
The notorious Conti ransomware gang has officially shut down their operation, with infrastructure taken offline and team leaders told that the brand is no more.
This news comes from Advanced Intel's Yelisey Boguslavskiy, who tweeted this afternoon that the gang's internal infrastructure was turned off.
While public-facing 'Conti News' data leak and the ransom negotiation sites are still online, Boguslavskiy told BleepingComputer that the Tor admin panels used by members to perform negotiations and publish "news" on their data leak site are now offline.
In addition, BleepingComputer was told that other internal services, such as their rocket chat servers, are being decommissioned.
While it may seem strange for Conti to shut down in the middle of their information war with Costa Rica, Boguslavskiy tells us that Conti conducted this very public attack to create a facade of a live operation while the Conti members slowly migrated to other, smaller ransomware operations.
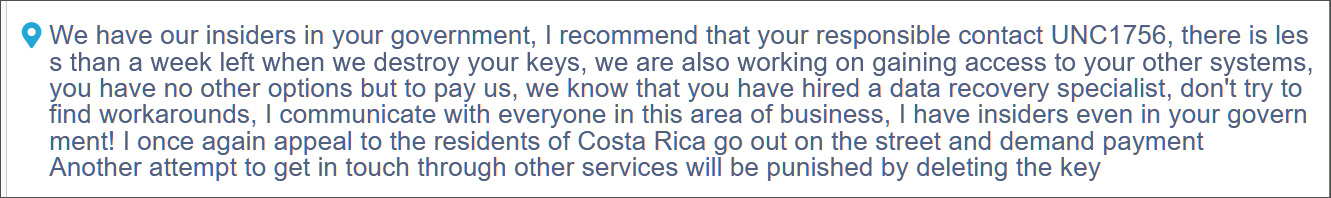
Source: BleepingComputer
"However, AdvIntel’s unique adversarial visibility and intelligence findings led to, what was in fact, the opposite conclusion: The only goal Conti had wanted to meet with this final attack was to use the platform as a tool of publicity, performing their own death and subsequent rebirth in the most plausible way it could have been conceived," explains a report being released tomorrow by Advanced Intel.
"The agenda to conduct the attack on Costa Rica for the purpose of publicity instead of ransom was declared internally by the Conti leadership. Internal communications between group members suggested that the requested ransom payment was far below $1 million USD (despite unverified claims of the ransom being $10 million USD, followed by Conti’s own claims that the sum was $20 million USD)."
Conti's gone, but the operation lives on
While the Conti ransomware brand is no more, the cybercrime syndicate will continue to play a significant role in the ransomware industry for a long time to come.
Boguslavskiy told BleepingComputer that instead of rebranding as another large ransomware operation, the Conti leadership has instead partnered with other smaller ransomware gangs to conduct attacks.
Under this partnership, the smaller ransomware gangs gain an influx of experienced Conti pentesters, negotiators, and operators. The Conti cybercrime syndicate gains mobility and greater evasion of law enforcement by splitting into smaller "cells," all managed by central leadership.
The Advanced Intel report explains that Conti has partnered with numerous well-known ransomware operations, including HelloKitty, AvosLocker, Hive, BlackCat, BlackByte, and more.
The existing Conti members, including negotiators, intel analysts, pentesters, and developers, are spread throughout other ransomware operations. While these members will now use these other ransomware operation's encryptors and negotiation sites, they are still part of the larger Conti cybercrime syndicate.
This splintering into smaller semi-autonomous and autonomous groups is illustrated in the image below shared by Advanced Intel.
