For the past two months, security researchers have been waging an online battle against a new 'BazarCall' malware that uses call centers to distribute some of the most damaging Windows malware.
The new malware was discovered being distributed by call centers in late January and is named BazarCall, or BazaCall, as the threat actors initially used it to install the BazarLoader malware.
While other malware is now being distributed, researchers continue to identify the distribution campaign as BazarCall.
Like many malware campaigns, BazarCall starts with a phishing email but from there deviates to a novel distribution method - using phone call centers to distribute malicious Excel documents that install malware.
Instead of bundling attachments with the email, BazarCall emails prompt users to call a phone number to cancel a subscription before they are automatically charged. These call centers would then direct users to a specially crafted website to download a "cancellation form" that installs the BazarCall malware.
From phishing emails to call centers
BazarCall attacks all start with a phishing email targeting corporate users that state the recipient's free trial is about to run out. However, these emails do not provide any details regarding the alleged subscription.
The emails then prompt the user to contact a listed phone number to cancel the subscription before they are charged $69.99 to $89.99 for a renewal, as shown in the example BazarCall phishing email below.
While the bulk of the emails seen by BleepingComputer have been from a fictitious company named "Medical reminder service, Inc.", the emails have also used other fake company names such as 'iMed Service, Inc.', 'Blue Cart Service, Inc.', and 'iMers, Inc.'
These emails all use similar subjects such as "Thank you for using your free trial" or "Your free trial period is almost over!" Security researcher ExecuteMalware has compiled a more extensive list of email subjects used by this attack.
When a recipient calls the listed phone number, they will be placed on a short hold and then be greeted by a live person. When asked for more information or how to cancel the subscription, the call center agent asks the victim for a unique customer ID enclosed in the email.
Randy Pargman, Vice President of Threat Hunting & Counterintelligence at Binary Defense, told BleepingComputer that this unique customer ID is a core component of the attack and is used by the call center to determine if the caller is a targeted victim.
"They will be able to identify the company that got that email when you give them a valid customer number on the phone. But if you give them a wrong number they will just tell you that they canceled your order and it’s all good without sending you to the website," Pargman told BleepingComputer in a conversation about BazarCall.
If a correct customer ID is given, the call center agent will direct the user to a fake website that pretends to be the associated medical services company. The phone agent will stay on the phone with the victim and guide them to a cancellation page where they are prompted to enter their customer ID, as shown below.
Source: Brad Duncan
When the user enters their customer ID number, the website will automatically prompt the browser to download an Excel document (xls or xlsb). The call center agent will then help the victim open the file and clicking on the 'Enable Content' button to enable malicious macros.
