Shadow Volume Copies have been a feature since Windows Vista that allows snapshots, or backups, of your files to be saved even when the files are currently in use. These snapshots will attempt to be created every day and allows you to restore documents to previous versions or even to restore them if they were deleted.
This same technology is also used by the Windows' System Restore feature that allows you to roll back Windows to a previously working configuration in case there is a problem. Since Windows Vista, Microsoft has been bundling a utility called vssadmin.exe in Windows that allows an administrator to manage the Shadow Volume Copies that are on the computer. Unfortunately, with the rise of Crypto Ransomware, this tool has become more of a problem than a benefit and everyone should disable it.
System Restore is a feature that relies on Shadow Volume Copies
By default, Windows will attempt to create new Shadow Volume snapshots of your C: drive every day. Since the standard save location for Document files is on the C: drive your documents will be backed up as well. Though this shouldn't be considered a regular backup method, it does provide an extra security blanket in the event that you need to restore a changed or deleted file. Unfortunately, the developers of Crypto Ransomware are aware of Shadow Volume Copies and design their infections so that they delete ALL Shadow Volume Copies when the ransomware infects your computer. This is done to prevent you from using Shadow Volumes to recover encrypted files.
There are a few methods that the ransomware malware developers use to delete the Shadow Volume Copies, but the most prevalent one is to use the vssadmin.exe Delete Shadows /All /Quiet command. This command will execute the vssadmin.exe utility and have it quietly delete all of the Shadow Volume Copies on the computer. As this program requires Administrative privileges to run, some ransomware will inject themselves into processes that are running as an Administrator in order to avoid a UAC prompt from being displayed.
As vssadmin.exe is not a tool that is routinely used by an administrator, it is strongly suggested that it be disabled it by renaming it. Then if a ransomware tries to utilize the program to delete your shadow volume snapshots, it will fail and you will be able to use them to recover your files. Will this be 100% effective against all ransomware infections? No,but it will help against a good amount of them.
