Ransomware actors are again using TeamViewer to gain initial access to organization endpoints and attempt to deploy encryptors based on the leaked LockBit ransomware builder.
TeamViewer is a legitimate remote access tool used extensively in the enterprise world, valued for its simplicity and capabilities.
Unfortunately, the tool is also cherished by scammers and even ransomware actors, who use it to gain access to remote desktops, dropping and executing malicious files unhindered.
A similar case was first reported in March 2016, when numerous victims confirmed in the BleepingComputer forums that their devices were breached using TeamViewer to encrypt files with the Surprise ransomware.
At the time, TeamViewer's explanation for the unauthorized access was credential stuffing, meaning the attackers did not exploit a zero-day vulnerability in the software but instead used users' leaked credentials.
"As TeamViewer is a widely spread software, many online criminals attempt to log on with the data of compromised accounts, in order to find out whether there is a corresponding TeamViewer account with the same credentials," explained the software vendor at the time.
"If this is the case, chances are they can access all assigned devices, in order to install malware or ransomware."
TeamViewer targeted again
A new report from Huntress shows that cybercriminals haven't abandoned these old techniques, still taking over devices via TeamViewer to try and deploy ransomware.
The analyzed log files (connections_incoming.txt) showed connections from the same source in both cases, indicating a common attacker.
In the first compromised endpoint, Huntress saw in the logs multiple accesses by employees, indicating the software was actively used by the staff for legitimate administrative tasks.
In the second endpoint seen by Huntress, which has been running since 2018, there had been no activity in the logs for the past three months, indicating that it was less frequently monitored, possibly making it more attractive for the attackers.
In both cases, the attackers attempted to deploy the ransomware payload using a DOS batch file (PP.bat) placed on the desktop, which executed a DLL file (payload) via a rundll32.exe command.
Source: BleepingComputer
The attack on the first endpoint succeeded but was contained. On the second, the antivirus product stopped the effort, forcing repeated payload execution attempts with no success.
While Huntress hasn't been able to attribute the attacks with certainty to any known ransomware gangs, they note that it is similar to LockBit encryptors created using a leaked LockBit Black builder.
In 2022, the ransomware builder for LockBit 3.0 was leaked, with the Bl00dy and Buhti gangs quickly launching their own campaigns using the builder.
The leaked builder allows you to create different versions of the encryptor, including an executable, a DLL, and an encrypted DLL that requires a password to launch properly.
Source: BleepingComputer
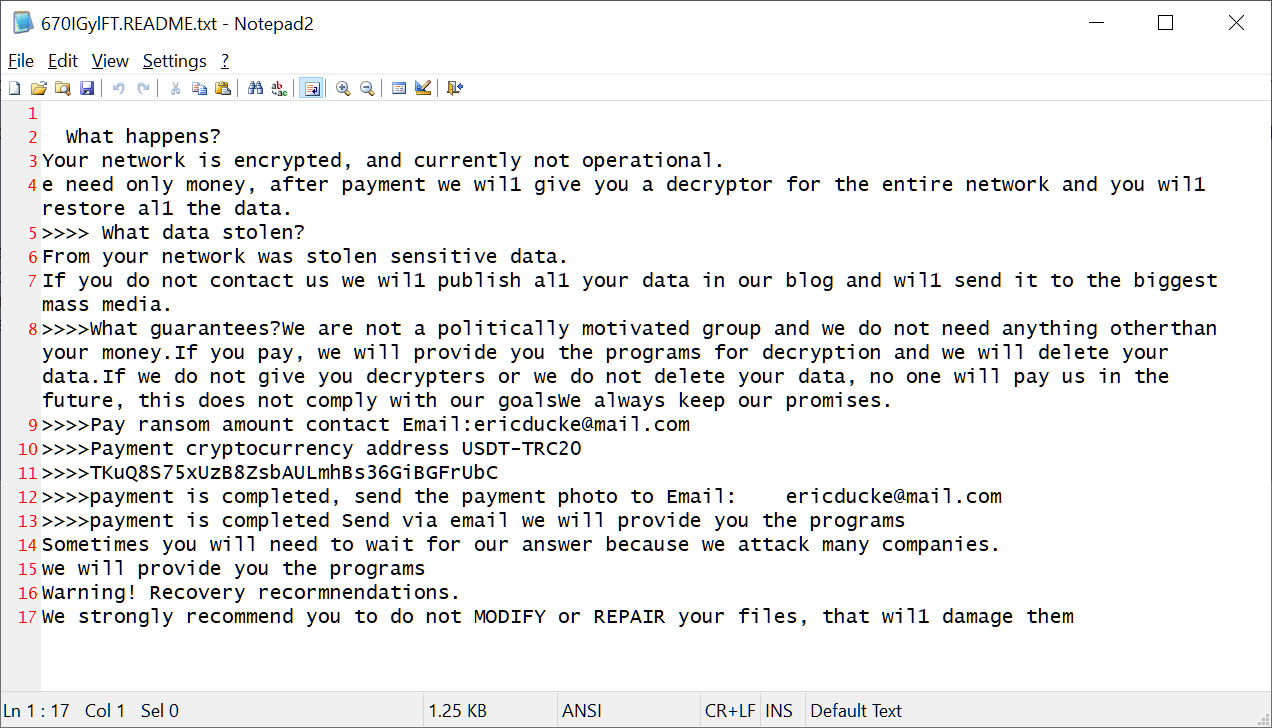
Based on the IOCs provided by Huntress, the attacks through TeamViewer appear to be using the password-protected LockBit 3 DLL.
While BleepingComputer could not find the specific sample seen by Huntress, we found a different sample uploaded to VirusTotal last week.
This sample is detected as LockBit Black but does not use the standard LockBit 3.0 ransomware note, indicating it was created by another ransomware gang using the leaked builder.
Source: BleepingComputer
While it is unclear how the threat actors are now taking control of TeamViewer instances, the company shared the following statement with BleepingComputer about the attacks and on securing installations.
"At TeamViewer, we take the security and integrity of our platform extremely seriously and unequivocally condemn any form of malicious use of our software.
Our analysis shows that most instances of unauthorized access involve a weakening of TeamViewer's default security settings. This often includes the use of easily guessable passwords which is only possible by using an outdated version of our product. We constantly emphasize the importance of maintaining strong security practices, such as using complex passwords, two-factor-authentication, allow-lists, and regular updates to the latest software versions. These steps are critical in safeguarding against unauthorized access.
To further support our users in maintaining secure operations, we have published a set of best practices for secure unattended access, which can be found at [Best practices for secure unattended access - TeamViewer Support]. We strongly encourage all our users to follow these guidelines to enhance their security posture."



Comments
GT500 - 5 months ago
I only skimmed the article, however from what I saw I'm guessing that this is only happening on devices where TeamViewer has been configured for unattended remote access?
Regardless, my advise is always to keep a backup on some sort of external media (USB hard drive or flash drive, DVD/Blu-ray, tapes, etc) and then disconnect them from the computer when not in use. Ransomware will often encrypt files on any drive connected to the PC (including anything accessible over the network), and if the threat actor gains access via compromised remote access software they may even delete cloud backups.
NoneRain - 5 months ago
Unattended access should not be an issue IF you have strong passwords and MFA enforced, which they didn't.
Bauhaus68 - 5 months ago
this is NEWS?
John_Doe_Toor - 5 months ago
We are in 2024 and people still do not use strong passwords and Multi/Two Factor Authentication (MFA/TFA) for their accounts?
This is clearly not a TeamViewer issue, it is a user's lack of minimal security mindset!