
Have you ever heard of the STOP Ransomware? Probably not, as few write about it, most researchers don't cover it, and for the most part it targets consumers through cracked software, adware bundles, and shady sites.
Ryuk, GandCrab, and Sodinkibi get huge and deserved media attention because they generate giant ransom payments, can halt business and local governments, and affect enterprise customers, which are the bread and butter for AV companies.
Yet, based on Michael Gillespie's ID Ransomware submissions and support requests at BleepingComputer, for the past year it has been the most actively distributed ransomware in the wild.
To give you some perspective, the ransomware identification service ID Ransomware gets approximately 2,500 ransomware submissions a day. Of those, between 60-70 % are STOP ransomware submissions.
This amount of submissions beats out any other ransomware that users are submitting to the service when trying to get help.
STOP is getting so big that the image above looks like Pacman eating all of the other ransomware!
Cracks, Adware bundles, and shady sites
In order to distribute STOP, the ransomware developers have teamed up with shady sites and adware bundles.
These sites promote fake software cracks or free programs, which are really adware bundles that install a variety of unwanted software and malware onto a user's computer. One of the programs installed via these bundles is the STOP Ransomware.
Some of the reported cracks that are have been seen installing STOP include KMSPico, Cubase, Photoshop, and antivirus software.
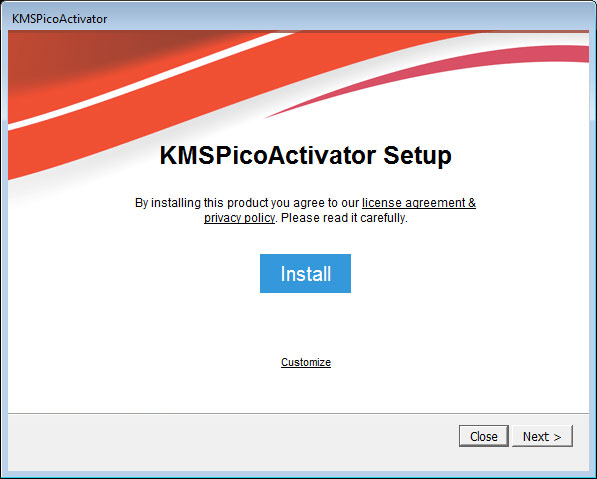
It is not only cracks, though, as many of these shady sites offer downloads of free software, but are simply just adware bundles that install the ransomware.
Even worse, some of these variants also bundle the Azorult password stealing Trojan with the ransomware for a double-attack on the victim.
Otherwise, there is nothing particularly special about the STOP Ransomware. It encrypts just like any other ransomware, appends an extension, and drops a ransom note.
What makes it so much of a pain is the sheer amount of variants that keep being released. In fact right now, there are more than 159 variants that we know about.
Users are desperate
Gillespie has had some success helping victims recover their files through his decryption tool STOPDecryptor that includes offline decryption keys that the ransomware uses when it couldn't communicate with the C2. The ransomware researcher has also had limited success in helping those who were infected with unique keys.
This has been an arduous task, though, with the ransomware pumping out sometimes 3-4 variants a day and thousands of victims needing help at one time.
Unfortunately, the encryption has changed and Gillespie will no longer be able to offer as much support as he was previously able to.
For already desperate users, this news makes it even worse as many are unable to afford the $490 ransom, which doubles after 72 hours to $980.
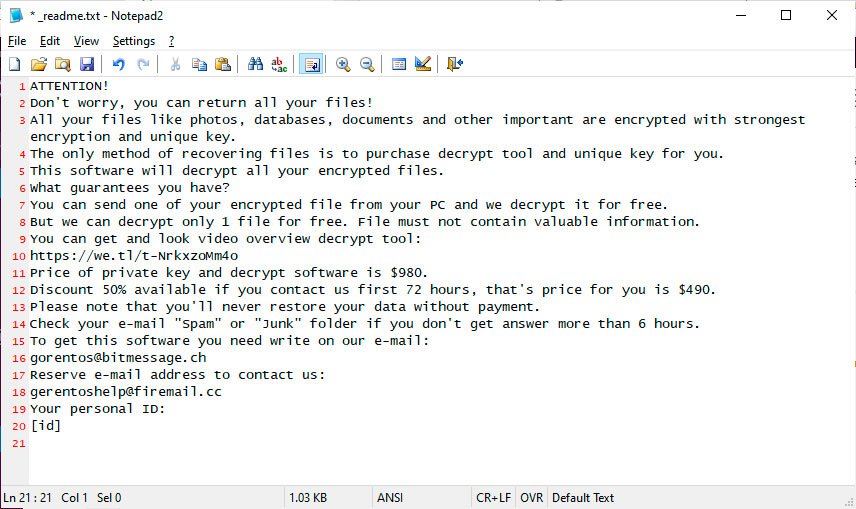
This leads users to leave constant support requests at BleepingComputer and in unrelated tweets by Gillespie.