Creating a task that schedules automatic restore point creation
The one downside to renaming vssadmin.exe is that it has been discovered that the program is used by Windows when it performs scheduled restore points. To work around this, we can create a scheduled task that issues a WMIC command that can create the restore points for us. This WMIC method does not rely on vssadmin and can be used to create a daily task to create restore points for protected drives. Please note that this task will only create restore points for drive that you have specifically enabled protection for.
The WMIC command that can be used is:
Wmic.exe /Namespace:\\root\default Path SystemRestore Call CreateRestorePoint "%DATE%", 100, 7
When creating the new scheduled task, create it as a New Task. Then in the General tab make sure you have it set to Run whether user is logged on or not and to Run with highest privileges as shown in the image below. These settings will prompt you to store your password so that it can run when you are not logged on. For those who want to use this task via GPO and can't push out the password to store, you can set it to Run only when user is logged on instead.
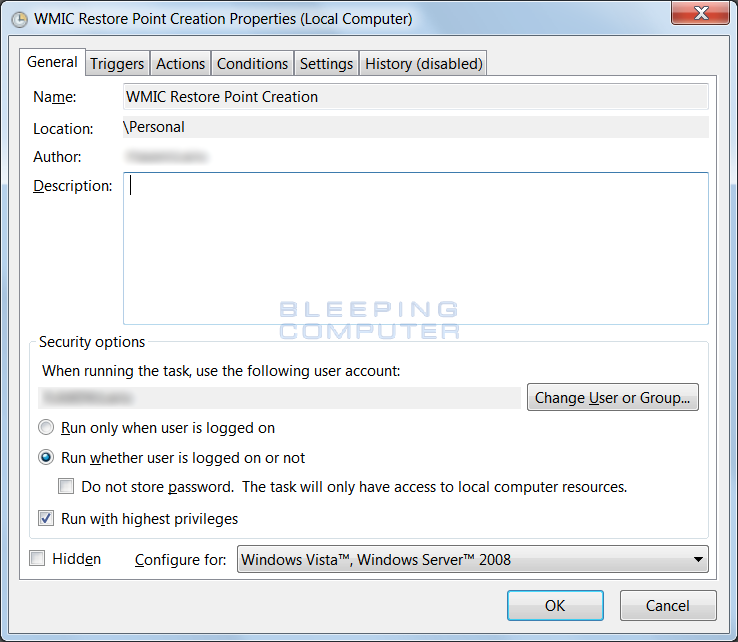
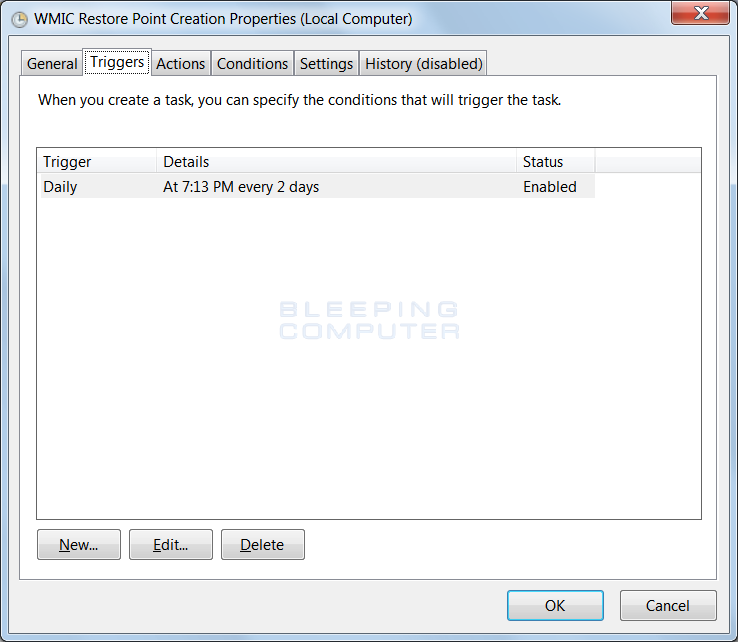
Then in the Triggers tab, set it to run as often as you want. I specified to have it execute every 2 days, but you can set it for daily or even more often as necessary for your environment.
Finally, in the Actions tab, click on the New button and then enter C:\Windows\System32\wbem\WMIC.exe into the Program/Script field. In the Add arguments field you want to enter /Namespace:\\root\default Path SystemRestore Call CreateRestorePoint "%DATE%", 100, 7. When it is done it should look like the image below.
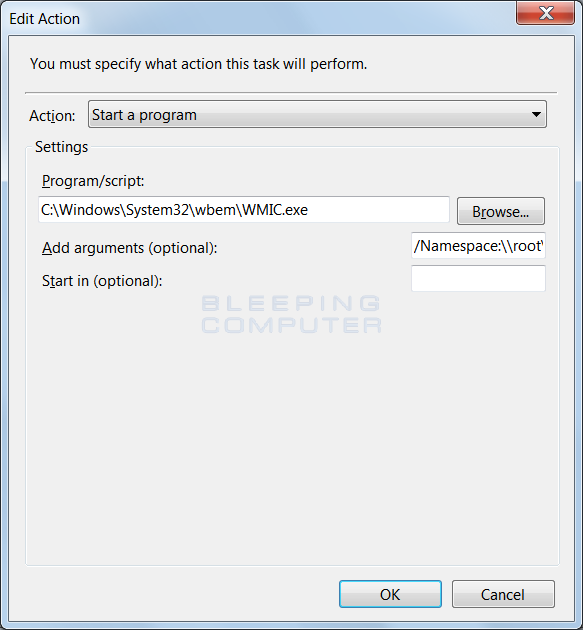
When the action is finished, you can then save the scheduled task and it should create new restore points at the times you specified. For those who wish to push this scheduled task via GPO, you can follow the steps in this article by Microsoft.
Now that we have a task to automatically create scheduled restore points, we can move ahead with renaming the vssadmin.exe program.
