This topic was created to provide a very brief introduction as to what RKill does and to provide a way a way for people to report false positives of processes that are terminated. Even though false positives may occur, this should not be considered a problem as you can always launch the programs again or reboot your computer as no files are removed by running RKill. This topic is not to be used as a support topic for removing malware. If you need help removing specific malware you can follow the steps here or ask in the Am I Infected? forum.
RKill is a program developed at BleepingComputer.com that was originally designed for the use in our virus removal guides. It was created so that we could have an easy to use tool that kills known processes and remove Windows Registry entries that stop a user from using their normal security applications. Simple as that. Nothing fancy. Just kill known malware processes and clean up some Registry keys so that your security programs can do their job.
So in summary, RKill just kills 32-bit and 64-bit malware processes and scans the registry for entries that would not allow you to run various legitimate programs. When scanning the Registry, Rkill will search for malicious Image File Execution Objects, DisallowRuns entries, executable hijacks, and policies that restrict your use of various Windows utilities. When changing Windows Registry entries it will create a backup of these entries and save them in the rkill folder on your desktop. Each registry backup will contain a time stamp so that the backups are not overwritten on subsequent runs of Rkill. For a list of changes in Rkill, please see the change log at the bottom of this post.
Since RKill only terminates processes and does not remove the offending files, when it is finished you should not reboot your computer. If you do, these malware processes that are set to start automatically, will just start up again. Instead, after running RKill you should scan your computer using your malware removal tool of choice. If there is a problem after running RKill, just reboot your computer and you will be back to where you started before running the program. Some great free tools that you can use to scan your computer after running RKill include MalwareBytes' Anti-Malware, SuperAntiSpyware, and Dr.Web CureIt.
RKill can be downloaded from the following location:
http://www.bleepingcomputer.com/download/rkill/
Please note that the other file names at the link above are RKill as well, but just renamed in order to allow it run by certain malware.
When RKill is run it will display a console screen similar to the one below:
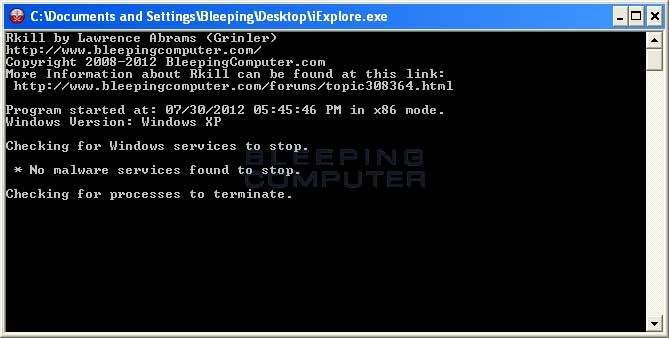
That console screen will continue to run until it RKill has finished. Once finished, the box will close and a log will be displayed showing all of the processes that were terminated by RKill and while RKill was running.
Depending on the malware that is installed on the computer, when you run RKill you may see a message from the malware stating that the program could not be run because it is a virus or is infected. Examples of these warnings are:
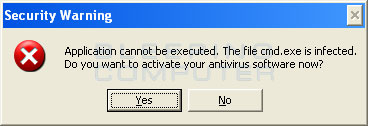
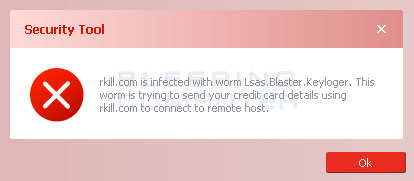
These warnings are just fake alerts by the malware that has hijacked your computer trying to protect itself. Two methods that you can try to get past this and allow RKill to run are:
- Rename Rkill so that it has a .com extension.
- Download a version that is already renamed as files that are commonly white-listed by malware. The main Rkill download page contains individual links to renamed versions.
Rkill is currently detected as malware by 3 anti-virus companies. I have submitted the tool to them so that they can remove the listing. Unfortunately, though, false positives ocassionaly happen. I assue you that there is nothing malicious in Rkill and it only performs the tasks described above.
A scan from virustotal.com as of 08/22/12 shows the following AV vendors flagging RKill with false positives
Comodo UnclassifiedMalware 20120822 Kaspersky HEUR:Backdoor.Win64.Generic 20120822 TrendMicro-HouseCall TROJ_GEN.F47V0821 20120822
Also at least SuperAntiSpyware and MalwareBytes may target Rkill when you rename it to a reserved name like iexplore.exe, explorer.exe, winlogon.exe, etc. This is because they have definitions in place that throws a flag when these reserved filenames are used outside their normal path.
If you see these alerts when running Rkill, you can safely ignore the warnings and continue to allow the program to run.
If you have any other questions about RKill, feel free to post them in the topic. Do not, though, ask questions about how to get RKill to run, unless you can provide a better method to get around the malware blocking it. Also please do not ask about how to remove specific malware. Those questions should be asked in the forums listed earlier in the topic.
How to create a custom whitelist file for Rkill
Rkill 2.5.9 added a new white listing component for IT, Consultants, and Enterprise support who are finding some of their remote support or other applications are being terminated by Rkill. Using this feature you can specify a custom white list file that contains a list of processes that should not be terminated.
When creating this file it must be saved in either ANSI or UTF-8. The file should consist of a list of processes with each process being on their own line. Each process you want to whitelist must also be listed using the full path such as C:\Windows\System32\App1.exe. You can specify the whitelist file using the -w command line argument. Please note, there is no need to enclose paths with spaces in quotes. In fact quotes will cause the files not to be properly matched.
