
A financially motivated threat actor using USB devices for initial infection has been found abusing legitimate online platforms, including GitHub, Vimeo, and Ars Technica, to host encoded payloads embedded in seemingly benign content.
The attackers hide these payloads in plain sight, placing them in forum user profiles on tech news sites or video descriptions on media hosting platforms.
These payloads pose no risks to users visiting these web pages, as they are simply text strings. However, when integrated into the campaign's attack chain, they are pivotal in downloading and executing malware in attacks.
The hackers responsible for this campaign are tracked by Mandiant as UNC4990 and have been active since 2020, predominately targeting users in Italy.
Involuntary payload hosting
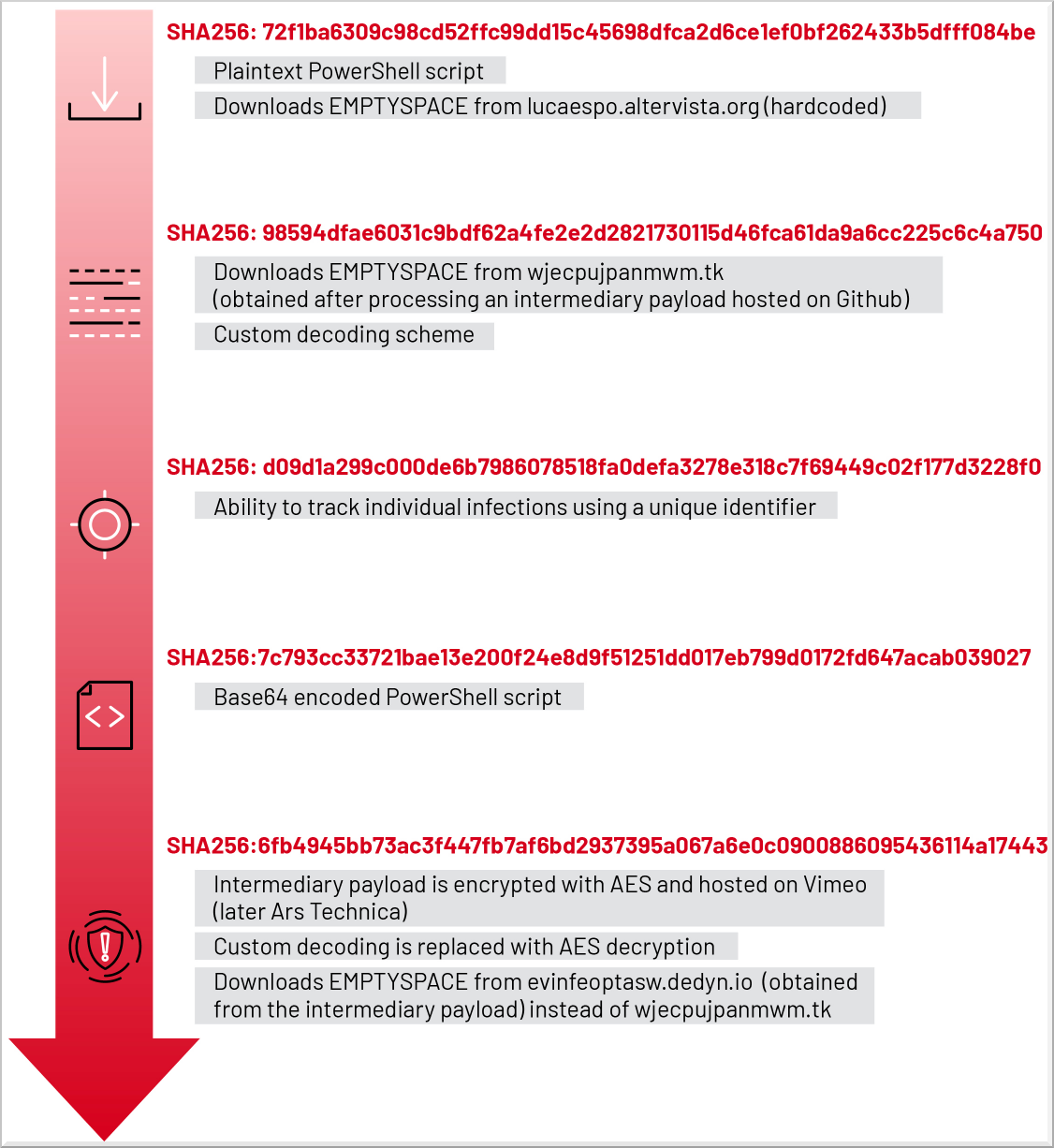
The attack begins with victims double-clicking a malicious LNK shortcut file on a USB drive. It is not known how the malicious USB devices make it to targeted victims to start the attack chain.
