-
PadCrypt Updated with Additional Chat Features and a Computer Blacklist
A new version of PadCrypt has been released that includes an updated live support chat, blacklisted computer names, and a new decrypter. This ransomware is actively being supported, updated, and evolving and is one that we need to keep an eye on.
- February 24, 2016
- 01:29 PM
 4
4
-
CTB-Locker for Websites: Reinventing an old Ransomware
CTB-Locker is one of the older ransomware projects that has been in circulation. This month they have reinvented themselves by releasing a CTB-Locker version that only targets and encrypts websites. Ransomware developers targeting companies is becoming the norm and it looks like CTB-Locker did not want to be left behind.
- February 23, 2016
- 06:22 PM
 2
2
-
The PadCrypt Ransomware is still Alive and Kicking
The PadCrypt ransomware is still alive and being actively distributed by the developer. A new sample of the PadCrypt ransomware has been discovered that utilizes a functional Command & Control server that is encrypting victims and being used to sent chat messages to the victims.
- February 17, 2016
- 05:25 PM
 2
2
-
The Locky Ransomware Encrypts Local Files and Unmapped Network Shares
A new ransomware has been discovered called Locky that encrypts your data using AES encryption and then demands .5 bitcoins to decrypt your files. Though the ransomware sounds like one named by my sons, there is nothing childish about it.
- February 16, 2016
- 05:22 PM
 178
178
-
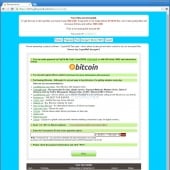
PadCrypt: The first ransomware with Live Support Chat and an Uninstaller
A new ransomware called PadCrypt was discovered that for the first time comes with a live support chat and an uninstaller. Though the command and control servers are currently down, and thus the ransomware is broken, these new features add a new level functionality to existing ransomware.
- February 14, 2016
- 01:50 PM
 3
3
-
Emsisoft Releases a Decrypter for HydraCrypt and UmbreCrypt Ransomware
Fabian Wosar of Emisoft has done it again with his release of a decrypter for the HydraCrypt and UmbreCrypt ransomware infections. Both of these infections are part of the CrypBoss Ransomware family, whose source code was leaked on pastebin last year.
- February 14, 2016
- 09:08 AM
 0
0
-
New TeslaCrypt variant now uses the .MP3 Extension
A new variant of the TeslaCrypt ransomware was released that contains some minor changes. The version number is still 3.0. but the ransom notes have been renamed and the file extension for encrypted files is now .MP3. Unfortunately, there is still no way to decrypt this latest version of TeslaCrypt.
- February 12, 2016
- 10:53 AM
 34
34
-
UmbreCrypt Ransomware manually installed via Terminal Services
A new CrypBoss ransomware variant has been released called UmbreCrypt. This ransomware family encrypts a victim's data with AES encryption and then requires them to email the developers for payment instructions. At this time there is no way to decrypt these files for free,
- February 10, 2016
- 10:51 AM
 5
5
-
Google is giving away extra Google Drive Storage for performing a Security Checkup
In honor of Safer Internet Day, Google is giving away 2GB of extra storage for completing their Security Checkup. This checkup will walk you through a series of checks to make sure you are using Google in the most secure manner possible.
- February 09, 2016
- 07:21 PM
 1
1
-
Oracle, Adobe, and Microsoft Release Updates for Critical Vulnerabilities
Today Microsoft, Oracle, and Adobe all released security updates for critical vulnerabilities in their products. Critical vulnerabilities allow attackers to execute commands on the vulnerable computers that could allow them to download and installer further programs without your permission.
- February 09, 2016
- 06:33 PM
 0
0
-
DMA Locker Ransomware targets Unmapped Network Shares
A new ransomware called DMA Locker was discovered by a Malwarebytes researcher last week. One feature that has not been discussed yet is its ability to encrypt files located on unmapped network shares. Thankfully, earlier versions of this ransomware can be decrypted for free using a utility by Fabian Wosar of Emsisoft.
- February 08, 2016
- 02:16 PM
 5
5
-
NanoLocker Ransomware can be Decrypted if Caught Early
A new ransomware was discovered last week that incorporates some interesting features such as ICMP communication with Command & Control server and a unique payment/key retrieval mechanism. This ransom also has a flaw in its key storage method that could allow user's to retrieve their decryption key under the right circumstances.
- February 04, 2016
- 12:55 PM
 2
2
-
7ev3n Ransomware trashes your PC and then demands 13 Bitcoins
A new ransomware has been spotted called 7ev3n that encrypts your data and demands 13 bitcoins to decrypt your files. A 13 bitcoin ransom demand is the largest we have seen to date for this type of infection, but this ransomware also has another surprise as it does a good job trashing your system.
- January 26, 2016
- 05:45 PM
 10
10
-
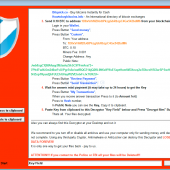
Emsisoft releases Decrypter for the LeChiffre Ransomware
A vulnerability for the LeChiffre ransomware has been discovered that allows Fabian Wosar of Emsisoft to create a free decryptor for it. This articles explains how to use the decrypter to recover files encrypted by LeChiffre for free.
- January 25, 2016
- 11:52 PM
 9
9
-
Malwarebytes releases new Anti-Ransomware Beta Software
Today Malwarebytes released their latest security offering called Malwarebytes Anti-Ransomware. Malwarebytes Anti-Ransomware, or MBARW for short, is currently in beta and is a small utility that runs in the background while quietly monitoring computer for behavior associated with file encrypting ransomware.
- January 25, 2016
- 10:27 PM
 10
10
-
Hidden Tear Ransomware Developer Blackmailed by Malware Developers using his Code
In a post on the BleepingComputer.com forums, the developer of the Magic Ransomware infection is blackmailing the author of the open source Hidden Tear and EDA2 Ransomware Project. The malware developer's demands are simple; take down the Hidden Tear project or their Magic ransomware's victims lose their keys forever.
- January 25, 2016
- 06:58 PM
 1
1
-
New Magic Ransomware developed from open source EDA2 Ransomware
A new ransomware has been discovered that utilizes the open source ransomware kit called eda2. This ransomware will encrypt your data with AES encryption, append the .magic extension to encrypted files, and then demand 1 bitcoin to decrypt your data.
- January 23, 2016
- 09:37 AM
 1
1
-
TeslaCrypt Decrypted: Flaw in TeslaCrypt allows Victim's to Recover their Files
Now that TeslaCrypt 3.0 has been released and the malware developer has fixed a flaw in his program, we are releasing information on how to decrypt files encrypted by earlier variants. This article explains how volunteers cracked TeslaCrypt's encryption key storage algorithm to help people recover their files for free.
- January 20, 2016
- 08:15 AM
 44
44
-
Apple Releases Security Updates for Safari, iOS, and OS X
Apple released security updates today for Safari, OS X, and iOS that resolve critical vulnerabilities that could lead to remote code execution. Remote code execution vulnerabilities allow an attacker to create specially crafted web sites or files that could allow the attacker to execute commands and programs on vulnerable platforms.
- January 19, 2016
- 06:34 PM
 1
1
-
Get Updating! Microsoft and Adobe release Critical Updates
Today Microsoft and Adobe both released updates for numerous critical remote code execution vulnerabilities in their products. It is strongly advised that every Windows, Adobe Acrobat, and Adobe Reader user install these updates immediately.
- January 12, 2016
- 07:23 PM
 1
1
 2
2