
A new malware distribution campaign uses fake Google Chrome, Word, and OneDrive errors to trick users into running malicious PowerShell "fixes" that install malware.
The new campaign was observed being used by multiple threat actors, including those behind ClearFake, a new attack cluster called ClickFix, and the TA571 threat actor, known for operating as a spam distributor that sends large volumes of email, leading to malware and ransomware infections.
Previous ClearFake attacks utilize website overlays that prompt visitors to install a fake browser update that installs malware.
Threat actors also utilize JavaScript in HTML attachments and compromised websites in the new attacks. However, now the overlays display fake Google Chrome, Microsoft Word, and OneDrive errors.
These errors prompt the visitor to click a button to copy a PowerShell "fix" into the clipboard and then paste and run it in a Run: dialog or PowerShell prompt.
"Although the attack chain requires significant user interaction to be successful, the social engineering is clever enough to present someone with what looks like a real problem and solution simultaneously, which may prompt a user to take action without considering the risk," warns a new report from ProofPoint.
The payloads seen by Proofpoint include DarkGate, Matanbuchus, NetSupport, Amadey Loader, XMRig, a clipboard hijacker, and Lumma Stealer.
PowerShell "fix" leads to malware
Proofpoint analysts observed three attack chains that differentiate mainly on their initial stages, with only the first not being attributed with high confidence to TA571.
In this first case, associated with the threat actors behind ClearFake, users visit a compromised website that loads a malicious script hosted on the blockchain via Binance's Smart Chain contracts.
This script performs some checks and displays a fake Google Chrome warning stating a problem displaying the webpage. The dialog then prompts the visitor to install a "root certificate" by copying a PowerShell script into the Windows Clipboard and running it in a Windows PowerShell (Admin) console.
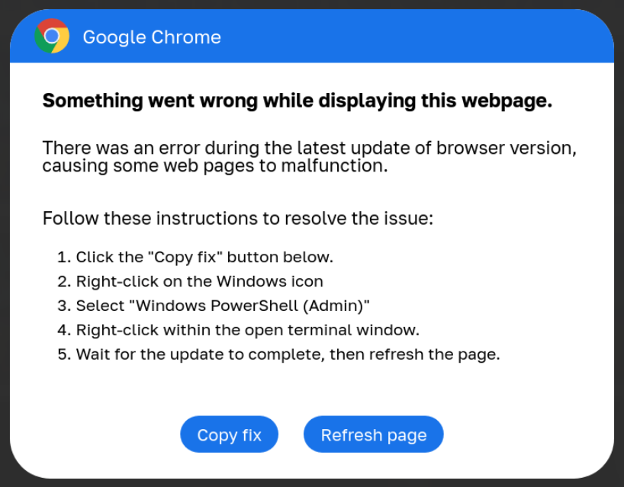
Source: Proofpoint
When the PowerShell script is executed, it will perform various steps to confirm the device is a valid target, and then it will download additional payloads, as outlined below.
- Flushes the DNS cache.
- Removes clipboard content.
- Displays a decoy message.
- Downloads another remote PowerShell script, which performs anti-VM checks before downloading an info-stealer.