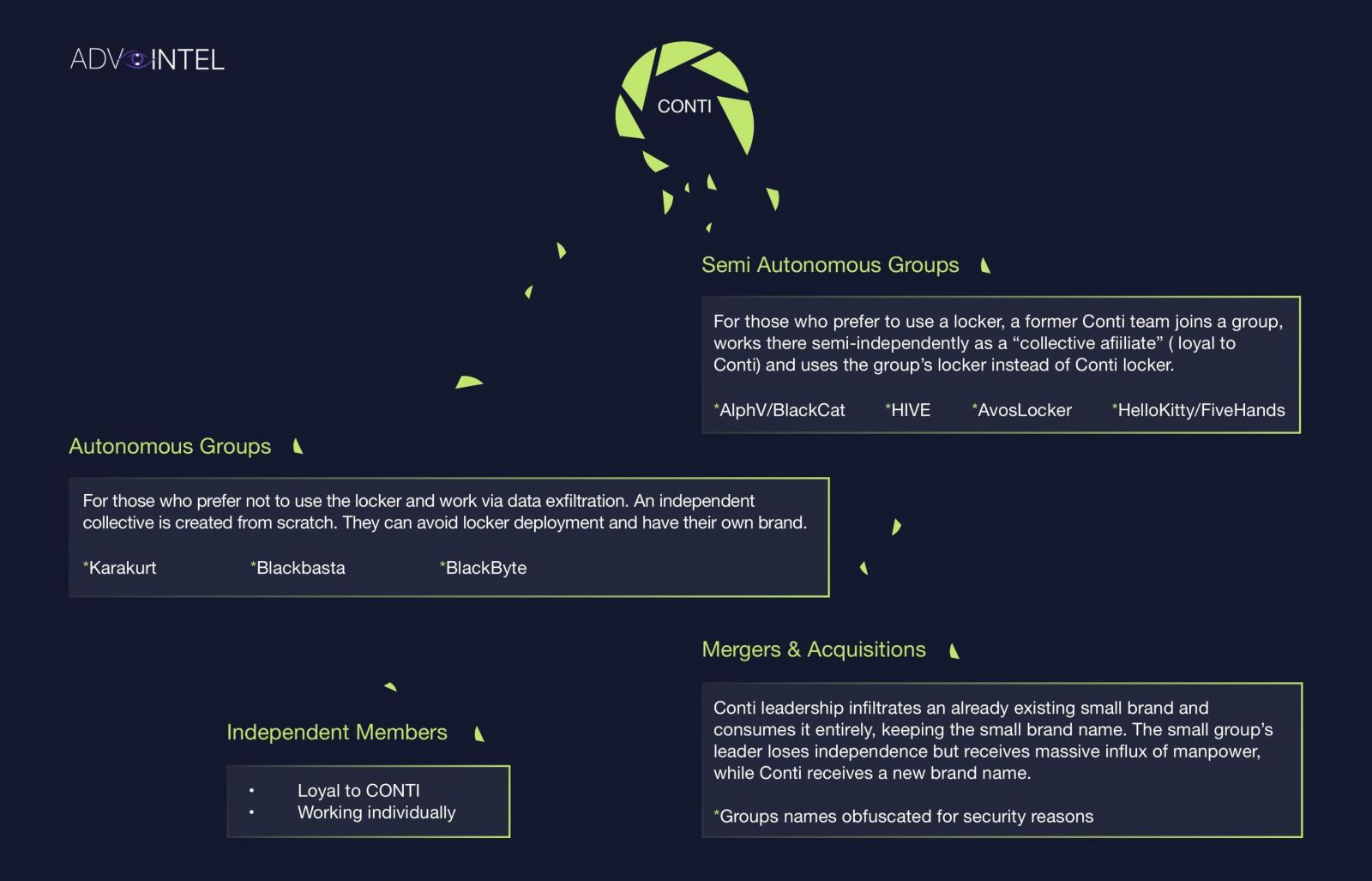
Source: Advanced Intel
Advanced Intel also states that new autonomous groups of Conti members have been created that focus entirely on data exfiltration and not data encryption. Some of these groups include Karakurt, BlackByte, and the Bazarcall collective.
These initiatives allow the existing cybercrime syndicate to continue operating but no longer under the Conti name.
A toxic brand
The rebranding of Conti comes as no surprise to researchers and journalists who have been following them over the past months, if not the past years.
The Conti ransomware operation launched in the summer of 2020, after taking the place of the Ryuk ransomware.
Like Ryuk, Conti was distributed through partnerships with other malware infections, such as TrickBot and BazarLoader, who provided initial access to the ransomware gang.
Over time, Conti grew into the largest ransomware operation, slowly turning into a cybercrime syndicate as they took over the operation of TrickBot, BazarLoader, and Emotet.
Conti was responsible for numerous attacks during their time, including those against the City of Tulsa, Broward County Public Schools, and Advantech.
They gained widespread media attention after they attacked the Ireland's Health Service Executive (HSE) and Department of Health (DoH), shutting down the IT systems of the country for weeks.
Ultimately, the ransomware gang provided a free decryptor to Ireland's HSE, but at that point, they were firmly in the crosshairs of law enforcement around the world.
However, it wasn't until Conti sided with Russia's invasion of Ukraine that the Conti brand became incredibly toxic and their fate was sealed.
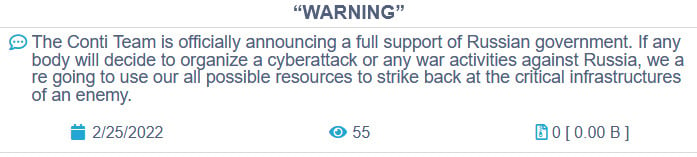
Source: BleepingComputer
After siding with Russia, a Ukrainian security researcher began leaking over 170,000 internal chat conversations between the Conti ransomware gang members and the source code for the Conti ransomware encryptor.
Once this source code became public, other threat actors began using it in their own attacks, with one hacking group using the Conti encryptor in attacks against Russian entities.
The US government considers Conti one of the costliest strains of ransomware ever created, with thousands of victims and over $150 million in ransom payments.
The Conti ransomware gang's exploits have led the US government to offer up to a $15,000,000 reward for the identification and location of Conti members in leadership roles.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now