It is bad enough when a ransomware infection encrypts your data and demands a ransom, but it's even worse when shoddy programming destroys it instead. This is what happened in a new variant of the Power Worm ransomware where bad programming encrypts your data using AES encryption and then throws away the key. Since the decryption key was not properly initialized and not saved, a victim's files become unrecoverable even if they wanted to pay the ransom. Therefore, if you are a victim of this infection, DO NOT pay the ransom as it will not help you recover your files.
At BleepingComputer we never disclose bugs in a ransomware infection as that will just alert the developer and cause them to fix the weakness. In this particular case, though, we are going to tell the developer how to fix his mistake so that he doesn't continue to destroy his victim's data going forward. In our opinion, if a person becomes infected, we would rather they have a fighting chance of recovering their files rather than no chance at all.
After receiving the sample from White Hat Mike, one of our resident malware researchers, and further analysis by, Nathan Scott, it was discovered that there is a flaw in how this ransomware initializes the AES encryption engine. This developer planned on using a static AES key for all of his victims. Since everyone would have the same decryption key, this would allow the developer to have one decryptor that would work for everyone rather than having to manage a intricate payment site and decryption engine. The problem is that the AES key was not properly padded when it was converted into a Base64 string. When the PowerShell script tried to decode this string, it failed, and instead of the variable $RgDhcxSdghWd containing his decoded AES string, it now contained a NULL or empty value. If he had added one one more = character to the string, it would have worked as intended and everyone would have had the same AES key.
Unfortunately, since the above variable had a NULL value, when he attempted to use it to initialize the AES cryptography API, the API instead created a random key for every victim.
As the developer thought he that knew the key that was being used, this random key was never saved and there is no way to recover it in the future. That one little missing "=" character irretrievably destroyed a victim's data. If the malware dev had simply tested (what a crazy concept) his infection, then this mess wouldn't have happened. Instead the victim's would have had their data encrypted with a static AES key, which would have given us a chance of recovering their files.
So the sad news is that for anyone who was affected by this ransomware, there is nothing that can be done to retrieve your files and your only option is restore from a backup. For those who want a little more information on how this PowerShell ransomware works, please read below.
Technical Details:
This new ransomware was developed in PowerShell and is a small 54 line script. When executed, it first deletes your shadow volume copies so that you are unable to use them to restore your files.

It will then use the PowerShell GDR command and filter its output for only drives that show free space. This allows the script to get a list of drives that are writable.
$VxRgsjfThsnvHjh=gdr|where {$_.Free}|Sort-Object -Descending
