Malware distributors have setup a site that impersonates the legitimate Cryptohopper cryptocurrency trading platform in order to distribute malware payloads such as information-stealing Trojans, miners, and clipboard hijackers.
Cryptohopper is a trading platform where users can build models that will be used for automated trading of cryptocurrency on various markets.
In a new campaign discovered by malware researcher Fumik0_, attackers have created a replica of the Cryptohopper trading platform site that when visited will automatically download a Setup.exe executable as shown below.
This Setup.exe executable uses the CryptoHopper logo as its icon to make it seem like a legitimate offering from the trading platform, but is actually the Vidar information-stealing Trojan.
When executed, this Vidar variant will download required libraries and then install two Qulab trojans; one that acts as a miner and the other that acts as a clipper, or clipboard hijacker.
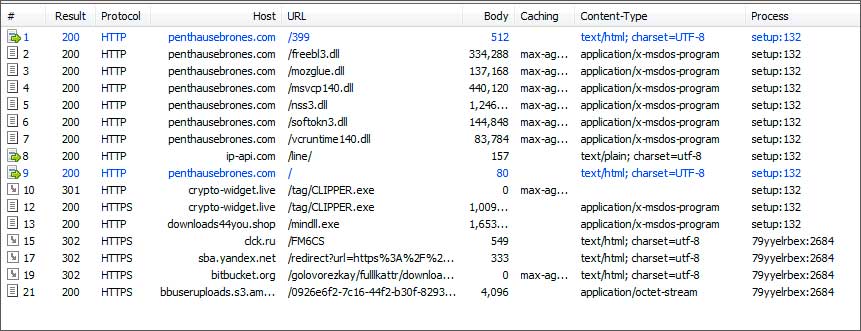
The QuLab associated files will be downloaded into the folders:
C:\ProgramData\x86_microsoft-windows-p..ting-separatorpages_31bf3856ad364e35_10.0.14393.0_none_c34b1497126d7bf8
C:\ProgramData\amd64_microsoft-windows-m..essagingcoreservice_31bf3856ad364e35_10.0.17134.1_none_c88a541351589fbb
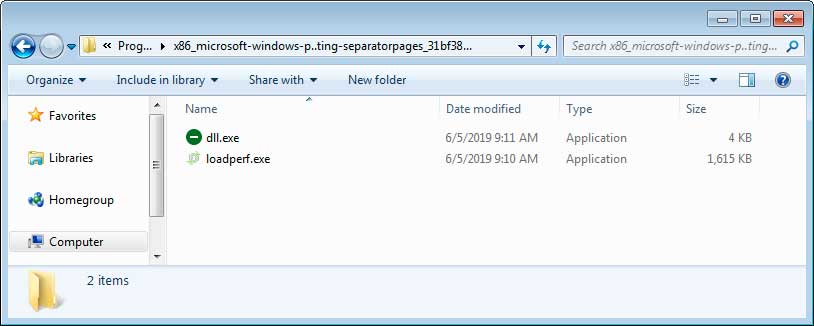
In order to add persistence, scheduled tasks will be created that launch the clipper and miner executables every minute.

Information-stealing capabilities
After downloading the files and configuring persistence, Vidar will begin to collect data from the machine and compile it under a random named directory in the %ProgramData% folder as shown below.

Configuration files shared with BleepingComputer by Fumik0_ show that Vidar will attempt to steal the following information:
- browser cookies
- browser history
- browser payment information
- saved login credentials
- cryptocurrency wallets
- text files
- browser form autofill information
- Authy 2FA authenticator databases
- a screenshot of your desktop at the time of infection, and more.
This information will then be uploaded to a remote server so that it can be collected by the attackers. After sending the information, the collection of files will be removed from the infected machine, leaving behind a directory full of empty folders.
Due to the nature of the impersonated site, the potential for stolen credentials and 2 factor authentication information is particularly concerning.