How to rename vssadmin
Unfortunately, as this file is owned by the special Windows account called TrustedInstaller, it is not a simple task to rename. In order to rename vssadmin.exe you first have take ownership of the file, give yourself the permissions to modify it, and then rename it. In order to make this task easier, I have put together a small batch file that does this for you. Renvbs.bat, which is shown below, will change the ownership of the vssadmin.exe file from TrustedInstaller to the Administrators group. It will then give the Administrators the Change permission so that they can rename it. Finally the batch file will rename the file in the format vssadmin.exe-date-time. Feel free to modify the name of the renamed file in the batch file for extra security.
In the future if you ever need to actually use this utility, you can just rename it back to vssadmin.exe and use it as normal. When testing this method, I have not found any functionality lost within Windows and the only program that I know of that no longer operates when it is renamed is Shadow Explorer. Once again, to resolve any issues that may come up, you simply need to rename the file back to vssadmin.exe.
The Renvbs.bat batch file can also be downloaded from here: http://download.bleepingcomputer.com/bats/renvss.bat.
The RenVBS Batch file:
@echo off
REM We are redirecting the output of the commands and any errors to NUL.
REM If you would like to see the output, then remove the 2>NUL from the end of the commands.
REM Check if vssadmin.exe exists. If not, abort the script
if NOT exist %WinDir%\system32\vssadmin.exe (
echo.
echo.%WinDir%\system32\vssadmin.exe does not exist!
echo.
echo Script Aborting!
echo.
PAUSE
goto:eof
)
REM Check if the script was started with Administrator privileges.
REM Method from http://stackoverflow.com/questions/4051883/batch-script-how-to-check-for-admin-rights
net session >nul 2>&1
if %errorLevel% NEQ 0 (
echo.
echo You do not have the required Administrator privileges.
echo.
echo Please run the script again as an Administrator.
echo.
echo Script Aborting!
echo.
PAUSE
goto:eof
)
REM We need to give the Administrators ownership before we can change permissions on the file
takeown /F %WinDir%\system32\vssadmin.exe /A >nul 2>&1
REM Give Administrators the Change permissions for the file
CACLS %WinDir%\system32\vssadmin.exe /E /G "Administrators":C >nul 2>&1
REM Generate the name we are going to use when rename vssadmin.exe
REM This filename will be based off of the date and time.
REM http://blogs.msdn.com/b/myocom/archive/2005/06/03/so-what-the-heck-just-happened-there.aspx
for /f "delims=/ tokens=1-3" %%a in ("%DATE:~4%") do (
for /f "delims=:. tokens=1-4" %%m in ("%TIME: =0%") do (
set RenFile=vssadmin.exe-%%c-%%b-%%a-%%m%%n%%o%%p
)
)
REM Rename vssadmin.exe to the filename in the RenFile variable
ren %WinDir%\system32\vssadmin.exe %RenFile% >nul 2>&1
REM Check if the task was completed successfully
if exist %WinDir%\system32\%RenFile% (
echo.
echo vssadmin.exe has been successfully renamed
echo to %WinDir%\system32\%RenFile%.
pause
) else (
echo.
echo There was a problem renaming vssadmin.exe
echo to %WinDir%\system32\%RenFile%.
echo.
pause
)
:END



Comments
XHero0 - 8 years ago
Question:
If you disable the file does it also disable to ability of windows to make restore points?
Joe M.
Lawrence Abrams - 8 years ago
No it does not. All Windows functionality appears to work fine. Only programs that act as a graphical front end to it, like Shadow Explorer, are affected.
XHero0 - 8 years ago
Ok cool thanx!
herbman - 8 years ago
Wow, thats a great and im sure very much appreciated thing you took the time to do to help all your members and visitors , so thanks for that .
My question is, i never store anything of importance on my computer and never have , if a ransomware got a hold of my computer i would just re format and re install .
I know the overwhelming majority of computer users do have important stuff on their computers however , so i know i am a very rare example i know.
Is this something everybody should do regardless or only for users who dont want to lose anything ?
Thank you very much
Foolish Tech - 8 years ago
Strongly agreed!! Blocking execution of vssadmin.exe has long since been an option in CryptoPrevent, but many may not know about it, which lives in the Advanced menu. This protection is applied with the Default and above protection levels.