An example command to start rkill using a whitelist is:
rkill -w c:\users\user\desktop\wl.txt
When giving the name of the white list, you can also use some variables to make it easier. These are:
%SystemDrive% - This will expand to the drive letter that Windows is installed. Typically expanding to C:.
%WinDir% - Expands to the folder where Windows is installed. IE: C:\Windows
%System% - Expands to the System32 folder in Windows. IE: C:\Windows\System32
%Desktop% - Expands to the desktop folder for the currently logged in user.
%UserProfile% - Expands to the UserProfile folder.
%AllUsersProfile% - Expands to the All Users Profile folder.
An example whitelist file is as simple as:
c:\windows\app1.exe c:\remote.exe "c:\program files\test.exe"
When you run Rkill using a whitelist, it will state that White List mode is enabled and then display the logfile. If there are any issues with your white list file it will alert you. Last, but not least, is you use a whitelist, rkill will display a list of processes that matched the contents of your whitelist and that were ignored.
Full list of commands:
-d: Enters debug mode. This mode pauses after listing each process
Rkill is checking.
-h : Shows this help screen.
-? : Shows this help screen.
-l: Allows you to specify a custom logfile path. The argument
following -l will be used as the logfile.
Example: rkill -l c:\rkill-log.txt
-w: Allows you to specify a white list file. The argument
following -w will be used as the white list file.
Example: rkill -w %Desktop%\rkill-wl.txt
Known Issues:
- Rkill needs to be updated for the Windows 10 Anniversary Update. If you see issues of missing services or other strange behavior after updating, please wait for a new version.
Changelog:
12/2/10:
- Major rewrite of the program to be more effective.
- Uses a white-list for displaying the processes that were killed. This is so it no longer shows itself as being killed and some other processes that were always displayed in Vista and Windows 7 even though Rkill didn't terminate them.
- Cleaned up output.
3/1/11:
- Rkill will fix modified batch file classes so that they can run as normal
3/4/11:
- If Rkill detects a proxy, it will disable it and make a backup on the desktop as rk-proxy.reg.
05/18/12:
- Rkill is now located at a new download link
07/30/12: Rkill version 2.0 is released.
This version contains many new features. These features can be found below.
- Rewritten as a single executable.
- Much much faster.
- Better reporting:
- Rkill now only lists those processes it actually terminates.
- Writes all actions it takes and any results into rkill.txt log file on the desktop.
- Details the registry keys it fixes. These are only some policies, executable associations, IFEO, and DisallowRun keys.
- The ability to use Rkill without remote control apps being terminated. This has been tested with TeamViewer, VNC, and Logmein. If you use a custom application, I still suggest you create a folder for it rather than running it from a Userprofile.
- Chrome is no longer terminated.
- Can kill file impersonators found in any directory (svchost.exe, winlogin, etc)
- Makes a registry backup of any IFEO, Proxy settings, DisallowRun, or Policies that it removes.
- Has the ability to terminate 64-bit processes as well.
08/16/12: Rkill version 2.2 is released.
This version contains many new features and an important fix.
- Missing digital signature detection on Windows files.
- Scan services and reports damaged or missing entries.
- Usermode ZeroAccess detection.
- Fixed bug that could cause Rkill to trigger a reboot on machines with ZeroAccess installed.
08/16/12: Rkill version 2.2.1 is released.
- Display possible patched files
08/21/12: Rkill version 2.3.0 is released.
- Rewrote Windows Service integrity checks.
- Added reporting for policies that disable System Restore, Automatic Updates, Windows Firewall, and Windows Defender.
- Reports when necessary services are stopped.
09/07/12: Rkill version 2.3.8 is released.
- Fix incorrect reports of services missing in Windows 7 Home Premium
- Added Recycle Bin ZeroAccess Rootkit detection
09/19/12: Rkill version 2.4.1
- Added HOSTS file enumeration.
- Checks permission on the HOSTS file and resets it so that administrators can access it.
09/19/12: Rkill version 2.4.2
- Will no longer issue a warning about the WinDefend service not running with Microsoft Security Essentials is installed.
- Will no longer issue a warning about the presence of HKLM\SOFTWARE\Microsoft\Windows Defender "DisableAntiSpyware" when Microsoft Security Essentials is installed.
11/02/12: Rkill version 2.4.4
- Enabled support for Windows 8.
01/16/13: Rkill version 2.4.6
- More support for Windows 8.
05/27/13: Rkill version 2.5.0
- Added Junction/Reparse Point detection for ZeroAccess and other malware.
- Fixed an issue with the FontCache service not being detected properly due to more than one correct imagepath.
- Cleaned up system file impersonator code
05/30/13: Rkill version 2.5.1
- Fixed a bug where unsigned system files were being killed and causing Windows to go into a restart countdown. Unsigned system files are indicative of an issue, but they should not be terminated due to the restarting of Windows.
05/31/13: Rkill version 2.5.2
- Fixed an issue with the msiserver service not being detected properly due to more than one correct imagepath.
06/03/13: Rkill version 2.5.2
- Added -s, -l, and -h command line arguments. Use -h to see the help file and what each argument does.
07/12/13: Rkill version 2.5.5
- Much better ZeroAccess file path detection
- Better ZA reparse point detection
- Replacement files for patched services will now show their md5 sum
06/19/14: Rkill version 2.6.7
- Added more Image File Execution Options entries to be cleaned.
- Modified one of the process termination routines to properly match processes running from non-standard Windows folder names
08/17/15: Rkill version 2.8
- Full support for Windows 10 is included
Edited by Grinler, 03 March 2020 - 08:36 PM.
Version 2.8




 Back to top
Back to top










