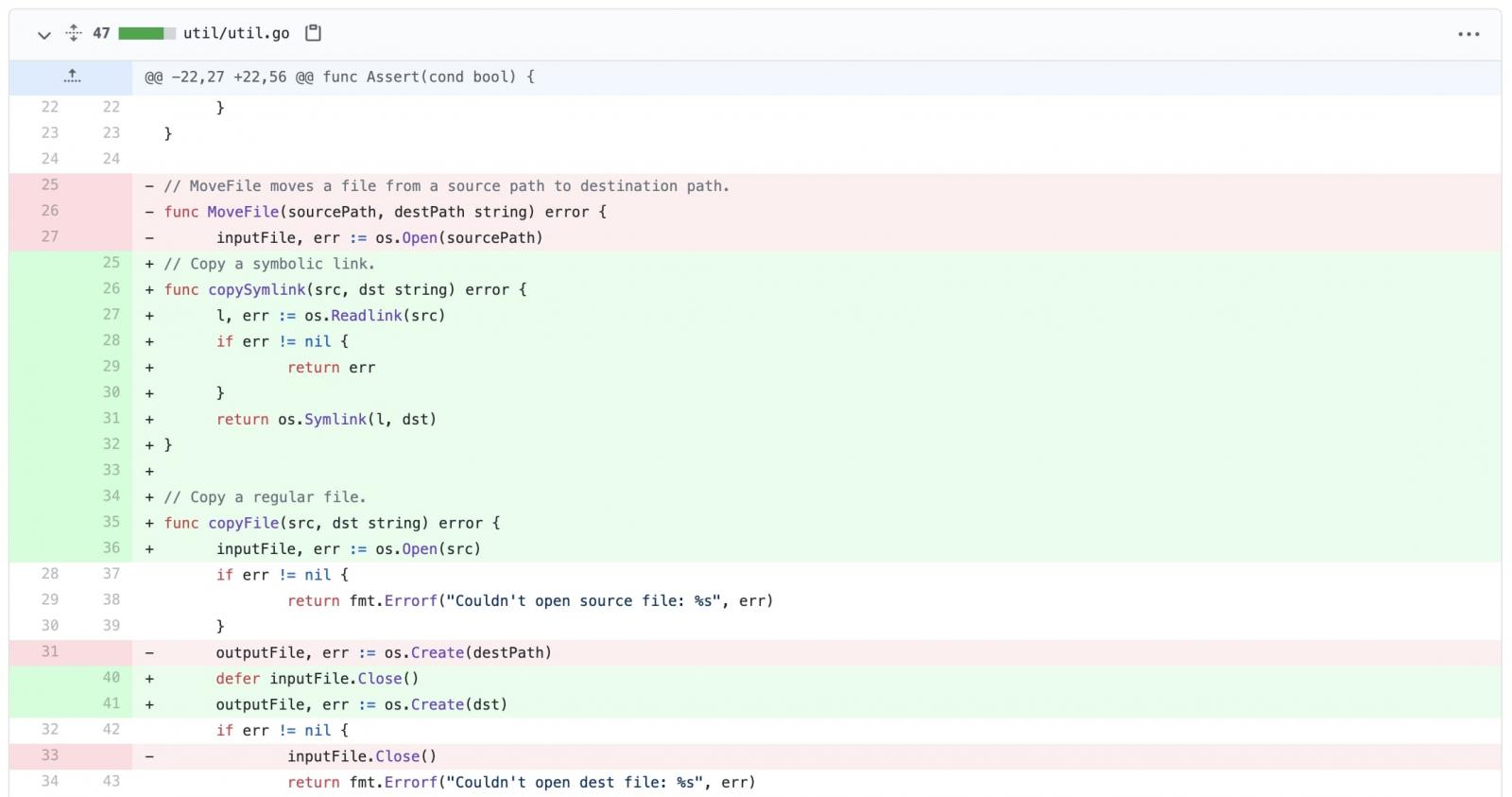
However, due to the complexity of the CDNJS ecosystem, a series of more concrete fixes were applied over the following weeks to different repositories, according to the researcher.
RyotaK shared with BleepingComputer that while the first fix was centered around rejecting symbolic links (symlinks) in Git repositories, it only remediated a part of the problem.
"They tried to refuse symlinks first, but they noticed that current design of the bot is too dangerous. So they isolated most dangerous features."
"And for other features, they applied AppArmors," the researcher told BleepingComputer in an email interview.
Application Armor or AppArmor is a security feature that restricts the capabilities of programs running on Unix-based envionments with predefined profiles so that the programs don't inadvertently exceed their intended scope of access.
The researcher also shared a series of fixes with BleepingComputer deployed by Cloudflare to secure the automated bot processing the updated libraries:
"While this vulnerability could be exploited without any special skills, it could impact many websites."
"Given that there are many vulnerabilities in the supply chain, which are easy to exploit but have a large impact, I feel that it's very scary," says RyotaK in his blog post.
As previously reported by BleepingComputer, a Magecart supply-chain attack impacting thousands of online stores stemmed from the compromise of Volusion's CDN infrastructure.
The researcher praised Cloudflare's fast-paced incident response teams, who, within minutes of receiving the researcher's report, rotated the leaked secrets and worked with him to study the PoC exploits.
BleepingComputer reached out to Cloudflare to understand if this vulnerability had been widely exploited.
A Cloudflare spokesperson told BleepingComputer that the vulnerability has not been exploited and that they are grateful to the researcher for reporting the issue.
"As can be seen from the report, automated systems detected the [researcher's] work and revoked credentials immediately."
"The researcher reported findings to us on April 6 and we had remediated the problem within 24 hours."
"Also, it's important to note that we'll see more and more researchers posting things like this, especially as we're expanding our bounty program and making it more public over time."
"We are happy to see researchers do this kind of testing—and that they are sharing it with us. We want to see more of that," Cloudflare told BleepingComputer.
Cloudflare has also released a blog post detailing this vulnerability and what steps were taken towards its remediation.
Update 13:47 ET: Added statement from Cloudflare.
Update 26-Jul-2021, 02:10 ET: Added link to Cloudflare blog post.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now