Unfortunately, it may not be an option for some corp networks depending on what the admin is doing, but otherwise and for home users there really is no excuse.
Also as mentioned it also will interfere with Shadow Explorer, however users of CryptoPrevent can learn more and follow these visual directions on using Shadow Explorer with VSSADMIN.EXE disabled within CryptoPrevent: https://www.foolishit.com/2015/06/cryptoprevent-shadowexplorer-and-vssadmin/
Lawrence Abrams - 8 years ago
Though, I agree CryptoPrevent has become an essential tool these days, I still recommend you rename vssadmin.exe altogether. Its a very niche tool that that vast majority will never use but has a high risk to it.
Also, if a malware executes from a location that SRPs do not block, that malware could easily remove those SRPs by editing the registry. Safer, for this particular exec, to just rename it.
Foolish Tech - 8 years ago
Youre probably right, although actually the SRP CryptoPrevent uses blocks it no matter where in the file system it is run from, of course yeah that wont cut it if other malware is started to then remove SRPs. I think Brantley is too far along with the initial v8 release but it is probably a good idea to let him know that would be a good option for ppl in addition to our hash/folder watch scanning and SRP, for the next revision... Thanks!
SharQ - 8 years ago
So, if you do this on a server & then need to restore a file what would be the process for restoring the file? In other words, when a user needs a file restored often times we will restore from the Volume Shadow Copy because it is so fast, if a user calls & needs a Word Document Restored, what would be the process?
Lawrence Abrams - 8 years ago
What tool are you using to restore from the shadow volume copies? Renaming vssadmin.exe does not disable Shadow volume copies, system restore, or previous version. It is just renaming a tool commonly used by ransomware that allows you to manage volume shadow copies. If you do not use this tool, then you can safely rename it.
Uselesslight - 8 years ago
Im just a bit unclear as to why this advice should be taken. Its my understanding that disabling VSSADMIN wont actually prevent an infection from ransomware of any type. Its also stated that the variants of ransomware utilize a few different methods to delete volume shadow copies... Wouldnt disabling VSSADMIN just increase the chances of someone not being able to recover their data from a non ransomware related failure? I could see it being useful if the VSSADMIN was actually an attack vector and disabling it could help to prevent the infections. Considering thats not mentioned anywhere that Ive read, it seems like disabling VSSADMIN would cause more problems than it would solve? Thoughts?
Lawrence Abrams - 8 years ago
VSSadmin is an administrative tool to manipulate shadow copies. Renaming it It does not affect system restore or disable shadow volume copies. So if you are using system restore, previous versions, etc, they will continue to work the way they normally do.
With that said, renaming vssadmin has no affect unless you routinely use the tool All it does is make it so that a ransomware is unable to use it to remove shadow volume copies. Since a ransomware will not be able to use this tool, you now have an extra method of possibly recovering files in the event that you do become infected with ransomware.
Condobloke - 8 years ago
Are there any implications for backup software..??....macrium, acronis, etc etc
silumor - 8 years ago
if I disable it will my system be unable to removed old shadow copies when i reach my 10% as per the system restore? so Will my computer just fill up with old restore points?
MystShadow - 8 years ago
hmmm. most intriguing. I tried to do a system restore before Id downloaded some rather foolish driver extensions, and got a BSOD. And then the system (Vista) gave me a diagnostic that it couldnt roll back. Correlation?
Also, if ones remote feature to make changes on the computer is unchecked, do you think that might serve as some protection? (trust me, Im making the changes as we speak!)
**Thanks** :)
Lawrence Abrams - 8 years ago
Also, if ones remote feature to make changes on the computer is unchecked, do you think that might serve as some protection?
I am not sure what you are referring to here.
granada12 - 8 years ago
As you take ownership of vssadmin.exe cryptowall wont be able to encrypt Vssadmin?
Since your are now the owner the infection should have the right to do so? Correct me if im wrong but having Thrusted Intaller as the owner is not a thing to prevent unusable volume shadow copy?
