
Academic researchers developed ZenHammer, the first variant of the Rowhammer DRAM attack that works on CPUs based on recent AMD Zen microarchitecture that map physical addresses on DDR4 and DDR5 memory chips.
AMD Zen chips and DDR5 RAM modules were previously considered less vulnerable to Rowhammer, so the latest findings challenge this notion.
The ZenHammer attack was developed by researchers at public research university ETH Zurich, who shared their technical paper with BleepingComputer.
Attack background
Rowhammer is a well-documented attack method that exploits a physical characteristic of modern Dynamic Random-Access Memory (DRAM) to alter data by repeatedly accessing ("hammering") specific rows of memory cells through read/write operations to change bit values inside.
Memory cells store information as electric charges that determine the value of the bits inside as a 1 or a 0. Because of the increased density of the memory cells in modern chipscells, repeated "hammering" can change the charge state in adjiacent rows, a process known as "bit flipping."
By strategically inducing these bit flips in specific locations, an attacker could gain access to sensitive data (e.g. cryptographic keys) or escalate privileges.
The technique has been demonstrated on Intel and ARM CPUs, leaving AMD's Zen architecture CPUs largely unexplored due to inherent challenges such as unknown DRAM addressing schemes, synchronization with refresh commands, and difficulty to achieve a high enough row activation throughput.
With ZenHammer, the researchers at ETH Zurich managed to address these challenges by reverse-engineering the complex and non-linear DRAM addressing functions in AMD platforms.
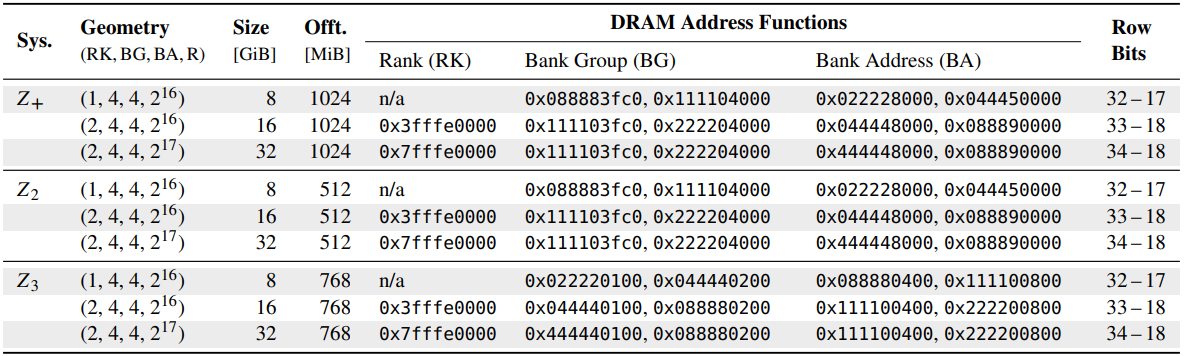
They also developed novel synchronization techniques to time their attacks with DRAM's refresh commands, which was crucial for bypassing mitigations like Target Row Refresh (TRR).
Additionally, the researchers optimized memory access patters to increase row activation rates, which is a critical factor in the success of Rowhammer attacks.
Test results
The researchers demonstrated that the ZenHammer attack could induce bit flips with DDR4 devices on AMD Zen 2 (Ryzen 5 3600X) and Zen 3 platforms (Ryzen 5 5600G). They were successful in 7 out of 10 tests on DDR4/AMD Zen 2 platforms and 6 out of 10 DDR4/AMD Zen 3 platforms.
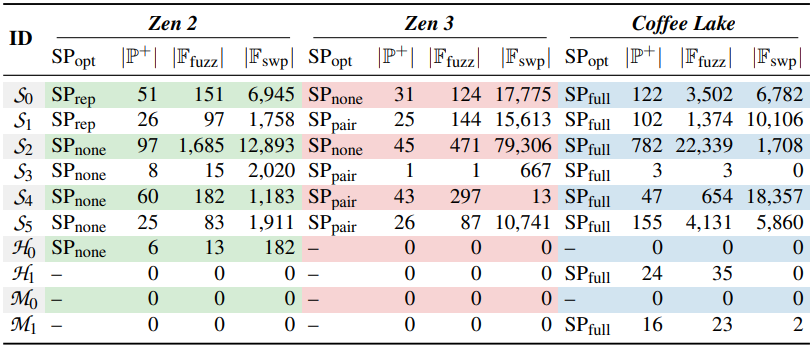
The researchers were also successful with DDR5 chips on AMD's Zen 4 microarchitectural platform, previously considered better shielded against Rowhammer attacks.
However, the test was successful on only one of the 10 systems, a Ryzen 7 7700X, indicating "that the changes in DDR5 such as improved Rowhammer mitigations, on-die error correction code (ECC), and a higher refresh rate (32 ms) make it harder to trigger bit flips."
These bit flips were not just theoretical, as the analysts were able to simulate successful attacks that targeted the system's security, including manipulating page table entries for unauthorized memory access.
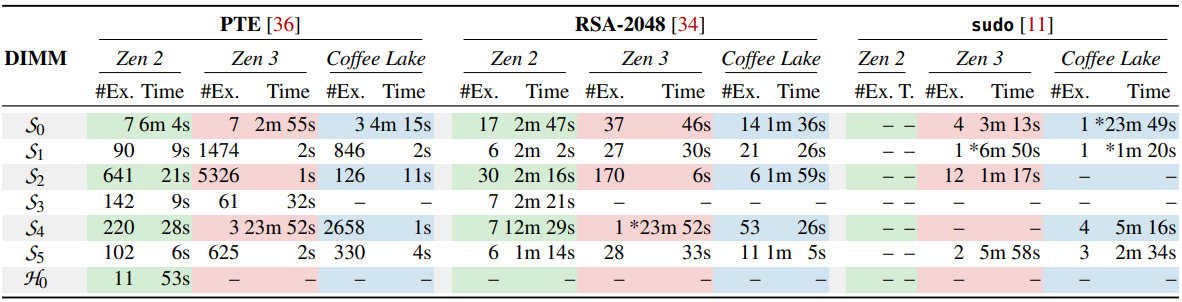
On one of the Zen 3 test systems produced in Q4 2021, the researchers were able to obtain root privileges in 10 successful attacks with an average time of 93 seconds, starting the moment an exploitable bit flip was discovered.
The options AMD CPU users have to defend against this threat resume to applying software patches and firmware updates. They may also want to consider using hardware that has implemented specific mitigations against Rowhammer, which typically integrates newer technology.
It is worth highlighting that these attacks are complex and successful execution requires an attacker with a deep understanding of both software and hardware components.
Update 3/25 - AMD has published a security bulletin in response to ZenHammer, offering mitigation advice and assuring that it is assessing the issues thoroughly and will provide updates.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now