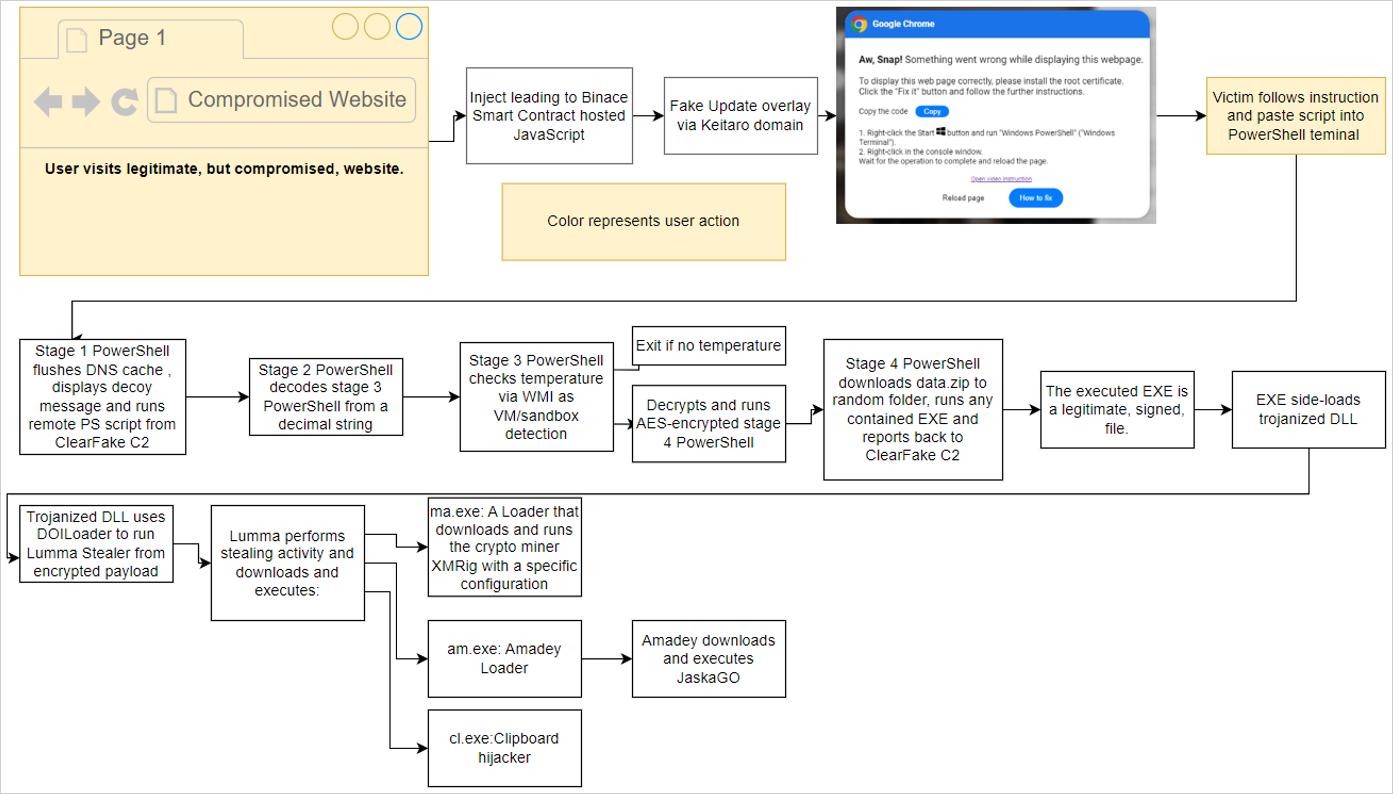
Source: Proofpoint
The second attack chain is associated with the 'ClickFix' campaign and uses an injection on compromised websites that creates an iframe to overlay another fake Google Chrome error.
Users are instructed to open "Windows PowerShell (Admin)" and paste the provided code, leading to the same infections mentioned above.
Finally, an email-based infection chain using HTML attachments resembling Microsoft Word documents prompts users to install the "Word Online" extension to view the document correctly.
The error message offers "How to fix" and "Auto-fix" options, with "How to fix" copying a base64-encoded PowerShell command to the clipboard, instructing the user to paste it into PowerShell.
Auto-fix" uses the search-ms protocol to display a WebDAV-hosted "fix.msi" or "fix.vbs" file on a remote attacker-controlled file share.