Lawrence Abrams - 8 years ago
As it will be renamed, Ransomware that relies on it wont be able to use it because the file wont exist when they try to execute it.
Pat(rick) - 8 years ago
Nice, I just free 60 GB of memory on my Hard Drive by disabling the vssadmin.exe xD
Lawrence Abrams - 8 years ago
Renaming the file should not have freed up any space. You were just supposed to rename the file. Not delete shadow volume copies.
bilalinamdar - 8 years ago
"Nice, I just free 60 GB of memory on my Hard Drive by disabling the vssadmin.exe xD"
LOL !!!!!!
woolie - 8 years ago
<p>Many thanks to Foolish Tech for his wonderful program to stop the bad guys...</p>
techjohnny - 8 years ago
In a domain environment where Group Policies are being used, I would recommended in place of renaming this file to simply add a PATH rule that disallows running vssadmin.exe.
Lawrence Abrams - 8 years ago
As already stated, it is trivial for a malware that runs to remove that entry from the registry. Safer to rename. Most will never need to use this program.
techjohnny - 8 years ago
How can the malware remove entries from the registry it does not have access to remove? Unless your user is running as local administrator.
Any domain accounts that have local admin rights defeat having any sort of security for this very reason. Its the lazy admin way to give everybody local admin rights in my opinion.
BeckoningChasm - 8 years ago
Thanks to everyone for writing this tool and making it available. Ive downloaded it to most of our clients servers and well be installing it on workstations as well.
A question: can vssadmin be restored to its regular file name through a Windows update? I would think if its part of an update, and Windows doesnt see it, that Windows might just bring it back and wed be right back where we started.
Lawrence Abrams - 8 years ago
Good question. Yes, if a new update is released that has an updated version of this tool then it would be replaced.
BeckoningChasm - 8 years ago
Well, most of our clients are running Windows 7, so its unlikely that there will be a major update to that system--they may be safe until the PCs are replaced. Still, Ill keep an eye out. Maybe the batch file could be added to a login script, with the pauses removed.
techjohnny - 8 years ago
I believe if you are reading this article, its unlikely you would be fooled into actually executing the program that wipes out your shadow copies.
This might be a good idea for a family or friends computer.
Lawrence Abrams - 8 years ago
Unfortunately ransomware can be installed via exploit kits, so though you may be educated enough not to open an attachment, just having that slightly outdated program installed could be all that you need to be infected.
Akane - 8 years ago
Excuse me,I have a little question.
If I turn [ vssadmin.exe ] off
Will there be the ways to turn it back again ?
Lawrence Abrams - 8 years ago
Just rename it back to vssadmin.exe
Bob. - 8 years ago
Thanks! Nice to have for client machines. Ill be running the batch file on my systems regardless, but since I use Acronis and Macrium to run regular scheduled and manual backups, not really an issue here.
lightspeed11 - 8 years ago
thanx Grinler...you da man and thx for being patient with all the questions :)
rdennisak - 8 years ago
Thanks. This is a great idea. I actually had a client that got infected and it encrypted files on server shares. Fortunately, I was able to restore using Previous Versions on the server. So, apparently, that version of the virus was not able to get to vssadmin.exe over the network, but I think Ill do this on all the servers i manage, just in case. Hopefully, the bad guys wont start including vssadmin.exe in the payload.
MaxMil - 8 years ago
Hello, do you think it is important to also disable Windows Management Instrumentation (net stop winmgmt) to prevent XRT ransomware that create and execute a VBS script to Contain WMIC command That clears the shadow volumes...
ex.: objshell1.ShellExecute wmic.exe,shadowcopy delete /nointeractive,runas,0
Sorry for my bad english!!! ;)
Lawrence Abrams - 8 years ago
Unfortunately, I think that would cause a lot of issues.
