
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has published research looking into 172 key open-source projects and whether they are susceptible to memory flaws.
The report, cosigned by CISA, the Federal Bureau of Investigation (FBI), as well as Australian (ASD, ACSC) and Canadian organizations (CCCS), is a follow-up to the 'Case for Memory Safe Roadmaps' released in December 2023, aimed at raising awareness about the importance of memory-safe code.
Memory safety
Memory-safe languages are programming languages designed to prevent common memory-related errors such as buffer overflows, use-after-free, and other types of memory corruption.
They achieve this by managing memory automatically instead of relying on the programmer to implement safe memory allocation and deallocation mechanisms.
A modern example of a safe language system is Rust's borrow checker, which eliminates data races. Other languages like Golang, Java, C#, and Python manage memory through garbage collection, automatically reclaiming freed memory to prevent exploitation.
Memory-unsafe languages are those that do not provide built-in memory management mechanisms, burdening the developer with this responsibility and increasing the likelihood of errors. Examples of such cases are C, C++, Objective-C, Assembly, Cython, and D.
Widely used open-source code unsafe
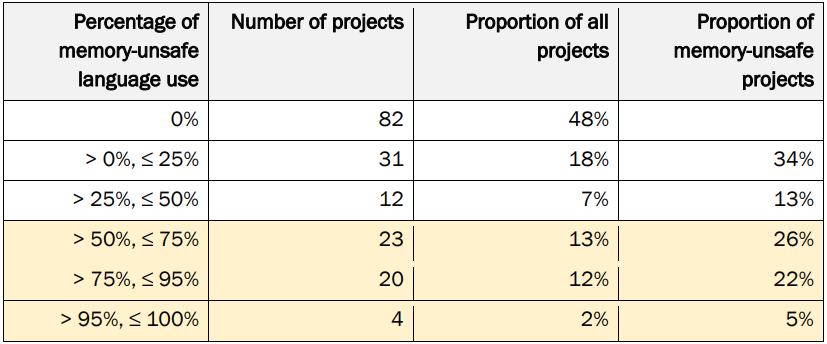
The report presents research examining 172 broadly deployed open-source projects, finding that over half contain memory-unsafe code.
Key findings presented in the report are summarized as follows:
- 52% of critical open-source projects analyzed contain code written in memory-unsafe languages.
- 55% of the total lines of code (LoC) across these projects are written in memory-unsafe languages.
- The largest projects are disproportionately written in memory-unsafe languages.
- Of the ten largest projects by total LoC, each has a proportion of memory-unsafe LoC above 26%.
- The median proportion of memory-unsafe LoC in these large projects is 62.5%, with four projects exceeding 94%.
- Even projects written in memory-safe languages often depend on components written in memory-unsafe languages.
Some notable examples from the examined set are Linux (unsafe code ratio 95%), Tor (unsafe code ratio 93%), Chromium (unsafe ratio 51%), MySQL Server (unsafe ratio 84%), glibc (ratio 85%), Redis (ratio 85%), SystemD (65%), and Electron (47%).
Source: CISA
CISA explains that software developers face multiple challenges that often oblige them to use memory-unsafe languages, such as resource constraints and performance requirements.
That is especially true when implementing low-level functionalities like networking, cryptography, and operating system functions.
"We observed that many critical open source projects are partially written in memory-unsafe languages and limited dependency analysis indicates that projects inherit code written in memory-unsafe languages through dependencies," explains CISA in the report.
"Where performance and resource constraints are critical factors, we have seen, and expect the continued use of, memory-unsafe languages."
The agency also highlights the problem of developers disabling memory-safety features, either by error or on purpose, to meet specific requirements, resulting in risks even when using theoretically safer building blocks.
Ultimately, CISA recommends that software developers write new code in memory-safe languages such as Rust, Java, and GO and transition existing projects, especially critical components, to those languages.
In addition, it is recommended to follow safe coding practices, carefully manage and audit dependencies, and perform continuous testing, including static analysis, dynamic analysis, and fuzz testing, to detect and address memory safety issues.



Comments
SecurityIsStress - 4 days ago
Devs usually know multiple languages, but it seems a losing effort to ask use memory safe languages. Large code rebases and having to re-specialize is a very tall ask. Would make sense if they took the effort trying to get everyone to switch and built modules to assist those unsafe languages use memory more safely.
U_Swimf - 3 days ago
Maybe it's the fact cell phones obviously enable their devices to using 8+ core CPUs with 12-16gb of memory on something origijally built to do calling and messaging.
Unsafe code is some companies anti cpmpete agenda to keep others away from that code. probably because they themselves used it to get where they are seated ...
Winston2021 - 3 days ago
Had to look it up:
Linux (the kernel) is essentially written in C with a little of assembly code.
The lower layer of userland, usually GNU (glibc and other libraries plus standard core commands) are almost exclusively written in C and shell scripting.
The remaining of the Gnu/Linux distributions userland is written in any language developers decide to use (still a lot of C and shell but also C++, python, perl, javascript, java, C#, golang, whatever ...)
ctigga - 3 days ago
Yeah, "unsafe" languages like Assembly, C, C++ are not going away anytime soon because they are the most performant for both speed of execution and memory; The code produced by these languages executes directly on the processor chips. It should come as no surprise that OS code (as well as applications wanting the best performance) will use these languages liberally.
The cutesy VM/Intermediate byte code languages (Java/C#, et. al.) and the many scripting languages are simpler for many people to use and help protect against common errors -- but they're still not infallible to targeted abuses (even if they're not using native/unmanaged/cli links to "unsafe" modules)
NoneRain - 3 days ago
Yep. But things are slowing changing, with languages like Rust being considered for kernel development. A long way to go, tho.
scantalk - 3 days ago
In some weird way. I seems like the people at CISA are the once that failed assembler and C classes and now wants to get even.