At least three groups split from the Conti ransomware operation have adopted BazarCall phishing tactics as the primary method to gain initial access to a victim’s network.
This allows the threat actors to deploy highly-targeted attacks that are more difficult to detect and stop because of the social engineering component.
BazarCall basics
The BazarCall/BazaCall method also referred to as call-back phishing, emerged in early 2021 as an attack vector used by the Ryuk ransomware operation, which later rebranded into Conti.
Threat actors using this technique target employees, whether from one company or entire industry, and tailor the phishing campaigns accordingly for maximum efficiency.
A BazarCall attack starts with an email informing that a subscription the recipient is allegedly paying for is about to be renewed automatically and canceling the payment is possible by calling a specific number.
Victims calling the provided phone number reach a threat actor versed in social engineering, who convinces the caller to start a remote access session via legitimate software controlled by a network intruder.
While the social engineer distracts the victim, the intruder determines how to compromise the network without triggering any alarm.
source: AdvIntel
Currently, there is evidence of three groups, all part of the former Conti ransomware operation, that used BazarCall or a version of those tactics: Silent Ransom Group, Quantum, and Roy/Zeon.
The switch to social engineering was caused by the predictability of the attacks, which caused profits to dwindle as defenders started to enforce effective mitigations.
However, tricking humans would allow for a more flexible approach that could change from one campaign to another, making attacks more difficult to identify and defend against.
According to researchers at cyber intelligence company Advanced Intelligence (AdvIntel), a Conti member said the following in internal communications:
“We can’t win the technology war because on this ground we compete with billion-dollar companies, but we can win the human factor” - Conti member
Silent Ransom Group hits major firms with BazarCall
AdvIntel researchers say that the initial faction running BazarCall campaigns separated from the Conti syndicate in March 2022 and formed a new collective called Silent Ransom Group (SRG), also tracked as Luna Moth.
Starting April 2022, as Conti was shutting down, the BazarCall operators formed their own extortion group called Silent Ransom Group (SRG). Over three months, they targeted at least 94 organizations, focusing only on stealing data and extorting the victims.
They typically send fake subscription notices impersonating Duolingo language-learning and the MasterClass online education platforms in their phishing campaigns.
source: AdvIntel
The group had a heavy focus on entities in the healthcare sector with annual revenue between $500,000 and more than $100 billion, almost 40% of them with revenue above $1 billion.
Although AdvIntel does not give any names in their report today, the researchers describe some of SRG’s major targets and victims as:
- NBA team
- a multinational weapons manufacturer and aerospace company (data stolen in the breach)
- a large IT solutions provider
- a multi-billion dollar technology and software company
- a large plumbing and HVAC supplier
AdvIntel says that their early reporting and assistance allowed the last three targeted companies in the list above to take mitigation steps that prevented a full-scale breach and data exfiltration.
Quantum uses custom BazarCall tactic
In mid-June 2022, Quantum ransomware, another splinter from Conti, started employing their version of BazarCall in an operation named “Jörmungandr” (Midgard Serpent or World Serpent in Norse Mythology).
The actors developed the operation by hiring individuals specialized in spamming, OSINT, design, and call center operators.
According to information from AdvIntel, Quantum ransomware operators were the main Conti subdivision (Conti Team Two), a group of highly-skilled hackers responsible for breaching the Costa Rica government.
Quantum ransomware emerged as a rebranded MountLocker in September 2021 but did not achieve must success. As Conti began to shutdown, the Quantum ransomware operation was taken over in April 2022 by the hackers in Conti Team Two, who kept the name from the original operators.
The BazarCall call campaigns attributed to the Quantum group have grown more sophisticated in two-months time and targeted high-profile companies based on exclusive email datasets they purchased.
For BazarCall phishing campaigns, Quantum impersonates a much larger number of brands, as observed by AdvIntel researchers:
- Ginyard International
- Oracle
- HelloFresh
- Luchechko Mortgage Team
- US Equal Opportunity Employment Commission
- CrowdStrike
- Gobble
Regardless of the theme in the phishing email, the threat actor urged recipients to call a number for further clarifications.
AdvIntel says that in one of the early stages Quantum experimented with BazarCall emails impersonating Oracle and delivered the phishing messages to more than 200,000 recipients.
Later, they deployed more sophisticated campaigns, impersonating communication from CrowdStrike cybersecurity company about abnormal activity on the victim’s network.

source: AdvIntel
In another advanced phishing operation, Quantum targeted banks with an email impersonating the Luchechko brand delivering a notification about the target discriminating against an individual applying for a loan based on their ethnicity.
