XP Network Log-on for Home Users
Table of Contents
Want your logon screen to look like this?
Figure 1.1
If you use a computer at work, school, library, or where ever a computer is on a network, you've probably seen the logon screen where it tells you to press Ctrl+Alt+Del. This is the logon prompt that XP Professional users and Windows 2000 users receive when the machine is configured to log on to a network. If this type of login is more comfortable for you to use and you would like to change your XP Home logon to do this as well, then please read on.
Requirements
There are only two (2) things you need to have in order to use this logon type:
- You need to have Microsoft Windows XP Home or Professional.
- You need to have access to an administrator account on the computer.
Very first thing you need to do is to turn off your current logon type.
-
Click Start
- Click Control Panel
- In the Classic View of the Control Panel, double click on User Accounts.
- Click Change the way users log on or off. If you get a pop-up about "Fast Switching," just click cancel.
- Uncheck Use Fast User Switching and Use the Welcome Screen
- Click Apply Options
- Click on the Guest account
- Click Turn OFF the Guest Account
- Close out of the User Accounts windows by clicking the little X.
Now that you have turned off your old logon, now you have configure your new logon. :)
-
Right Click on the TaskBar
- Click Properties
- Click the Start Menu tab
- Click the Radio Button option Start Menu
- Then click Customize
- Click the Advanced tab
- Scroll down and click the Radio Button option under "System Administrative Tools," labeled Display on the All Programs menu and the Start Menu.
- Click Ok, then click Ok.
- Now you have to adjust our "preferences." You should be viewing your desktop.
- Click Start
- Click Administrative Tools while the rollover menu is still there, click Local Security Policy
- On the left side of the screen click the + so its a – on the Local Policies menu.
- Then click on Security Options
-
Then make sure the following is changed to or is the option in bold.
- Interactive logon: Do not display last user name. Change it to Enabled
- Interactive logon: Do not require CTRL+ALT+DEL. Change it to Disabled*
- Interactive logon: Message text for users attempting to log on. Change it to anything you want, on mine it is: "Welcome to YanoNet! By touching this computer you are agreeing to the EULA. Thank you. If you need an account please contact the administrator."(This text will appear as shown in Figure 1.3)
- Interactive logon: Message title for users attempting to log on: Change it to anything you want. Mine is: Welcome to YanoNet!" (White text in the top bar of Figure1.3)
- System cryptography: User FIPS compliant algorithms for encryption, hashing, and signing. Enabled
- System objects: Strengthen default permissions of internal system objects (e.g. Symbolic Links) Enabled
If you have followed these steps correctly your computer is now set to login as if you are on a network. Next time you reboot you will see a screen like this.
Figure 1.2
To start the login process, press Control-Alt-Delete. You will now be presented with the message text that you created in step 14.3 and 14.4.
Figure 1.3
Press OK to accept the message and you will be presented with the logon screen as show below.
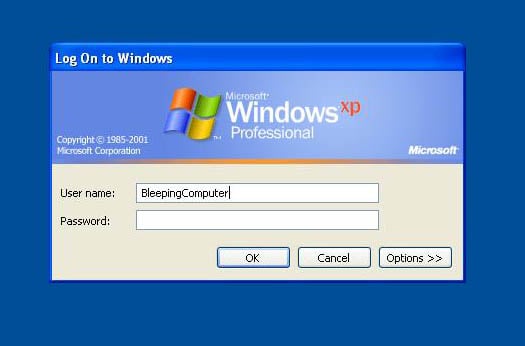
Figure 1.4
You can now enter your account information to logon to Windows.
As always if you have any questions please do not hesitate to ask them in the computer help forums.
--
Yanowhiz
Bleeping Computer Microsoft Advanced Concepts Tutorial
BleepingComputer.com: Computer Help & Tutorials for the beginning computer user.