As Cryptohopper is a cryptocurrency trading platform, if one of their users mistakenly goes to this fake site and installs the Trojan, their Cryptohopper credentials could be stolen and used to steal cryptocurrency stored on the platform.
Clipper component steals cryptocurrency
Vidar will also download and install the QuLab Trojan, which will perform clipper, or clipboard hijacking, functionality on the infected computer.
As cryptocurrency addresses are long and hard to remember strings, people typically copy the address into the Windows clipboard and then paste them in another application to transfer the cryptocurrency.
When QuLab detects that an address is copied into the clipboard, it will substitute the copied address with one under their control in order to steal the cryptocurrency.
The cryptocurrency addresses that are substituted by this clipper are shown in the table below.
| CryptoCurrency | Address | Transactions Amount |
| Ethereum | 0xeF44179038f46b139BC4B8f7E73E479642C5B302 | 0.001136742901273047 |
| Bitcoin | 1FFRitFm5rP5oY5aeTeDikpQiWRz278L45 | 32.87981922 |
| Bitcoin Cash | qpuzruuhf04qf9ae4ayvzq7wzyn8drwq05eczxfd96 | 0 |
| DOGE | DEHfj44qErZuUW2qqw92W2tLVQ4mfyDvXa | 0 |
| Dash | XwhQSkYKzyqhjnipro4bhsXHtAtTJD6dbR | 0.10430658 |
| Litecoin | LT1Kqob5UDEML61gCyjnAcfMXgkdP3wGcg | 4.37138704 |
| Zcash | t1JZ7MuMn6D1B8ujUbHEkpC76sK6tG5ic81 | 0 |
