In this article, we review Perimeter 81, a Secure Access Service Edge service, as we discuss how secure it is, whether it's good value, what features it has to offer, and so much more.
Perimeter 81 is a veteran Secure Access Service Edge (SASE) provider catering to small-to-medium-sized organizations with remote staff and geographically dispersed offices. With it, organizations can allow remote workers to securely access company resources hosted locally or on the cloud, connect two offices with a site-to-site VPN, and improve endpoint security, especially for organizations with bring-your-own-device (BYOD) policies.
In this review, I'll answer the following questions:
- Is Perimeter 81 secure?
- Is Perimeter 81 fast?
- Is Perimeter 81 good value?
- Is Perimeter 81 easy to set up and use for both admins and clients?
- Can Perimeter 81 scale to grow with my organization?
- What apps, ID providers, and cloud services is Perimeter 81 compatible with?
Perimeter 81 is a SASE service, which you might compare to a Virtual Private Network (VPN). While SASE and a VPN offer many of the same benefits, SASE provides more control and granularity. More on that later.
If you don't have time to read the full article, here's a summary of my review.
Perimeter 81 review summary
Perimeter 81 is a robust but easy-to-use networking tool that will best serve organizations employing between a few dozen and a few hundred people. If you need to secure remote workers' access to resources stored on-premises or on the cloud, or set up a secure site-to-site connection between two or more office locations, then Perimeter 81 can help you.
Although it's not a replacement for skilled IT staff, it will certainly make their jobs easier. On the downside, Perimeter 81 is more expensive than the competition.
Pros:
- Easy to set up and use
- Strong encryption and leak-proof
- Simple to scale up as your organization grows
- Fast servers in 20+ countries
- Works in China
- Compatible with a wide range of apps, cloud services, ID providers, and VPN protocols
Cons:
- Pricier than rivals
- Useful features like FWaaS limited to more expensive plans
- No deep packet inspection (DPI)
- No kill switch
Perimeter 81 admin setup
Administrators manage Perimeter 81 from a web-based dashboard that can be accessed from any standard web browser. From here, you can set up servers and gateways, keep track of clients, segment the network, and assign privileges to team members.
It takes about 20 minutes from logging in to spinning up your first network, which consists of at least one gateway and one server.
From there, you can send invites to team members, assign them to groups, and configure the firewall. The next step is segmenting your network and narrowing access rules to individual users and groups. You can control clients' interactions with resources based on application access, user and group identity, and the sensitivity of the data being accessed. Authentication is enforced using identity providers like Okta, Google, and Azure.
Perimeter 81 supports multiple protocols and encryption solutions at once, depending on the relevant environment and connection. This lets you adapt Perimeter 81 to different environments.
We'll go into more detail on the firewall and other security features later.
The monitoring Dashboard displays active sessions, utilized member licenses, gateway licenses, applications, and active users.
Perimeter 81 can securely connect your staff to all major cloud providers including Google, Azure, AWS, Salesforce, Heroku, Splunk, as well as to on-premises resources on a local network. Site-to-site tunnels can be set up with IPSec and OpenVPN, or the Perimeter 81 Connector (WireGuard) for AWS, Azure, Google Cloud, and other cloud providers. Connector requires Ubuntu 20, 16.04 LTS, 18.04 LTS, or CentOS.
Private gateways can be deployed in multiple locations. Creating a network with distributed access points helps serve international branches, remote employees, and region-based cloud resources with low latency and high availability. The number of regions and gateways is limited to the number of gateway licenses you've purchased.
You can deploy a gateway in about 20 countries. Here is a full list of locations:
North America:
- Denver
- Dallas
- New York
- Chicago 1
- Silicon Valley
- Miami
- Seattle
- New Jersey
- Los Angeles
- Atlanta
- Honolulu
- Toronto
- Fremont
- New Jersey
- San Francisco
EMEA:
APAC:
- Singapore 1
- Bangalore
- Mumbai
- Sydney 1
- Tokyo 1
- Seoul
- Melbourne
- Manilla
LATAM:
- Mexico City
- São Paulo
If you opt for one of the higher-tier plans, you'll also get access to shared public gateways. These are more or less like consumer VPN servers that secure your connection to the public internet. Users connected to one of these servers will share an IP address.
Next, I'll discuss the client apps.
Client apps: What devices work with Perimeter 81?
Perimeter 81 makes client apps available for the following operating systems:
- Windows 8.1 or later
- MacOS 10.15 or later
- iOS 9.0 or later
- Android 8.1 or later
- Ubuntu 18.04 or later
The mobile apps are available from their respective app stores, and the desktop apps can be downloaded directly from Perimeter 81.