In some calls conducted by Pargman, the threat actors instructed him to disable antivirus to prevent the malicious documents from being detected.
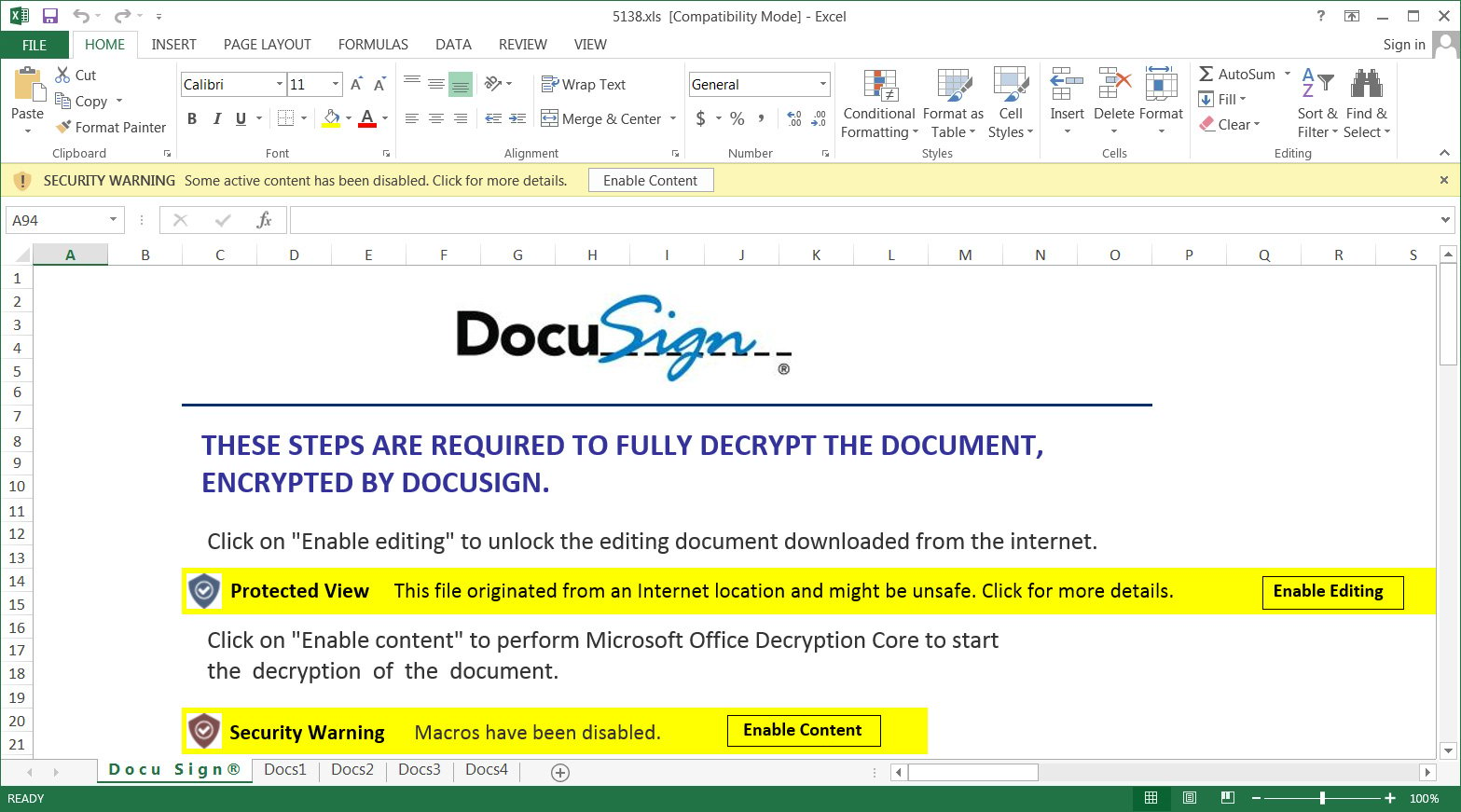
When the Excel macros are enabled, the BazarCall malware will be downloaded and executed on the victim's computer.
When the BazarCall campaign first started, it was used to distribute the BazarLoader malware but has also begun distributing TrickBot, IcedID, Gozi IFSB, and other malware.
These Windows infections are particularly dangerous as they provide remote access to compromised corporate networks where the threat actors spread laterally through the network to steal data or deploy ransomware.
Threat actors use BazarLoader and Trickbot to deploy the Ryuk or Conti ransomware, while IcedID has been used in the past to deploy the now-defunct Maze and Egregor ransomware infections.
Security researcher Brad Duncan has shared a video illustrating a call into the threat actor's call center and its distribution of malicious documents to unsuspecting victims.
Deployed via a Distribution-as-a-Service
While BazarLoader and the TrickBot infections are believed to be created by the same 'TrickBot' hacking group, the other distributed infections are not related to these threat actors.
Due to this, Pargman has told BleepingComputer that he believes that another threat actor group is running the call centers and renting out distribution as a Distribution-as-a-Service.
"My belief is that this is a distro as a service and that UNC1878 is probably a customer of theirs," Pargman explained.
This belief is echoed by Cryptolaemus security researcher Joseph Roosen who told BleepingComputer that the distribution service is run like a regular company, keeping strict Monday through Friday business hours.
BleepingComputer's efforts to contact the call center over the past four days have been unsuccessful due to the constantly changing infrastructure used by the threat actors.
Due to the efforts of researchers such as Pargman, Roosen, Duncan, William Thomas of Cyjax, TheAnalyst, and ExecuteMalware, and many others, the distribution service has been forced to constantly change their phone numbers and hosting sites as the researchers take them down.
Unfortunately, even with the cybersecurity community's combined efforts, this distribution method has been very successful.
Due to their distribution method, malware samples commonly have very low detection rates on VirusTotal as they are not publicly distributed and detected by antivirus vendors.
Furthermore, from emails seen by BleepingComputer, people are falling for this scam as they believe they are legitimate subscriptions that need to be canceled.



Comments
Wolverine 7 - 3 years ago
That dog looks deeply troubled,..
E mails,..dont click on anything you dont recognise,..even then,take a good second look..think..dont unsubscribe from anything you dont fully remember subscibing too..,..just delete it,..
mynameisgod - 3 years ago
One point you should have mentioned is the domain in your screenshot: gtmers.xyz is Namecheap.com. It's ALWAYS a Namecheap domain behind this shit. ALWAYS. I didn't even need to look it up because this scam just stinks of Namecheap.com. Also, you type in a website address in your video, it goes to "getmers.us". You will see that is also Namecheap.com, of course.