Please help me Broo
— Karanganyar (@afwin_channel) September 20, 2019
My Komputer Infected Virus .KVAG
Id : 0163Asd483yiqgkhjdg6T5mXmvIFUoo8mghI7ZipcBHp6KgFFRodOvN2jaJ
Please Help Me
I need Help Youplease
While some may say that these victim had it coming because they downloaded cracks, it is important to remember that we never want to let the ransomware developers generate ransom payments as it only leads to more ransomware being created.



Comments
GT500 - 4 years ago
I've had to answer so many STOP/Djvu ransomware help requests that sometimes I wonder if I can even remember anything else anymore. Every now and then a GlobeImposter 2.0 or Dharma/Crysis help request shows up, but these days when I see a ransomware extension I don't recognize I just expect it to be a new STOP/Djvu while I'm looking it up...
nileshbhakre - 4 years ago
stop ransomware can not be stop.
Peter_M - 4 years ago
I almost exclusively deal with the corporate environment and have to investigate a LOT of attacks, Ryuk being pretty much constant at the moment. However I have never had to investigate STOP and i have always wondered why, this article has helped explain that. thanks.
rapidbeepingnoises - 1 year ago
the stop ransomware needs to STOP
Wasif001 - 4 years ago
LETO please help me
mikano001 - 4 years ago
help!! , i am infected with .derp ransomware ,
ID: PGbVyl8UYuRyjspU691qsYjNteXmltJ5VTeygepj
MaryhanaRosza - 4 years ago
help!! , I'm infected with .mado ransomware ,
ID: 0217OIWojlj48kaYPxfA1ZjGtZJwTSpaMa41g1uIMvjA5mF0g1rq2
JLRoco30 - 4 years ago
Hi, i dont know what Ransomware is: id:
n23TvdGpY9jOVIBWcMat4aAhZZgz3LurNykjL1IJ{36A698B9-D67C-4E07-BE82-0EC5B14B4DF5}
the file is a txt
ORIGINAL FILE ----
Torrent Downloaded From ExtraTorrent.com
- The biggest torrent community
- No fake torrents, All torrents checked by our Moderators
- The latest torrent releases
- The most helpful members and site admins
- Be updated with the latest news in the p2p world with ExtraTorrent
- The best forum community in the p2p world
WITH RANSOMWARE----
TorreRKÑ`Ùkö¦S|ÔPH›ÊÜÖÅ
Ö¿ aÛ´É•-O\²´…ŸcîÿjÔˆ'Ì=#ù:‡6P²õÔ¼ž–û³^7w,q aÅŽ3ªnK
÷Iaìá›^”ã…ÈK™š×1g²Ö©¤×ÏZpÏXlB8NMµ€M1Ó¹TõvòÉ_¤{ÜiZOãû†A¤³'VLqWô{~öƒ©A ÒCj’ó¯M¨VæfVhkô+ýYâGUª~©jL¸·‹›{Ø&AeøTÞ=?ÿVv¼÷Vkõ,ÕâZ^NÄ—ýñn?4–R¤º{†Õvѵï×$Þ`¾ìêZ¡Æe;Çj7Ï·ïÜJí:ÞgÆ.´»4ÌÃQ”“Š›=%㉈ÄNa÷w±ÒiSÝŒ´Õ/Èu”¬€Á]ƒ£(æ¶,í‰W¹|÷e¾g1lI•Š/C’hn23TvdGpY9jOVIBWcMat4aAhZZgz3LurNykjL1IJ{36A698B9-D67C-4E07-BE82-0EC5B14B4DF5}
kakero - 3 years ago
no onluck id
Your personal ID:
0161psdfjH7gdfgUKH2nNREsFSdasQ5wfkryB1hvzj5KUC6hq1kzu3C
Acel74 - 2 years ago
<p>I get infested, all my personal data "realy personal" is encrypted now, I have an older file and the same in encrypted version. Anyone please help. Is seams to bo a newer version.</p>
kuuhuu - 1 year ago
Error: No key for New Variant online ID: DsNMLxvTJCA8kPumRFAipNBL9MBstlhEyPY59pB1
Notice: this ID appears to be an online ID, decryption is impossible
please help