MaxMil - 8 years ago
OK, thanks!!!
abdinho - 8 years ago
i have a little problem :
why !!!
http://i.imgur.com/4JcCRfN.png
Lawrence Abrams - 8 years ago
Strange error. When you checked was it renamed or not?
raoskidoo - 8 years ago
The solution is simple. He has a french version of Windows ( Appuyer sur une touche pour continuer ). So that means that Administrator is not found. Replace Administrator by Administrateur and everything will work as intented. :)
iliyanpi - 8 years ago
I fellow had the same problem and his access to any site was blocked by editing the shortcut to browser. Fortunatly he works on this PC as a user with limited rights (not as admin) and changes made by virus were only that said above and many times executable link to some F.exe. This shows that browsing on the WEB should be performed not as a administrator!
huntsin2 - 8 years ago
Hi,
I looked at the batch file, but where exactly would one rename the vssadmin.exe if they wanted to name it something else?
Lawrence Abrams - 8 years ago
This line is the renamed file:
set RenFile=vssadmin.exe-%%c-%%b-%%a-%%m%%n%%o%%p
Aron321 - 8 years ago
I have the same problem with the batch file.
http://i.imgur.com/4JcCRfN.png
Help?
Lawrence Abrams - 8 years ago
Are you running it as admin? right click on the batch file and select run as administrator.
Aron321 - 8 years ago
"Are you running it as admin? right click on the batch file and select run as administrator."
I ran the batch file as admin.
22029206 - 8 years ago
Change the file name to something else without those date and time stuff and it will work
raoskidoo - 8 years ago
The solution is simple. He has a french version of Windows ( Appuyer sur une touche pour continuer ). So that means that Administrator is not found. Replace Administrator by Administrateur and everything will work as intented. :)
maxamos - 8 years ago
After running the batch file the scheduled shadow copies on my servers no longer run, I can create a shadow copy by selecting the create now button and if I rename the vssadmin back to its original state all schedules resume. I use Configure Shadow Copies in windows manager, is there any way to configure schedules with the renamed vssadmin application?
TechworksConsulting - 8 years ago
"After running the batch file the scheduled shadow copies on my servers no longer run, I can create a shadow copy by selecting the create now button and if I rename the vssadmin back to its original state all schedules resume. I use Configure Shadow Copies in windows manager, is there any way to configure schedules with the renamed vssadmin application?"
We just found the same as well. If you run it manually, it works fine however if you have it scheduled at 7AM and 12PM (or whatever else) it will fail to run as it can't find the file.
Surprised that no one else has come across this until now since there wasn't supposed to be any adverse affects with these changes.
TechworksConsulting - 8 years ago
(Subscribing to email notifications as well)
Lawrence Abrams - 8 years ago
Thanks...will update the article. Now that we know that vssadmin.exe is required for daily restore points, we can instead create a task scheduler job to make them using this command:
Wmic.exe /Namespace:\\root\default Path SystemRestore Call CreateRestorePoint "%DATE%", 100, 7
TechworksConsulting - 8 years ago
"Thanks...will update the article. Now that we know that vssadmin.exe is required for daily restore points, we can instead create a task scheduler job to make them using this command:
Wmic.exe /Namespace:\\root\default Path SystemRestore Call CreateRestorePoint "%DATE%", 100, 7"
Could and article be written detailing these steps for multiple drives (System, Data, etc) as well as how it can be done via GP / Script. We have this on over 100 Servers and can't do this manually.
Lawrence Abrams - 8 years ago
Really sorry for not getting back to this sooner. I just did some tests and it appears that the WMIC command above will generate restore points for all protected drives and not just the C: drive. If you can confirm that would be great.
Best way to check is with shadow explorer, so you will need to rename vssadmin.exe back to its original name before that would work.
TechworksConsulting - 8 years ago
Hey Grinler - Doesn't look like this was updated yet to reflect what it breaks.
GuidoZ - 8 years ago
You shouldn't do this on servers, just workstations or home user systems. Servers use VSSadmin to perform several actions, including scheduled shadow copies as has been mentioned. Good advice for the average user, but messing with a server like this usually means "You're gonna have a bad time."
7of9 - 8 years ago
The SFC command is an IMPORTANT part of general maintenance for Vista and above. When executed (/scannow switch etc) it simply restores VSSAdmin.exe back to its original name/state - if you start deleting SFC sources for this file the sources could just be updated at some point or have other unforeseen negative effect on the OS performance.