AdvIntel says that the threat actor selected Luchechko because of the company’s Eastern European background. This way, when the target called the provided number the operator’s accent would not raise any suspicion.

source: AdvIntel
According to AdvIntel’s report, Quantum used Jörmungandr, their version of the BazarCall method, to target five “large-scale companies” with annual revenue of more than $20 billion, most of them in the healthcare sector.
One of them was a managed service provider (MSP) that would have allowed access to hundreds of businesses and put them at risk of encrypting them, similar to REvil ransomware’s attack on Kaseya last year.
When they obtained access to the victim network Quantum hackers typically stole data and encrypted the systems.
Conti Team One becomes Roy/Zeon
The third group splintered from Conti that adopted BazarCall-like techniques is referred to as Roy/Zeon, after the names of the two lockers (Roy and Zeon) they use to encrypt victim networks.
“This group came from the old-Guard members of Conti’s “Team One” responsible for the creation of Ryuk itself” - AdvIntel
Roy/Zeon is also the most adept at social engineering and very selective with their targets, choosing companies with a high annual revenue or from sensitive industries.
They started leveraging BazarCall techniques on June 20 in elaborate operations that impersonated the largest number of brands, many of them being vendors of software used by companies in a particular industry:
- Sygnal Partners
- iWired
- Applied Automation Tech
- RMM Central
- Itarian
- Auvik
- RemotePC
- RentoMojo
- Parcel International
- WhatFix
- EZLynx
- EATclub Canada
- Standard Notes
Roy/Zeon shows off social engineering skills
AdvIntel researchers say that the choice to impersonate the above brands was based on the assessment that targeted employees would be more inclined to talk to vendors of software specific to their activity, which is less known outside the industry.
Furthermore, Roy/Zeon also impersonated a real employee of the software solutions management company Edifecs, thus increasing the feeling of legitimacy upon cursory verification of the sender’s identity.
AdvIntel researchers found that in a recent campaign the threat actor targeted financial institutions with a fake notification from the vendor of Standard Notes - a note-taking app featuring end-to-end encryption - about the end of the trial period.
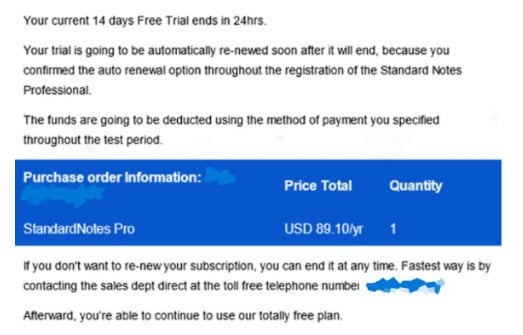
source: AdvIntel
Roy/Zeon used the BazarCall technique as an initial attack vector at “a major housing authority in northeast New Jersey,” which led to encrypting more than 130 servers and 500 workstations.
The threat actor used an unprotected VPN to gain access to the company network and stole 600GB of data.
Based on intelligence from AdvIntel, the group demanded a $5.5 million ransom and threatened to release documents allegedly containing evidence of embezzlement activity.
The researchers were able to identify eight other victims of Roy/Zeon’s BazarCall campaigns:
- a full-service landscaping company in Texas
- a leading Italian producer of pharmaceuticals
- a manufacturer of machined metal components
- a specialized service center for Porsche, Bentley, Lamborghini, Audi, and Mercedes
- a small Italian municipality
- a Canadian electrical and instrumentation contractor
- a large Canadian distributor of Mediterranean foods
- a city magazine focused on the Detroit area
The three groups adopting the BazarCall tactics to breach companies have shown that the extortion business, either by just stealing data or combined with network encryption, can still be profitable.
Call-back phishing pays off
AdvIntel researchers note that the BazarCall campaigns they attributed to SRG, Quantum, and Roy/Zeon in a little over three months led to 20 high-profile accesses and ransom demands as large as tens of millions of U.S. dollars.
The risk assessment for this new attack vector is grim as threat actors can use it to increase the infection rate with software used maliciously like Atera, Cobalt Strike, Brute Ratel, Sliver, Zoho Remote Desktop Control, Remote Monitoring and Management agents.
While detecting the initial stage of the attack may be difficult, defenders could track unusual signals from communication with the command and control server and the beacons planted on machines that indicate an infection.
Additionally, AdvIntel recommends monitoring the network to potential lateral movement activity that could affect the domain controller.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now