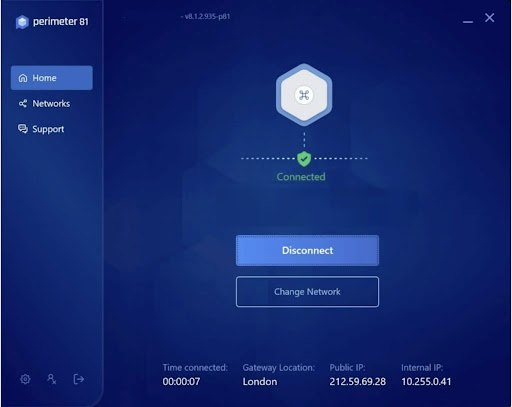
There are no Perimeter 81 browser extensions or plugins at this time. You must install the native apps on the operating system.
The desktop app runs from the system tray and couldn't be much simpler. After logging in, users are given a list of gateways to which they've been granted access. By default, the apps connect to Perimeter 81 as soon as they are opened, and admins can enforce this behavior.
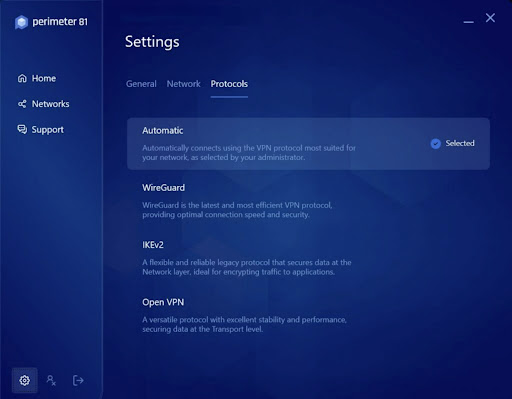
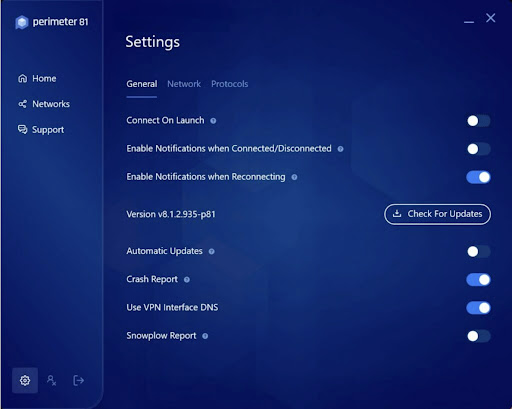
In the settings menu, clients can change their VPN protocol to WireGuard, IKEv2, or OpenVPN. They can adjust when Perimeter 81 automatically connects, manage notifications, toggle automatic updates, and choose whether to use the VPN's DNS settings.
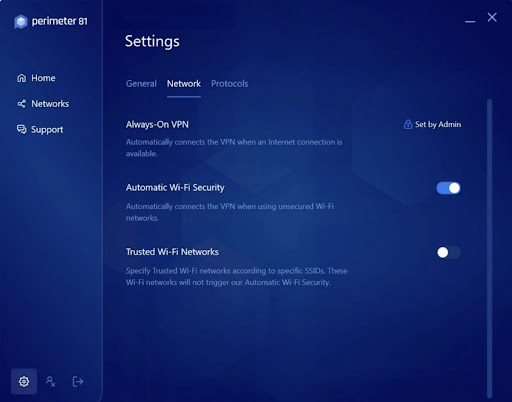
The apps can be set to auto-connect when using untrusted WiFi or when the app launches. As an endpoint user, you can add trusted WiFi networks to a list. You won't be automatically connected to the VPN when using these.
The mobile interface is a mirror image of the desktop version, albeit with fewer options in the settings menu.
Noticeably missing from the client apps is a kill switch. Kill switches halt all internet traffic if the VPN connection is disrupted, preventing unencrypted traffic from leaking outside the VPN tunnel.
Perimeter 81 security
Perimeter 81 combines a software-defined perimeter (SDP) to enable zero-trust network access (ZTNA). Under this model, users and their devices must be authenticated before connecting. That authentication includes identity verification and device posture checks. Admins can use these to restrict third-party access to specific applications without exposing their network. You can limit application access by user, time, location, and browser. Perimeter 81 supports HTTPS, RDP, VNC, SSH, and VoIP protocols.