As has been mentioned in ADDITION MUCH cheaper than the CryptoPrevent software is an LUA (ie NON-Admin account) with SRP(ie what c.prevent is based on). An LUA is vastly restricted in its ability to write to the file system (due to the OS's default inbuilt security cf Admin's are virtually unrestricted in this way) while SRP restricts file execution typically in areas were an LUA account still has writing permissions (eg account's user folder)
WindowsUser646 - 8 years ago
I am confused regarding the comment from maxamos and shadow copy creation "After running the batch file the scheduled shadow copies on my servers no longer run, I can create a shadow copy by selecting the create now button and if I rename the vssadmin back to its original state all schedules resume" AND the proposed use of WMIC as a workaround to create system restore points.
The Volume Shadow Copy Service (VSS) is the underlying Windows service providing the functionality of system restore points (the ability to restore Windows system files to an earlier point in time) as well as Previous Versions of one's documents (e.g. Excel files) if stored on a drive where shadow copies are being made.
Maxamos states that renaming vssadmin.exe prevented his computer from creating shadow copies. TechworksConsulting's follow-up comment confirmed that result. Since the WMIC work-around creates only restore points (backups of Windows system files that one can go back to), how does that help with the larger issue of shadow copy creation no longer being able to create "previous versions" of Excel and other data files? I do not understand.
Thank you.
Lawrence Abrams - 8 years ago
The WMIC command takes new snapshots. Test it out. Open Shadow Explorer and view your existing snapshots. Modify a file, use the WMIC command and you will see that shadow explorer sees a new snapshot.
StevenGDC - 8 years ago
So, after a quick search on C drive I found out that I have "vssadmin.exe" in the following locations, "C:\Windows\SysWOW64", and "C:\Windows\System32", do I have to rename both? They are different files the System32 one as 109Kb and the SysWOW64 one as 143Kb...
EltonAguiar - 7 years ago
I guess you can rename both vssadmin.exe files? Based on StevenGDC post? But what if the malware runs sfc.exe /scannow although if it's a rootkit probably wouldn't do that at least not last. Also, couldn't the malware just redownload a copy of vssadmin.exe and restore it to the windows directory or whatever directory? And aren't there other commands they can use to wipe the volume shadow copies?
foxman751 - 7 years ago
Should disable or should rename WMIC.exe for prevent ransom delete shadow copy
Serpent ransomware will also clear the Windows Volume Shadow Copies so that they cannot be used to recover files. The command executed to clear the shadow copies is:
WMIC.exe shadowcopy delete /nointeractive
dfxg^57vcbCVBFGHCGN - 7 years ago
Hi. This is a very interesting article and I thought I would implement on my PC. The problem is I've created the task and it does not seem to actually create any VSS snapshots. I manually create a VSS snapshot and confirmed it was available in previous versions when I look at my D drive. When I run the task and look at the same folder the only visible snapshot is the one that was manually created. I'm running Windows 10 home 64-bit.
If I run the command from an elevated command prompt I received the following output, this also does not create a snapshot. What have I done wrong?
C:\WINDOWS\system32>Wmic.exe /Namespace:\\root\default Path SystemRestore Call CreateRestorePoint "E%", 100, 7
Executing (SystemRestore)->CreateRestorePoint()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
p5ycho - 6 years ago
Hi,
This happened to me under Win 10 Pro x64, the command runs smoothly but no restore point at all, i've found there is a default setting that prevents new restore point on last 24 hours (from the last one).
If this is your problem, you can try create the restore point from powershell using "Checkpoint-Computer -Description "RestorePoint1" -RestorePointType "MODIFY_SETTINGS"" and you will see the following msg:
WARNING: A new system restore point cannot be created because one has already been created within the past 1440 minutes. The frequency of restore point creation can be changed by creating the DWORD value 'SystemRestorePointCreationFrequency' under the registry key 'HKLM\Software\Microsoft\WindowsNT\CurrentVersion\SystemRestore'. The value of this registry key indicates the necessary time interval (in minutes) between two restore point creation. The default value is 1440 minutes (24 hours).