| Bitcoin Gold | Gf9m5PCwpwb1EG9XyJgwVosLWYX7URUBcF | 0 |
| QTUM | QihCFPSNPkwLNBTbVZHUAnYc5iRYaWz9em | 0 |
| Ripple | rLQMLrMmvrva5skwyM4QzDUoGQJGhaovqy | 1,094 |
The transactions in the above cryptocurrency addresses may not be purely from this campaign, but they do show that the actor has made quite a bit of money from their malicious activities.
For example, the Bitcoin address of 1FFRitFm5rP5oY5aeTeDikpQiWRz278L45 has had a total transaction amount of 32.87981922 bitcoins. This is worth $253,238.39 at Bitcoin's current values.
Sites created to push malware becoming more common
The creation of professionally designed sites to impersonate legitimate services or to promote fake software has become increasingly common.
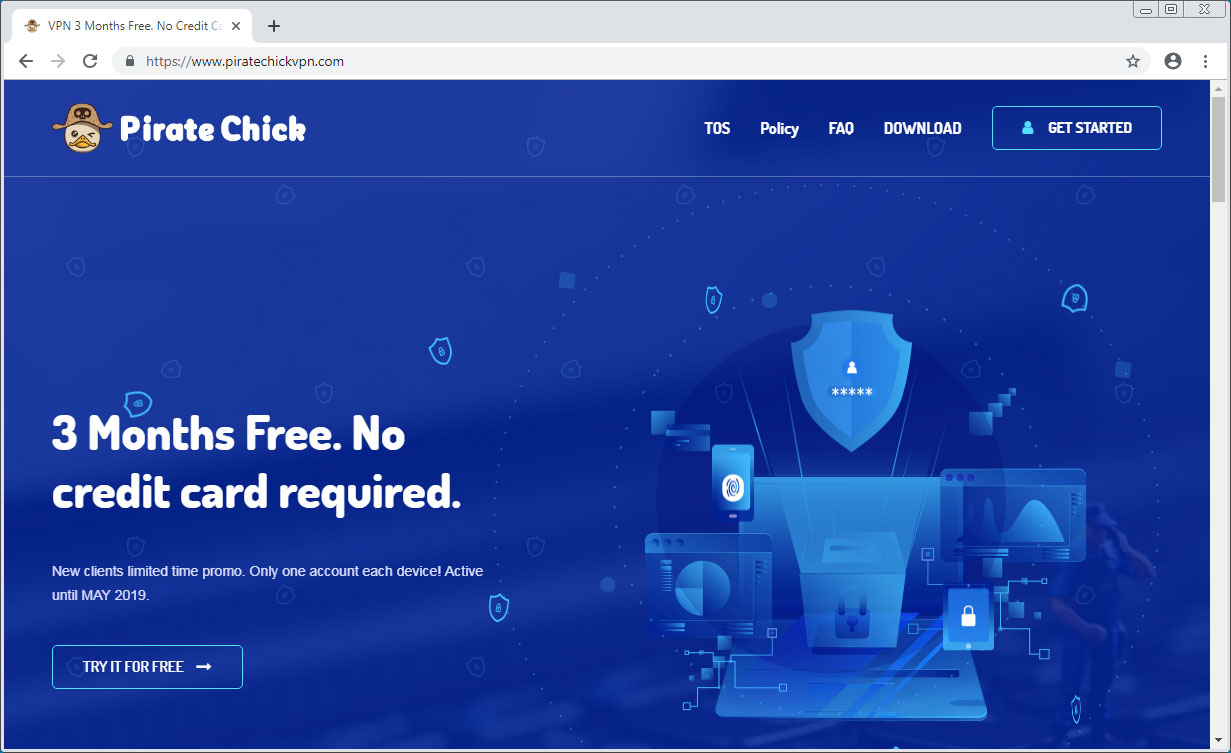
For example, in May we reported that attackers have created a site to promote a fake VPN software called Pirate Chick that is used to distribute the AZORult password-stealing Trojan.
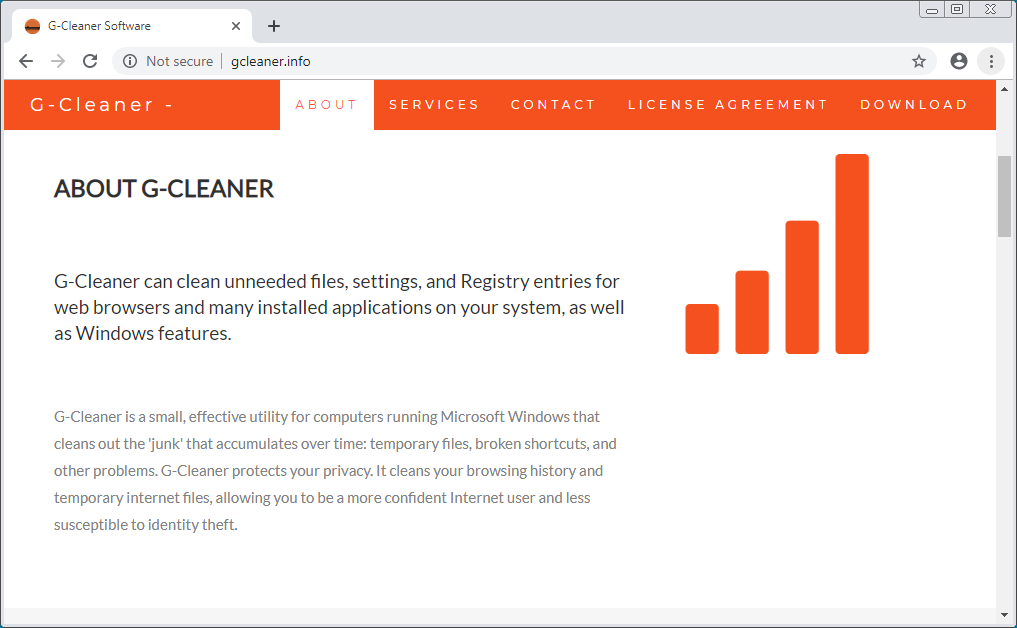
Another example is a site created to promote a fake Windows system cleaner called G-Cleaner that also installs information stealing Trojans.
To protect themselves, users should make sure the site they are visiting is the legitimate URL for the associated service. Furthermore, if these sites offer any downloads, they should be scanned using VirusTotal before being executed.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now