When the shortcut is launched, it executes a PowerShell script explorer.ps1, which in turn downloads an intermediary payload that decodes to a URL used to download and install the malware downloader named 'EMPTYSPACE.'
These intermediary payloads are text strings that decode into a URL to download the next payload: EMPTYSPACE.
UNC4990 has tried out several approaches to hosting intermediary payloads, initially using encoded text files on GitHub and GitLab and later switching to abusing Vimeo and Ars Technica for hosting Base64 encoded and AES-encrypted string payloads.
Mandiant notes that the attackers do not exploit a vulnerability in these sites but simply employ regular site features, like an About page in an Ars Technica forum profile or a Vimeo video description, to covertly host the obfuscated payload without raising suspicion.
Source: Mandiant
Also, these payloads do not directly threaten the visitors of the abused sites as they are just harmless text strings, and all cases documented by Mandiant have now been removed from the impacted intermediary platforms.
The advantage of hosting the payloads on legitimate and reputable platforms is that they are trusted by security systems, reducing the likelihood of them being flagged as suspicious.
Moreover, the threat actors benefit from those platforms' robust content delivery networks and enjoy resilience to takedowns.
Embedding the payloads within legitimate content and mixing it with high volumes of legitimate traffic makes it more difficult to pinpoint and remove the malicious code.
Even then, the attackers could easily re-introduce it on a different platform that supports publicly viewable comments or profiles.
Source: Mandiant
Loading Quietboard
The PowerShell script decodes, decrypts, and executes the intermediate payload fetched from the legitimate sites and drops EMPTYSPACE on the infected system, which establishes communication with the campaign's command and control (C2) server.
Source: Mandiant
In the subsequent phases of the attack, EMPTYSPACE downloads a backdoor named 'QUIETBOARD,' as well as crypto coin miners that mine Monero, Ethereum, Dogecoin, and Bitcoin.
The wallet addresses linked to this campaign have made a profit that surpasses $55,000, not accounting for Monero, which is hidden.
QUIETBOARD is a sophisticated, multi-component backdoor used by UNC4990, offering a wide range of capabilities, including:
- Executing commands or scripts received from the C2 server
- Executing Python code received from the C2
- Altering clipboard content for cryptocurrency theft
- Infecting USB/removable drives to spread malware on other systems
- Capturing screenshots for information theft
- Gathering detailed system and network information
- Determining the geographical location of the infected system
QUIETBOARD also establishes persistence across system reboots and supports dynamically adding new functionalities through extra modules.
Mandiant concludes by underlining how UNC4990 likes to conduct experiments with its campaigns to discover optimal pathways for its attack chain and refinement of its methodologies.
Despite the seemingly straightforward prevention measures, USB-based malware continues to pose a significant threat and serve cybercriminals as an effective propagation medium.
As for the tactic of abusing legitimate sites to plant intermediate payloads, this shows that threats can lurk in unexpected, seemingly innocuous locations, challenging conventional security paradigms.



Comments
Elastoer - 5 months ago
This is why you should never blindly trust any website to deliver anything to you.
h_b_s - 5 months ago
You apparently didn't read the article. The websites aren't at fault, and there's quite literally nothing the websites, nor their visitors, could do to stop something like this. Arbitrary text is just that, arbitrary. It can literally be anything, anywhere, and in any sequence. It takes a page from legitimate spycraft in placing innocuous messages in newspapers or at seemingly randomly broadcast over the air that means nothing to anyone but the intended recipient. Impossible to stop or decipher. In this case, it's reassembled into the next stage URL for the infection chain. No, a regex searching for URLs isn't going to work. Again, the other side can just change the sequences rendering any regex useless - not to mention the amount of processing power complex regex demands while adding its own potential attack surface for dubious gain.
The place you stop this particular exploit is not trusting random USB storage devices of unknown provenance (the first stage) and educating workers to resist the temptation to use them along with enforcing policies against workers that repeatedly violate them, including the c-suite.