In my case this was the problem, after the new Dword with custom value everything works great.
Hope it helps someone with same problem as me.
Quadrillion - 7 years ago
Thanks for this tip. I set up a scheduled task and renamed VSSAdmin as described above. Everyday, a window opens up and the exe runs. At the very end I get a quick screen that says exactly what is in the comment above beginning with "Executing":
Executing (SystemRestore)->CreateRestorePoint()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
If I go to System Restore through the Control Panel, I can see that there is indeed a restore point for that exe. Of course, I don't want to use it if there's a chance that something is wrong - which is where the "Out Parameters" comes in. Do these notations (__Parameters, Return Value, etc) mean anything that I need to be concerned with, or should I be comfortable that my system was successfully backed up? Thanks in advance.
JaqoBravo - 7 years ago
I got this error when i tried to make the task
http://vvcap.com/8BmeOQnuj3b
peterlonz - 7 years ago
Good info & thanks to those who helped with the procedure.
However this is all far too complicated for all but advanced users.
Most folk want to get work done quickly & securely, changing programs back & forthe is just not an option to be even considered.
Why in the name of God does MS not make this stuff easier, they have just launched a flagship OS which turns out to be full of security holes & it's now 2017.
It can't be that difficult to build a program incorporating all the above suggestions which then simply displays what's on & what's OFF making changes easy to experiment with.
Will this ne windows 12 maybe?
bruticus0 - 7 years ago
I did this and my system boinked. I renamed the vssadmin file back. Finally got system restored. Could have been the new Bitdefender trial, or adding another disk to be protected. Don't know. It worked fine on the Win8.1 machine though.
MultiverseIT - 7 years ago
Isn't this little more than an exercise in futility? Security by obscurity is not security. I spent 10 minutes thinking about this today, with the recent ransomeware incidents hitting the news, and thought of at least 3 different ways I could get around this if I were a bad guy. Most, if not all would require less than 20 lines of code. Better options would be to limit access rights to the file and / ensure you don't run as a user with administrative privileges. At least that way, the bad guys are forced to use more esoteric exploits - unpatched vulnerabilities and the like.
prasaddlv - 7 years ago
In Windows Server 2008 R2, I am logged in a administrator and when I right click on the batch file and run it, it shows the error "Please run the script again as an Administrator."
What could be the issue ?
p5ycho - 6 years ago
Hi,
Try to open command prompt as adminsitrator (right click -> run as administrator) first and then browse to the folder where is the batch file and run it.
Matt-CSUK - 6 years ago
If I try t run the command:
Wmic.exe /Namespace:\\root\default Path SystemRestore Call CreateRestorePoint "%DATE%", 100, 7
in C:\Windows\System32\wbem>
I get ERROR :
Description = Not found
Should I be replacing "namespace" with something else?
moyoman - 6 years ago
I have a question, in my case I host all files in a virtual win server 2012 r2 file server, I have 2 virtual HDD one for the shared and other for the shadow copies. y have the same config on the host of the 4 virtual servers, the host is not on the domain so it will ask for user/pass to access it I also have Symantec backup exec installed on the host and configured to do backups to a network HDD, backups of the virtual machines and of the files in the file server. The network HDD is in the domain and can only be access by the domain admin account user that I created for the backup exec.
Is it even possible that shadows on the virtual server and on the host could be erased with any of these commands in this particular configuration?
And again as many others thanks for your time and sorry if my English is not good.
geekomatic - 6 years ago
Is there any reason I can't just boot up a live Linux & rename vssadmin there?
Ryan87 - 5 years ago
Something I have realized and might be good to keep in mind with this is that if you ever run sfc /scannow it will see that vssadmin.exe either has been renamed or doesn't exist and it will replace the file with a known good copy.
MultiverseIT - 3 years ago
So, if I'm a malware author... what's stopping me from doing a simple check for the file... if not found, check the OS version, then go download from my own repository the exe necessary and appropriate for that version of windows and THEN execute the command.
Rather than injure your ability to manage windows, just have a good, offsite backup. Done.