
Security researchers developed a new attack, which they named AutoSpill, to steal account credentials on Android during the autofill operation.
In a presentation at the Black Hat Europe security conference, researchers from the International Institute of Information Technology (IIIT) at Hyderabad said that their tests showed that most password managers for Android are vulnerable to AutoSpill, even if there is no JavaScript injection.
How AutoSpill works
Android apps often use WebView controls to render web content, such as login pages within the app, instead of redirecting the users to the main browser, which would be a more cumbersome experience on small-screen devices.
Password managers on Android use the platform’s WebView framework to automatically type in a user's account credentials when an app loads the login page to services like Apple, Facebook, Microsoft, or Google.
The researchers said that it is possible to exploit weaknesses in this process to capture the auto-filled credentials on the invoking app, even without JavaScript injection.
If JavaScript injections are enabled, the researchers say that all password managers on Android are vulnerable to the AutoSpill attack.
Specifically, the AutoSpill issue stems from Android’s failure to enforce or to clearly define the responsibility for the secure handling of the auto-filled data, which can result in leaking it or being captured by the host app.
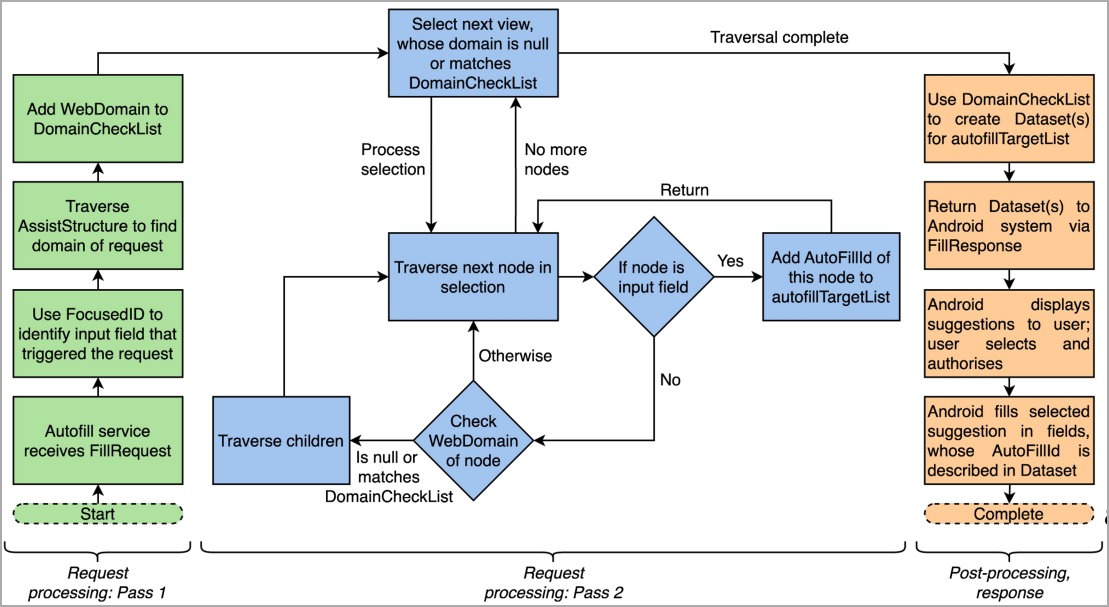
In an attack scenario, a rogue app serving a login form could capture the user’s credentials without leaving any indication of the compromise. Additional technical details about the AutoSpill attack are available in the researchers' slides from the Black Hat Europe presentation.
More details about the AutoSpill attack can be found in this document, which contains slides from the BlackHat presentation.
Impact and fixing
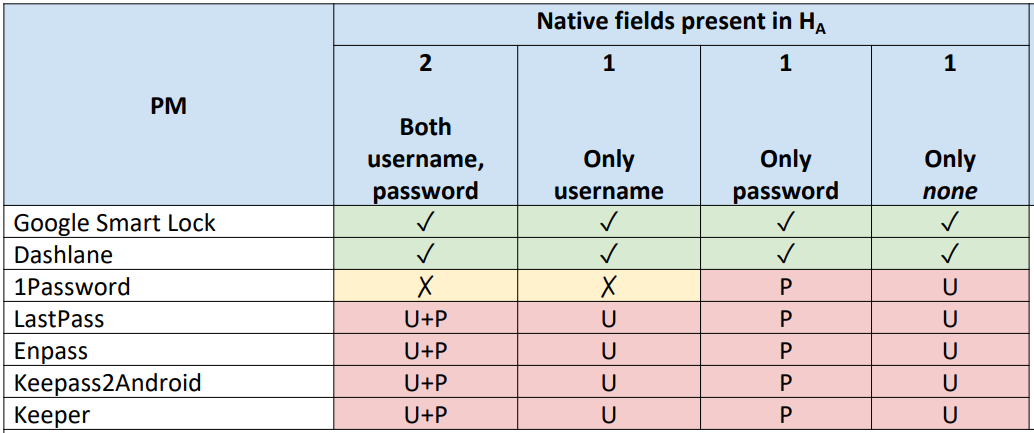
The researchers tested AutoSpill against a selection of password managers on Android 10, 11, and 12 and found that 1Password 7.9.4, LastPass 5.11.0.9519, Enpass 6.8.2.666, Keeper 16.4.3.1048, and Keepass2Android 1.09c-r0 are susceptible to attacks due to using Android’s autofill framework.