It then scans this list of drives for data files that match the following extensions and encrypts them using a randomly generated AES encryption key. Unfortunately this key is not saved or transmitted to the developer and thus lost after the script terminates.
*.pdf,*.xls,*.docx,*.xlsx,*.mp3,*.waw,*.jpg,*.jpeg,*.txt,*.rtf,*.doc,*.rar,*.zip,*.psd,*.tif,*.wma,*.gif,*.bmp,*.ppt,*.pptx,*.docm,*.xlsm,*.pps,*.ppsx,*.ppd,*.eps,*.png,*.ace,*.djvu,*.tar,*.cdr,*.max,*.wmv,*.avi,*.wav,*.mp4,*.pdd,*.php,*.aac,*.ac3,*.amf,*.amr,*.dwg,*.dxf,*.accdb,*.mod,*.tax2013,*.tax2014,*.oga,*.ogg,*.pbf,*.ra,*.raw,*.saf,*.val,*.wave,*.wow,*.wpk,*.3g2,*.3gp,*.3gp2,*.3mm,*.amx,*.avs,*.bik,*.dir,*.divx,*.dvx,*.evo,*.flv,*.qtq,*.tch,*.rts,*.rum,*.rv,*.scn,*.srt,*.stx,*.svi,*.swf,*.trp,*.vdo,*.wm,*.wmd,*.wmmp,*.wmx,*.wvx,*.xvid,*.3d,*.3d4,*.3df8,*.pbs,*.adi,*.ais,*.amu,*.arr,*.bmc,*.bmf,*.cag,*.cam,*.dng,*.ink,*.jif,*.jiff,*.jpc,*.jpf,*.jpw,*.mag,*.mic,*.mip,*.msp,*.nav,*.ncd,*.odc,*.odi,*.opf,*.qif,*.xwd,*.abw,*.act,*.adt,*.aim,*.ans,*.asc,*.ase,*.bdp,*.bdr,*.bib,*.boc,*.crd,*.diz,*.dot,*.dotm,*.dotx,*.dvi,*.dxe,*.mlx,*.err,*.euc,*.faq,*.fdr,*.fds,*.gthr,*.idx,*.kwd,*.lp2,*.ltr,*.man,*.mbox,*.msg,*.nfo,*.now,*.odm,*.oft,*.pwi,*.rng,*.rtx,*.run,*.ssa,*.text,*.unx,*.wbk,*.wsh,*.7z,*.arc,*.ari,*.arj,*.car,*.cbr,*.cbz,*.gz,*.gzig,*.jgz,*.pak,*.pcv,*.puz,*.r00,*.r01,*.r02,*.r03,*.rev,*.sdn,*.sen,*.sfs,*.sfx,*.sh,*.shar,*.shr,*.sqx,*.tbz2,*.tg,*.tlz,*.vsi,*.wad,*.war,*.xpi,*.z02,*.z04,*.zap,*.zipx,*.zoo,*.ipa,*.isu,*.jar,*.js,*.udf,*.adr,*.ap,*.aro,*.asa,*.ascx,*.ashx,*.asmx,*.asp,*.indd,*.asr,*.qbb,*.bml,*.cer,*.cms,*.crt,*.dap,*.htm,*.moz,*.svr,*.url,*.wdgt,*.abk,*.bic,*.big,*.blp,*.bsp,*.cgf,*.chk,*.col,*.cty,*.dem,*.elf,*.ff,*.gam,*.grf,*.h3m,*.h4r,*.iwd,*.ldb,*.lgp,*.lvl,*.map,*.md3,*.mdl,*.mm6,*.mm7,*.mm8,*.nds,*.pbp,*.ppf,*.pwf,*.pxp,*.sad,*.sav,*.scm,*.scx,*.sdt,*.spr,*.sud,*.uax,*.umx,*.unr,*.uop,*.usa,*.usx,*.ut2,*.ut3,*.utc,*.utx,*.uvx,*.uxx,*.vmf,*.vtf,*.w3g,*.w3x,*.wtd,*.wtf,*.ccd,*.cd,*.cso,*.disk,*.dmg,*.dvd,*.fcd,*.flp,*.img,*.iso,*.isz,*.md0,*.md1,*.md2,*.mdf,*.mds,*.nrg,*.nri,*.vcd,*.vhd,*.snp,*.bkf,*.ade,*.adpb,*.dic,*.cch,*.ctt,*.dal,*.ddc,*.ddcx,*.dex,*.dif,*.dii,*.itdb,*.itl,*.kmz,*.lcd,*.lcf,*.mbx,*.mdn,*.odf,*.odp,*.ods,*.pab,*.pkb,*.pkh,*.pot,*.potx,*.pptm,*.psa,*.qdf,*.qel,*.rgn,*.rrt,*.rsw,*.rte,*.sdb,*.sdc,*.sds,*.sql,*.stt,*.t01,*.t03,*.t05,*.tcx,*.thmx,*.txd,*.txf,*.upoi,*.vmt,*.wks,*.wmdb,*.xl,*.xlc,*.xlr,*.xlsb,*.xltx,*.ltm,*.xlwx,*.mcd,*.cap,*.cc,*.cod,*.cp,*.cpp,*.cs,*.csi,*.dcp,*.dcu,*.dev,*.dob,*.dox,*.dpk,*.dpl,*.dpr,*.dsk,*.dsp,*.eql,*.ex,*.f90,*.fla,*.for,*.fpp,*.jav,*.java,*.lbi,*.owl,*.pl,*.plc,*.pli,*.pm,*.res,*.rsrc,*.so,*.swd,*.tpu,*.tpx,*.tu,*.tur,*.vc,*.yab,*.8ba,*.8bc,*.8be,*.8bf,*.8bi8,*.bi8,*.8bl,*.8bs,*.8bx,*.8by,*.8li,*.aip,*.amxx,*.ape,*.api,*.mxp,*.oxt,*.qpx,*.qtr,*.xla,*.xlam,*.xll,*.xlv,*.xpt,*.cfg,*.cwf,*.dbb,*.slt,*.bp2,*.bp3,*.bpl,*.clr,*.dbx,*.jc,*.potm,*.ppsm,*.prc,*.prt,*.shw,*.std,*.ver,*.wpl,*.xlm,*.yps,*.md3,*.1cd
For each folder that it encrypts a file, it will also create a ransom note called DECRYPT_INSTRUCTION.html. This ransom note is a copy of Cryptowall's, but the developer adds his own warnings to the bottom that state your ransom price will go up if you don't pay quickly. This ransom note also includes an ID that is supposedly unique to the victim. In reality this ID is the same for everyone and can be ignored.