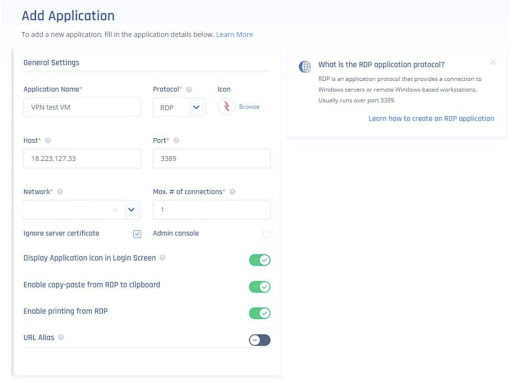
An SDP network has three important components: client, controller, and the gateway PoP. The client verifies who they are using an identity provider such as Okta, Google, or Azure. It routes whitelisted applications to authorized remote connections, ensuring that the VPN only connects to authorized services.
Network traffic is tunneled between the user’s device and the corresponding gateway. The controller establishes trust between the SDP Client and backend security controls by authenticating users and devices. The gateway grants access to previously private resources, giving remote employees a private and uncongested connection.
Unlike a traditional VPN, Perimeter 81 uses software-defined wide area networking (SD-WAN) infrastructure. It’s a cloud-based approach to connecting offices in multiple locations. It allows administrators to separate traffic based on security level, authorization, and quality of service (QoS) settings. Compared to a VPN, SD-WAN benefits from lower latency and has some security failovers that VPNs do not.
SDP, ZTNA, and SD-WAN are the key elements of Perimeter 81's SASE infrastructure. To summarize, SASE enforces least-privilege access to network segments based on identity, role, and device.
One of the first tasks for administrators is to configure your firewall policies. Perimeter 81 boasts a robust firewall-as-a-service (FWaaS) to control internal network access to apps, resources, regions, and data centers. Note, however, FWaaS isn't available on the cheapest plan.
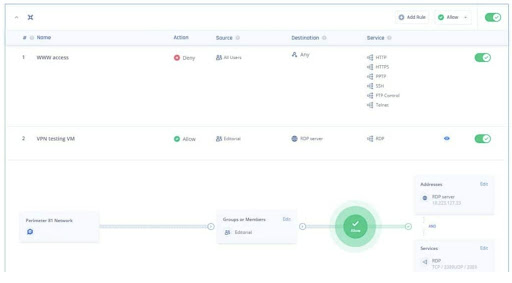
The firewall secures and controls all traffic on one unified SDP. You can assign a group of users their own policies and rules to access specific parts of a certain network. For example, I can ensure a group of team members only uses a specific protocol and only when coming from an internal subnet IP range.
Here are some of Perimeter 81's other major security features:
- DNS filtering: Block access to malicious or infected websites. Prevent employees from accessing material that could hinder productivity.
- Device posture check: Establish trust only in devices that comply with security policies. Automatically deny access to insecure or compromised devices. Devices can be checked for antivirus, certificates, Windows registry keys, disk encryption, and more.
- Cloud access service broker (CASB): Extend your security policy to your cloud service provider’s architecture to protect it from uninvited users or apps.
- Secure web gateway: This one is still TBA according to Perimeter 81's website at the time of writing. When it's available, it will protect your network from online threats by web filtering, meaning employees who surf the web will be protected from accidental malware infections. You can create user- or group-specific rules that determine which sites are blocked, warned against, or allowed. This limits access to distracting sites that impact productivity and prevents shadow IT by blocking applications that could put your company's data in danger.
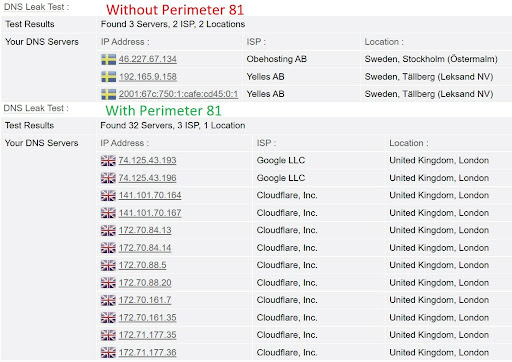
Perimeter 81 leak tests
I tested Perimeter 81 for DNS, IPv6, and WebRTC leaks and found none. No data leaks outside of the encrypted tunnel when connected to a Perimeter 81 gateway using its official client app.