Google Smart Lock 13.30.8.26 and the DashLane 6.2221.3 followed a different technical approach for the autofill process. They did not leak sensitive data to the host app unless JavaScript injection was used.
The researchers disclosed their findings to impacted software vendors and Android’s security team and shared their proposals for addressing the problem. Their report was acknowledged as valid, but no details about fixing plans were shared.
BleepingComputer has contacted multiple providers of password management products that are impacted by AutoSpill, as well as Google, asking about their plans to address the issue and we received the following comments so far:
Many people have become accustomed to using autofill to quickly and easily enter their credentials. Through a malicious app installed on the user's device, a hacker could lead a user to unintentionally autofill their credentials. AutoSpill highlights this problem.
Keeping our customers’ most important data safe is our utmost priority at 1Password. A fix for AutoSpill has been identified and is currently being worked on.
While the fix will further strengthen our security posture, 1Password’s autofill function has been designed to require the user to take explicit action.
The update will provide additional protection by preventing native fields from being filled with credentials that are only intended for Android’s WebView. - Pedro Canahuati, CTO of 1Password
In 2022, we engaged with Dr. Gangwal via Bugcrowd, our bug bounty program partner. We analyzed the findings he submitted and found it to be a low-risk vulnerability due to the mechanisms required for it to be exploited.
What’s important to note here is that this vulnerability requires the ability and opportunity to install a malicious app on the target device, which would indicate a complete compromise or the ability to execute code on the targeted device.
Prior to receiving Dr. Gangwal’s findings, LastPass already had a mitigation in place via an in-product pop-up warning when the app detected an attempt to leverage the exploit. After analyzing the findings, we added more informative wording in the pop-up.
We confirmed this update with Dr. Gangwal but did not receive any acknowledgement of our update. - LastPass spokesperson
On May 31, 2022, Keeper received a report from the researcher about a potential vulnerability. We requested a video from the researcher to demonstrate the reported issue. Based upon our analysis, we determined the researcher had first installed a malicious application and subsequently, accepted a prompt by Keeper to force the association of the malicious application to a Keeper password record.
Keeper has safeguards in place to protect users against automatically filling credentials into an untrusted application or a site that was not explicitly authorized by the user. On the Android platform, Keeper prompts the user when attempting to autofill credentials into an Android application or website. The user is asked to confirm the association of the application to the Keeper password record prior to filling any information. On June 29, we informed the researcher of this information and also recommended that he submit his report to Google since it is specifically related to the Android platform.
Generally, a malicious Android application would first need to be submitted to Google Play Store, reviewed by Google and subsequently, approved for publication to the Google Play Store. The user would then need to install the malicious application from Google Play and transact with the application. Alternatively, the user would need to override important security settings on their device in order to sideload a malicious application.
Keeper always recommends that individuals be cautious and vigilant about the applications they install and should only install published Android applications from trusted app stores such as the Google Play Store. - Craig Lurey, CTO and co-founder of Keeper Security
WebView is used in a variety of ways by Android developers, which include hosting login pages for their own services in their apps. This issue is related to how password managers leverage the autofill APIs when interacting with WebViews.
We recommend third-party password managers be sensitive as to where passwords are being inputted, and we have WebView best practices that we recommend all password managers implement. Android provides password managers with the required context to distinguish between native views and WebViews, as well as whether the WebView being loaded is not related to the hosting app.
For example, when using the Google Password Manager for autofill on Android, users are warned if they are entering a password for a domain Google determines may not be owned by the hosting app, and the password is only filled in on the proper field. Google implements server side protections for logins via WebView. - Google spokesperson
Ankit Gangwal from the research team at the Indian Institutes of Information Technology reached out to us in June 2022 about the AutoSpill vulnerability in the Android Autofill framework. That vulnerability was subsequently patched in Enpass 6.8.3, released September 29, 2022. - Enpass spokesperson



Comments
L0g1calmadn3ss - 6 months ago
No Bitwarden test?
MtnDooDoo - 6 months ago
Was wondering the same thing myself as well as with the MS authenticator app.
lukastesar - 6 months ago
<p>Bitwarden is not vulnerable, because it's a good peace of software, as opposed to those mentioned in the article. It never fills in fully automatically so it can't be exploited that way.</p>