Modern computers that come with a Thunderbolt interface and run Windows, macOS, Linux, or FreeBSD are vulnerable to a range of Direct Memory Access (DMA) attacks performed by potential attackers with physical access to the device using malicious peripherals.
The security flaws collectively dubbed "Thunderclap" can be exploited to run arbitrary code using highest possible privilege level on the system to potentially access or steal "passwords, banking logins, encryption keys, private files, browsing," and other sensitive data present on machine that come with ports for peripherals that use PCI Express (PCIe) and USB-C ports.
The Thunderclap vulnerabilities provide potential attackers with direct and unlimited access to a machine's memory because these ports come with low-level and very privileged direct memory access (DMA), which supplies any malicious peripherals with much more privileges than regular USB devices.
Computers impacted by Thunderclap
As explained by a team of researchers from the University of Cambridge, Department of Computer Science and Technology, Rice University, and SRI International, the attacks can compromise a vulnerable computer in just a few seconds.
The researchers say that most modern laptops, as well as a number of desktop computers, are susceptible to being vulnerable to Thunderclap-based attacks which can be carried out either with specially built malicious peripheral devices or common devices such as projectors or chargers that have been altered to automatically attack the host they are connected to.
Among the computers potentially affected by Thunderclap:
- Thunderbolt 3 is often supported via USB Type-C ports on modern laptops.
- Machines with older versions of Thunderbolt (carried over a Mini DisplayPort connector) are also affected.
- All Apple laptops and desktops produced since 2011 are vulnerable, with the exception of the 12-inch MacBook.
- Many laptops, and some desktops, designed to run Windows or Linux produced since 2016 are also affected - check whether your laptop supports Thunderbolt.
- Thunderclap vulnerabilities can also be exploited by compromised PCI Express peripherals, either plug-in cards or chips soldered to the motherboard.
Even though most vendors have implemented Input-Output Memory Management Units (IOMMUs) designed to provide memory protection for DMA and block all memory access from unrecognized devices altogether.
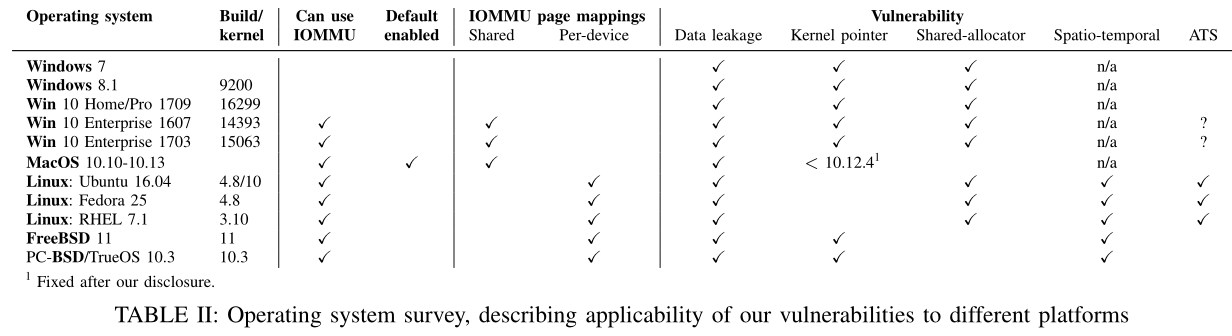
In collaboration with the research team, OS vendors have also added Thunderclap mitigation measures to their platforms starting with 2016 but the measures are not 100% effective and security flaws still impact systems protected using IOMMU.
While some platform such as Windows 7 to Windows 10 Home and Pro don't even come with IOMMU, on the OSs where it is present IOMMU is either limited (Windows 10 Enterprise), disabled out of the box (Linux and FreeBSD). The only platform where it is enabled is macOS, but even then the users aren't safe given that Thunderclap vulnerabilities can still circumvent it.
How to stay safe
As advised by the researchers behind Thunderclap, users need to completely disable the Thunderbolt interface on their computers if they want to be fully protected.
Those that still need to use the ports but don't need the vulnerable Thunderbolt features can disable them from their machine's firmware/UEFI/BIOS settings to still have access to the port's USB, power, and video capabilities.
Computer users can also make sure that they are not exposed to Thunderclap attacks by not borrowing chargers or using publicly available charging stations that may have been maliciously altered, and always keeping an eye out on their devices to make sure that attackers do not gain physical access without their knowledge.
As described by Theodore Markettos, one of the researchers behind the Thunderclap study, "Such attacks are very plausible in practice. The combination of power, video, and peripheral-device DMA over Thunderbolt 3 ports facilitates the creation of malicious charging stations or displays that function correctly but simultaneously take control of connected machines."
OS and hardware vendors adding IOMMU support
While most modern computers with a Thunderbolt interface are still vulnerable to Thunderclap attacks, most OS and hardware vendors have started enabling the IOMMU on their platforms and, in some cases, successfully mitigated the IOMMU bypass also states Markettos.
Intel for example "committed patches to Linux to enable the IOMMU for Thunderbolt devices, and to disable the ATS feature that allowed our IOMMU bypass," while "MacOS fixed the specific vulnerability we used to get administrator access in macOS 10.12.4 in 2016, although the more general scope of such attacks remain relevant."
The Thunderclap platform used to discover the vulnerabilities, as well as a number of proof-of-concept attacks, are described in the "Thunderclap: Exploring Vulnerabilities in Operating System IOMMU Protection via DMA from Untrustworthy Peripherals" paper available HERE in PDF format, and is authored by A. Theodore Markettos, Colin Rothwell, Brett F. Gutstein, Allison Pearce, Peter G. Neumann, Simon W. Moore, and Robert N. M. Watson.
More information on some of the experiments behind the vulnerabilities and the Thunderclap hardware platform is provided in Colin Rothwell's "Exploitation from malicious PCI Express peripherals" PhD thesis that can be found HERE.
The Thunderclap paper was presented at the NDSS 2019 conference that takes place in San Diego, USA, between 24-27 February 2019.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now