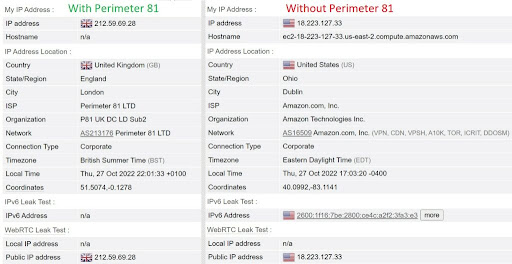
Speed: Is Perimeter 81 fast?
The cheapest plan gives you access to 500 Gbps servers, and the more expensive plans will net you 1000 Gbps servers. Note that no matter which plan you choose, the cost of adding a server is always the same: $40 per month.
We ran a few download speed tests to a 500 Mbps dedicated gateway in the UK from the USA. The average download speed was 226 Mbps. That's fast but doesn't max out the promised 500 Mbps.
Note that the volatility of the internet means our tests can only give you a rough indication of what speeds to expect. Take the results with a pinch of salt.
I did not speed test Perimeter 81's shared gateways.
Perimeter 81 prices and billing

Perimeter 81 offers four plans:
- Essentials costs $8 per user per month. Minimum 10 users. Connect up to two applications. 500 Mbps per gateway. No always-on VPN or DNS filtering, no device posture check, no SSO, no SIEM integration, no API support, and no SCIM provisioning. Support during office hours only. 14 days of audits and reports.
- Premium costs $16 per user per month. Minimum 10 users. Connect up to 10 apps. Set up to 10 FWaaS policies. Get 30 days of audits and reports. 1,000 Mbps gateways. Always on VPN. DNS filtering. Single sign-on (SSO) support. Set up as many as three device posture check profiles and three user config profiles. "Prioritized response" when you contact customer support.
- Premium Plus costs $16 per user per month. Minimum 20 users. Connect up to 100 apps. Set up to 100 FWaaS policies. SIEM integration (add-on). Dedicated customer support. API support. Set 20 device posture check profiles and 10 user config profiles. Access to shared gateways.
- Enterprise prices are negotiated directly with Perimeter 81. Minimum 50 users. Unlimited apps and FWaaS rules. 60 days of audits and reports. Unlimited device posture check and user config profiles. SCIM provisioning. 24/7 support with a dedicated agent.
Notably, the Essentials plan doesn't get FWaaS, DNS filtering, shared gateways, device posture check, SSO, SIEM integration, API support, or SCIM provisioning. If you need any of those features, then you'll need one of the more expensive plans.
Bear in mind that most organizations will need to rent at least one dedicated gateway. Gateways cost $40 per month each on all plans except Enterprise.
Customer support
We emailed Perimeter 81's customer support team using the ticket submission system on its website. Although I'd prefer live chat, the support team emailed me back within a few minutes, so I can't complain. They answered my questions to my satisfaction.
Essentials plan users only get support during office hours, while Premium and Premium Plus users get "prioritized response", whatever that means. Premium Plus and Enterprise customers get a dedicated customer success manager. Only Enterprise users get 24/7 phone support.
The website has a thorough knowledge base of FAQs, setup instructions, troubleshooting steps, and general information about Perimeter 81.
Perimeter 81 FAQs
Does Perimeter 81 have a free trial?
No, Perimeter 81 does not offer a free trial. You can request a demo to test drive the software before you make a commitment, though. It will let you configure your network, users, and resources; set up an access policy; and deploy some features.
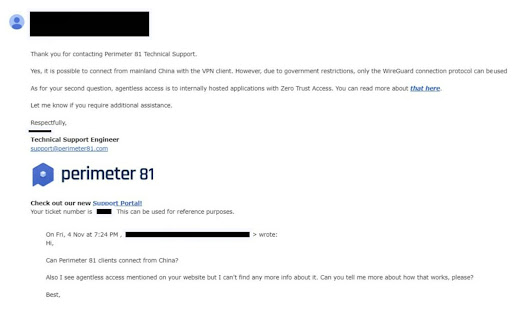
Does Perimeter 81 work in China?
Yes. Perimeter 81 informed me that it is possible to connect from mainland China using its VPN client app. However, only the WireGuard protocol will work there at the time of writing.
What is BleepingComputer’s Perimeter 81 testing methodology?
At BleepingComputer, our expert reviewers evaluate every service we review through a series of empirical tests, security analysis, and real-world experience. Our testing methodology includes:
- Download speed tests
- DNS, IPv6, and WebRTC leak testing
- Assessment of security parameters and encryption suite
- Testing all available features in a real-world environment
- Engaging with customer support
And much more. You can see our full VPN testing methodology here.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now