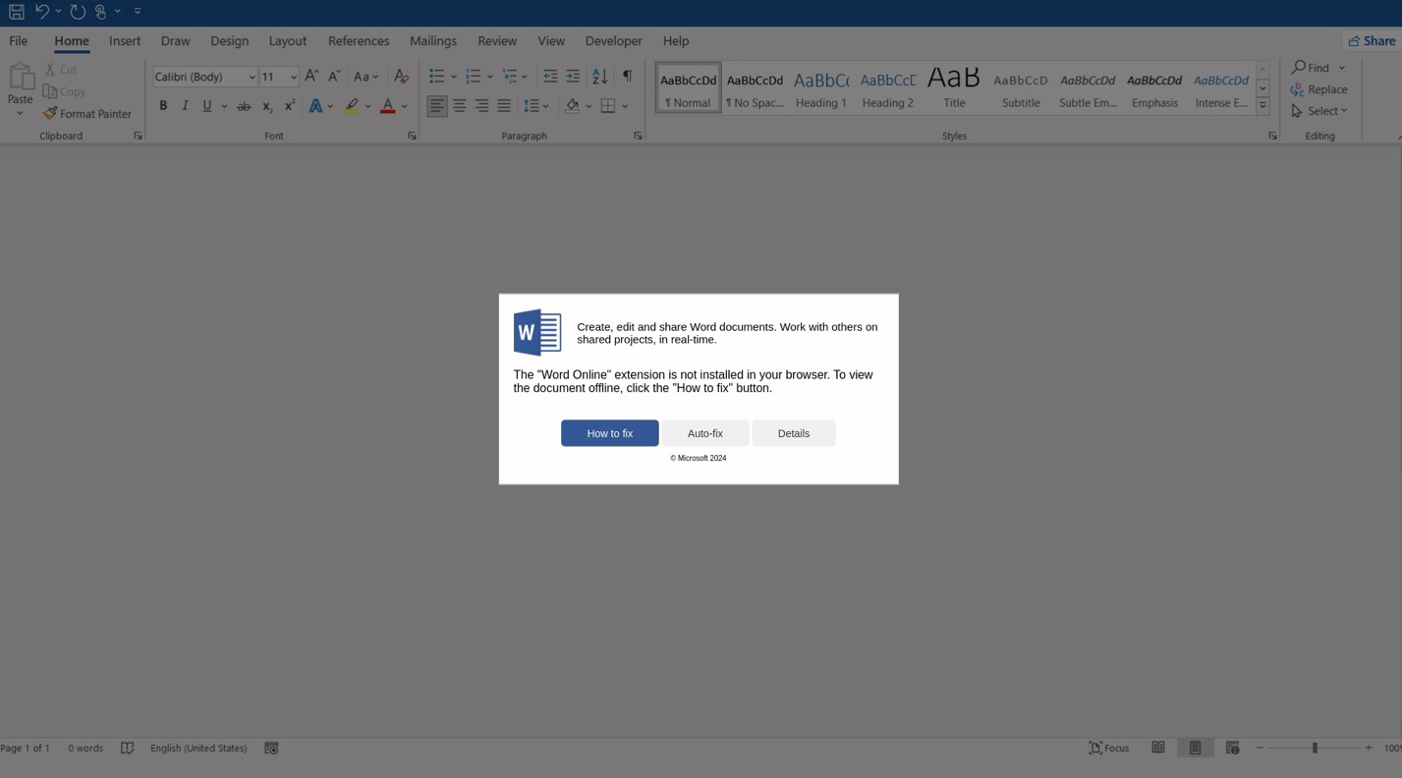
Source: Proofpoint
In this case, the PowerShell commands download and execute either an MSI file or a VBS script, leading to Matanbuchus or DarkGate infections, respectively.
In all cases, the threat actors exploit their targets' lack of awareness about the risks of executing PowerShell commands on their systems.
They also take advantage of Windows' inability to detect and block the malicious actions initiated by the pasted code.
The different attack chains show that TA571 is actively experimenting with multiple methods to improve effectiveness and find more infection pathways to compromise a larger number of systems.



Comments
newtronic - 1 week ago
The first attack appears to need admin privileges ( Powershell (Admin)) and the second one (clearFake) just says Powershell (Windows Terminal). Do they need admin ?
Mr.Tom - 1 week ago
Inconsistent wording here. The graphic says Windows Powershell, but the author says Windows PowerShell (Admin). Plus the graphic only says to right-click, they never tell the victim to press the Enter key, but I suppose they'd eventually do it anyway.
On a side note, I did a registry experiment from another page to disable Powershell. I didn't reboot, but my explorer.exe keeps crashing and reloaded. I try to run either of the Powershell commands, and it states 'the operation has been canceled'. But I select either of the Terminal commands, and Powershell loads up okay. Caution to anyone trying to disable Powershell, you'll also need to find a way to disable the "Terminal" command too.
omnom - 1 week ago
If the command copied to the clipboard has a second superfluous line, return character, etc it will execute without pressing enter; HOWEVER, it will pop up a warning that pasting multiple lines can result in "unexpected execution of commands". Something tells me though that the type of person to fall victim to this pop-up would just hit the "Paste Anyway" button.
Since the actual commands listed in the IOC list all have "exit;" at the end, whatever extra line is pasted and not executed would be irrelevant since the window will close.
If you paste something like this:
Write-Host 'Foo'
""
After the warning you'll get the "Foo" and then "" waiting at the next prompt. Add "; exit" after the write-host and the window closes so you never see the unexecuted "".