Signal messenger has investigated rumors spreading online over the weekend of a zero-day security vulnerability related to the 'Generate Link Previews' feature, stating that there is no evidence this vulnerability is real.
This statement comes after numerous sources told BleepingComputer and reported on Twitter that a new zero-day vulnerability allowed for a full takeover of devices.
After contacting Signal about the zero-day last night, they released a statement on Twitter stating that they have investigated the rumors and have found no evidence that this flaw is real.
"PSA: we have seen the vague viral reports alleging a Signal 0-day vulnerability," reads a statement on Twitter.
"After responsible investigation *we have no evidence that suggests this vulnerability is real* nor has any additional info been shared via our official reporting channels."
"We also checked with people across US Government, since the copy-paste report claimed USG as a source. Those we spoke to have no info suggesting this is a valid claim,"
Citing US government sources, news of the alleged zero-day quickly spread online and among the cybersecurity community Saturday afternoon.
These unnamed USG sources said that the vulnerability could be mitigated by disabling the 'Generate Link Previews' setting in Signal.
Source: BleepingComputer
However, BleepingComputer could not confirm the validity of these statements, even though we heard it from numerous people claiming the same sources.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has also stated that they have no information on a zero-day targeting Signal
"At this time, CISA does not have any information corroborating a zero-day vulnerability affecting Signal," a CISA spokesperson told BleepingComputer.
While Signal has stated that they have no evidence of a new zero-day, they still request that those with new and "real" info contact their security team.
As this is an ongoing investigation, and the mitigation is to simply disable the Link Previews feature, users may want to turn this setting off for the time being until it's fully confirmed not to be real.
Signal zero-days in high demand
Signal zero-day bugs are highly sought after by vulnerability brokers, who are willing to pay a hefty amount for flaws that can lead to remote code execution on devices.
Zero-day broker Zerodium offers up to $500,000 for a zero-day Signal exploit chain, leading to privilege escalation and remote code execution.
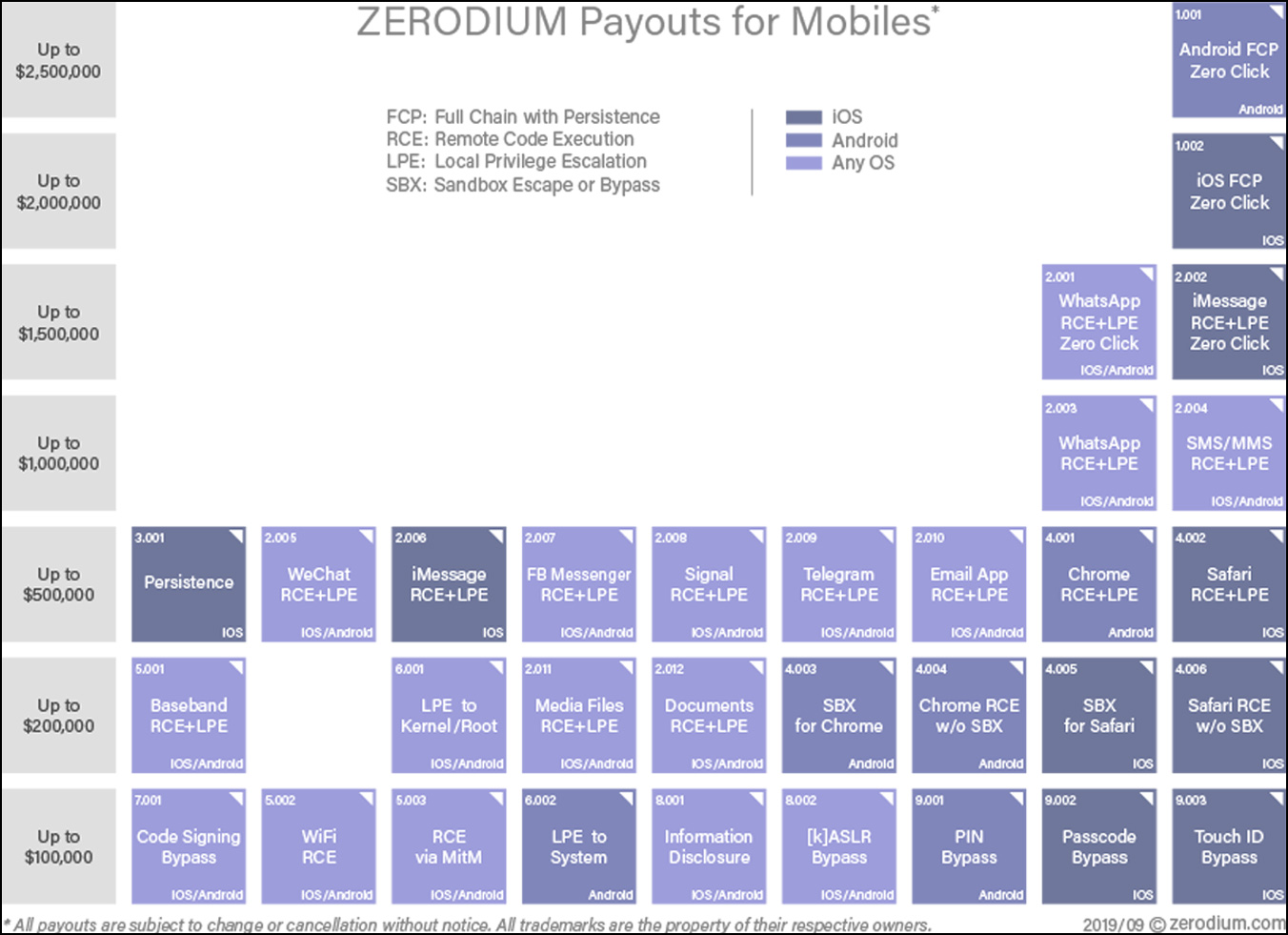
Source: Zerodium
However, Russian zero-day broker Operation Zero is willing to pay as high as $1.5 million for a Signal zero-day remote code execution vulnerability.
While both vulnerability brokers sell acquired zero-day flaws to private corporations and government agencies, Operation Zero only sells to Russian entities.
Zero-day vulnerabilities for mobile apps and operating systems are in high demand as spyware developers commonly use them to install their software on mobile devices.
These services have been found to be used by entities, including government agencies, to monitor the activities of journalists, activists, and politicians.



Comments
blackhatcat - 8 months ago
the linked tweet is deleted