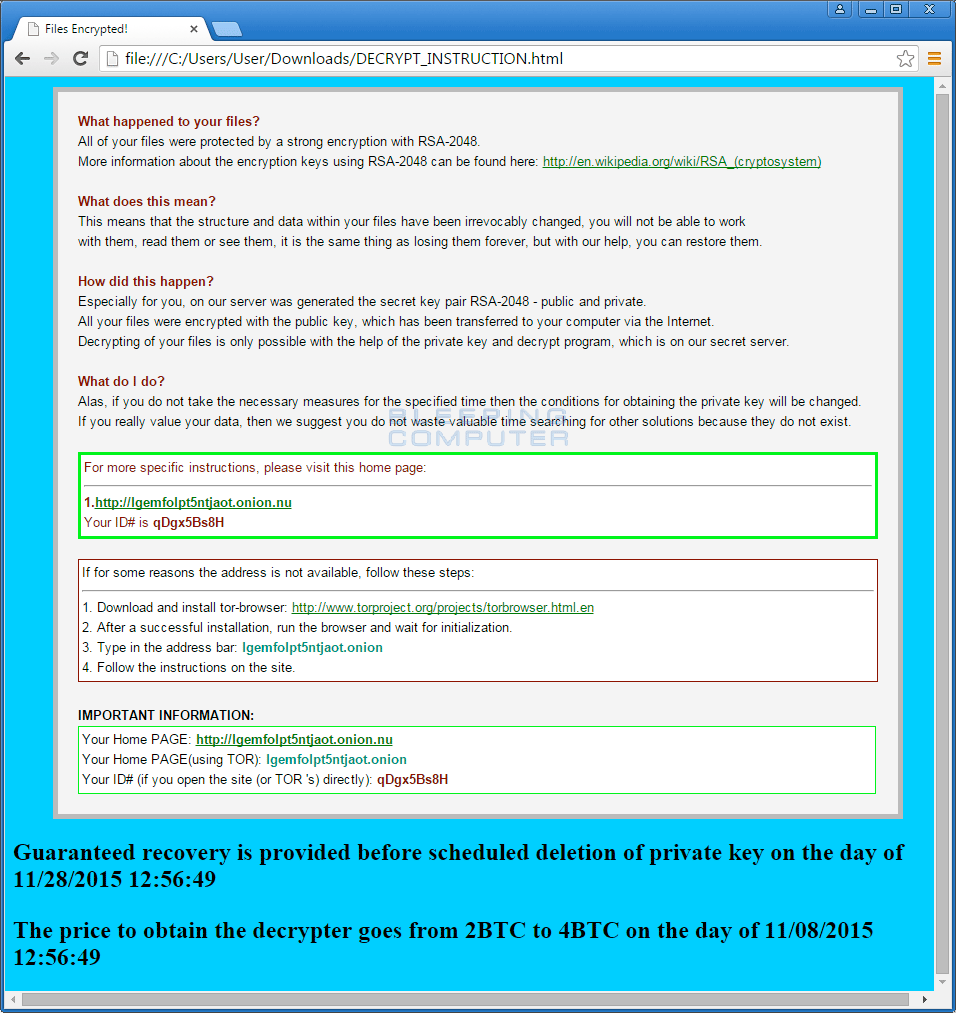
This ransom note also contains links to the payment sites, which are currently lgemfolpt5ntjaot.onion.nu or lgemfolpt5ntjaot.onion. A picture of the payment site can be seen below.

As already stated, there is unfortunately nothing that can be done for victims of this infection. If you have been affected by this ransomware, your only option is to restore from a backup.



Comments
blueelvis - 8 years ago
This is the first time I am seeing when a ransomware is developed in Powershell.
Lawrence Abrams - 8 years ago
There was also these:
https://www.bleepingcomputer.com/forums/t/530294/poshcoder-malware-removal/
https://www.bleepingcomputer.com/forums/t/575975/the-el-polocker-ransomware-is-no-chicken-as-it-encrypts-your-drives-and-shares/
https://www.bleepingcomputer.com/forums/t/544502/how-to-decrypt-powershell-ransomware-flaw-makes-recovery-impossible/
Alexstrasza - 8 years ago
The ransom note of this one is similar to the How-To-Decrypt PowerShell ransomware that also destroys peoples data by a mistake in the coding.
Maybe it came from the same person?
blueelvis - 8 years ago
Oh thanks. I failed to notice those articles.
Nikhil_CV - 8 years ago
Even-though its a good thing to see it broken down, this trend of making errors in code (for victims) and appreciating indirectly the stupidness of dev is not so nice.....
IMO
Lawrence Abrams - 8 years ago
How are we appreciating the dev?