Malware researchers have noticed a new tool that helps cybercriminals build malicious .LNK files to deliver payloads for the initial stages of an attack.
LNKs are Windows shortcut files that can contain malicious code to abuse legitimate tools on the system, the so-called living-off-the-land binaries (LOLBins), such as PowerShell or the MSHTA that is used to execute Microsoft HTML Application (HTA) files.
Due to this, LNKs are extensively used for malware distribution, especially in phishing campaigns, with some notable malware families currently using them being Emotet, Bumblebee, Qbot, and IcedID.
Quantum LNK builder
Researchers at Cyble have spotted a new tool for creating malicious LNKs called Quantum, which features a graphical interface and offers convenient file building through a rich set of options and parameters (e.g. extension spoofing, icon selection from over 300 available options).
The tool is rented for €189 per month, €335 for two months, €899 for six months, or single payment of €1,500 for lifetime access.
Quantum offers UAC bypass, Windows Smartscreen bypass, the ability to load multiple payloads on a single LNK file, post-execution hiding, startup or delayed execution.
Its authors claim files generated with Quantum are 100% FUD, or fully undetectable, indicating that antivirus engines and OS protection mechanisms fail to flag them as suspicious or dangerous.
Finally, Quantum also offers the option to build HTA files and ISO archives, which typically go hand in hand in attacks involving LNK, with everything bundled inside the disk image files.
Another interesting feature of Quantum is the implementation of a dogwalk n-day exploit in the Microsoft Support Diagnostic Tool (MSDT), which uses a .diagcab file to perform arbitrary code execution.
Ties to Lazarus
Cyble’s analysis of recent LNK samples captured in the wild indicates that notorious APT gangs like Lazarus might be using Quantum for their attacks.
The particular file used in the campaign is “Password.txt.lnk”, which appears as a text file with a password for a protected PDF document that supposedly offers a stablecoin analysis.
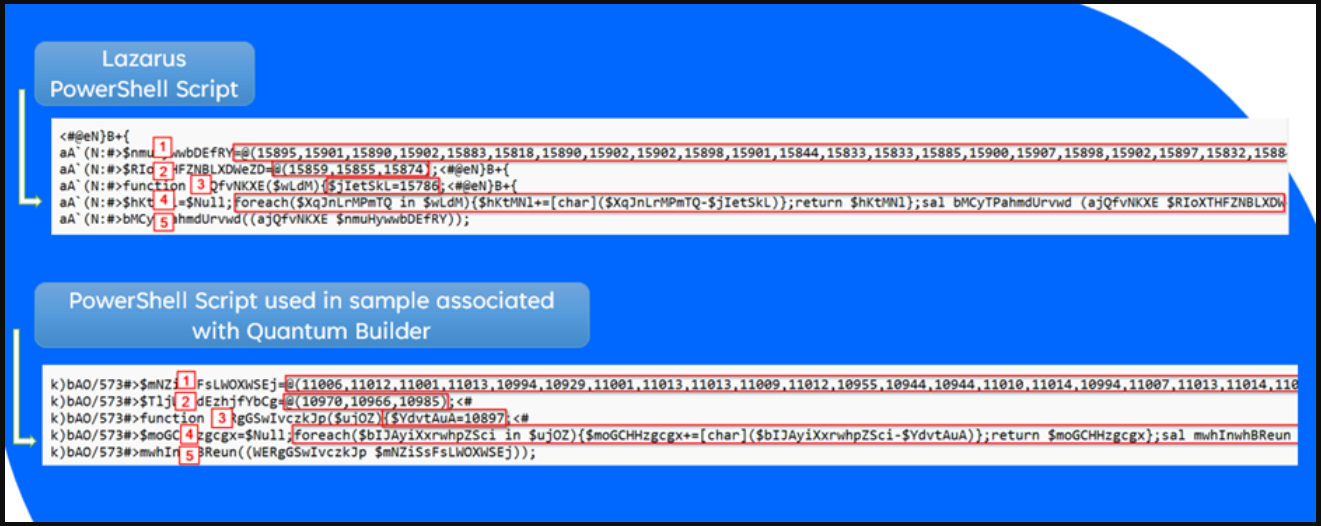
The PowerShell script that executes upon opening the LNK file is very similar to scripts used by Lazarus in recent campaigns, indicating a possible connection.
As long as using LNK files is effective for malicious actors, the rising trend in their deployment is expected to continue.
Tools like Quantum are accelerating the adoption trend even more and make the choice of LNK files more enticing to cybercriminals.
Users are advised to remain vigilant and scan all files they receive via email on an anti-virus tool before executing them.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now