Security researchers have analyzed a variant of the PlugX malware that can hide malicious files on removable USB devices and then infect the Windows hosts they connect to.
The malware uses what researchers call "a novel technique" that allows it to remain undetected for longer periods and could potentially spread to air-gapped systems.
A sample of this PlugX variant was found by Palo Alto Network’s Unit 42 team during a response to a Black Basta ransomware attack that relied on GootLoader and the Brute Ratel post-exploitation toolkit for red-team engagements.
Looking for similar samples, Unit 42 also discovered a PlugX variant on Virus Total that locates sensitive documents on the compromised system and copies them to a hidden folder on the USB drive.
Hidding PlugX in USB drives
PlugX is an old piece of malware that has been used since at least 2008, initially only by Chinese hacker groups - some of them continue to use it with digitally signed software to side-load encrypted payloads.
Over time, however, it became so widespread that multiple actors adopted it in attacks, making attribution for its use a very challenging task.
In the recent attacks that Unit 42 observed, the threat actor is using the 32-bit version of a Windows debugging tool named ‘x64dbg.exe’ along with a poisoned version of ‘x32bridge.dll,’ which loads the PlugX payload (x32bridge.dat).
At the time of writing, most antivirus engines on the Virus Total scanning platform don't flag the file as malicious, the detection rate being of just 9 out of 61 products.
More recent samples of the PlugX malware are detected by even fewer antivirus engines on Virus Total. One of them, added in August last year, is currently flagged as a threat by just three products on the platform. Obviously, live security agents rely on multiple detection technologies that look for malicious activity generated by a file on the system.
The researchers explain that the PlugX version they encountered uses a Unicode character to create a new directory in detected USB drives, which makes them invisible on Windows Explorer and the command shell. These directories are visible on Linux but concealed on Windows systems.
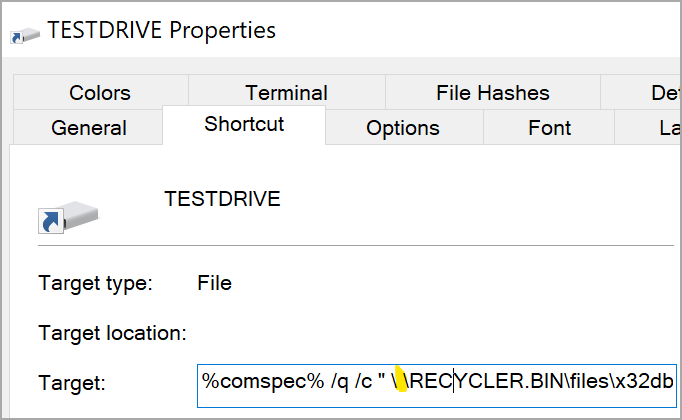
“To achieve code execution of the malware from the hidden directory, a Windows shortcut (.lnk) file is created on the root folder of the USB device,” Unit 42 says.
“The shortcut path to the malware contains the Unicode whitespace character, which is a space that does not cause a line break but is not visible when viewed via Windows Explorer” - Palo Alto Networks Unit 42
The malware creates a ‘desktop.ini’ file on the hidden directory to specify the LNK file icon on the root folder, making it appear as a USB drive to trick the victim. Meanwhile, a ‘RECYCLER.BIN’ subdirectory acts as a disguise, hosting copies of the malware on the USB device.
This technique has been seen in an older version of PlugX analyzed by Sophos researchers in late 2020, although the focus of the report was on the DLL side-loading as a means to execute malicious code.
The victim clicks on the shortcut file on the root folder of the USB device, which executes x32.exe via cmd.exe, resulting in the infection of the host with the PlugX malware.
Simultaneously, a new Explorer window will open to show the user’s files on the USB device, making everything appear normal.
After PlugX gets on the device, it continually monitors for new USB devices and attempts to infect them on discovery.
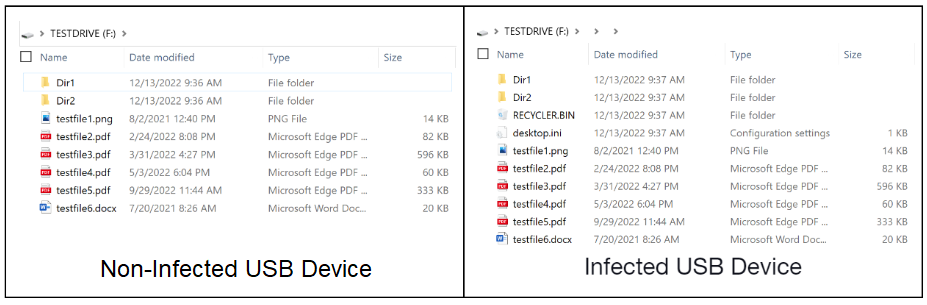
During their research, the Unit 42 team has also discovered a document-stealing variant of the PlugX malware that targets USB drives, too, but has the added capability of copying PDF and Microsoft Word documents onto a folder in the hidden directory called da520e5.
It is unknown how the threat actors retrieve these “locally exfiltrated” files from the USB drive, but physical access might be one of the ways.
While PlugX was typically associated with state-backed threat actors, the malware can be purchased on underground markets and cybercriminals have also used it.
With the new development that makes it more difficult to detect and allows it to spread through removable drives, Unit 42 researchers say that PlugX has the potential to jump to air-gapped networks.



Comments
27ragbag - 1 year ago
If the flash drive is write protected before being connected, this wouldn't happen. A virus will ping a device if it is writable or not, if the device is read-only, the virus will ignore it. That is why a "lock license" drive should be used... because by default the USB is always write protected, until the user can define _when_ it should be writable.
ThomasMann - 1 year ago
I may be getting old, but when I read about malware, I usually want to know, HOW does it get into my compomputer, and HOW does a file then get out to the hacker.
What I red is: "It is unknown how the threat actors retrieve these “locally exfiltrated” files from the USB drive, but physical access might be one of the ways."
Really?????
DyingCrow - 1 year ago
Really.
You just have to look at possible scenarios, one is an insider job. It's fairly easy to leave one of these plugged to an executive's laptop dock without him even noticing it (use a USB extension to hide it somewhere if necessary, much less conspicuous), then just wait a few days and get it back.
ThomasMann - 1 year ago
I never said that IDIOTS will be safe...
Once you understand the problems with security, and come to the correct conclusion that basivcally YOU are responsible, then you ought to accept the consequences of that simple fact.
If you refuse to do this, or are too stupid to understand it, then sooner or later you will have a huge problem.
I cannot see anything that is hard to understand about the situation.
Also, there are now the first desktop size Quantum Computers for sale in China (at $500.000!). Still, for a hacker this might be a worthwhile investment.
Given the ridiculous, so-called "sophistication" of security AND the incompetence of the users, I am looking very much forward to see the first REAL breaches of internet banking.
TsVk! - 1 year ago
Easy there mate. It may seem all so simple from a home user point of view but when you start adding sophisticated networks and many people suddenly the task of securing it all and maintaining usability becomes a monumental task. There's a reason that people have multiple degrees on this topic and those who understand it's complexities are in high demand.
Even if you had every qualification under the sun, and knew how to secure every network that ever existed, tomorrow there will be a zero day you never saw before and if you are valuable enough you will be targeted, and you will be pwned. If not tomorrow, then the day after. It's just a matter of when.
bugzorc - 2 months ago
Fascinating, isn't it?