Table of Contents
- 1What is the Locker Ransomware?
- 2What to do if your computer is infected with the Locker Ransomware
- 3What happens when the 72 hour timer runs out?
- 4How do you become infected with the Locker Ransomware?
- 5Locations encrypted by Locker
- 6Will paying the ransom actually decrypt your files?
- 7How to restore files encrypted by the Locker Ransomware
- 8How to decrypt your files using Locker Unlcoker
- 9How to restore files encrypted by Locker using Shadow Volume Copies
- 10How to restore files that have been encrypted on DropBox folders
- 11How to prevent your computer from becoming infected by Locker
- 12How to allow specific applications to run when using Software Restriction Policies
What is the Locker Ransomware?
Brief Overview:
Locker is a file-encrypting ransomware program that targets all versions of Windows including Windows XP, Windows Vista, Windows 7, and Windows 8. On May 25 at Midnight local time, a Trojan.Downloader was issued the command to install Locker onto an infected computer. Once Locker was activated, it scanned all drive letters for specific file extensions and encrypted them using AES encryption. When it finished encrypting your data the infection displayed a screen titled Locker <version number>, where version number were random numbers such as 1.7, 2.62, 1.91, etc. This Locker screen provides information on how your files were encrypted and then demand .1 bitcoins to decrypt your files. If you do not pay the ransom within 72 hours your ransom price will increase to 1 bitcoin.
On May 30th, 2015 the Locker ransomware developer released a dump of all of the private decryption keys along with an apology. This apology stated that on June 2nd if a user is still running the infection, it will automatically decrypt the encrypted files for free. Now that the private decryption keys were available, Nathan Scott wrote a decrypter that allowed victim's to decrypt their files for free. More information about this decrypter can be found here.
On June 2nd, as the developer promised, those who were still running the infection were shown an apology message and found that their files were decrypted. The message shown was:
Advanced Overview:
The Locker ransomware is installed through a Trojan.Downloader that was already present on a victim's computer. This Trojan.Downloader was installed as a Windows service in C:\Windows\SysWow64 with a random file name. Example filenames are solaraddtogs.exe or twitslabiasends.exe. On May 25th at Midnight local time, a command was sent to the Trojan.Downloader telling it to install the Locker ransomware on the infected user's computer. As part of the Trojan.Downloader and Locker installation, another service was installed at C:\ProgramData\Steg\steg.exe, which when executed installed the C:\ProgramData\Tor folder. When this was completed another service was created called C:\ProgramData\rkcl\ldr.exe, which loaded the C:\ProgramData\rkcl\rkcl.exe program. The rkcl.exe program is the main executable for the Locker ransomware.
Once Locker was started it began to scan all the drive letters on your computer for data files to encrypt. When looking for files to encrypt, Locker searches for only lower case extensions and as it uses case-sensitive string comparison, .jpg files would be encrypted, but not .JPG files. The list of extensions targeted by Locker is:
It important to stress that Locker will scan all drive letters on your computer including removable drives, network shares, and even DropBox mappings. In summary, if there is a drive letter on your computer it will be scanned for data files to encrypt by the ransomware
When the infection has finished scanning your computer it will also delete the Shadow Volume Copies stored on the C: drive. It does this so that you cannot use the shadow volume copies to restore your files. As it only deletes the Shadow Volume Copies on the C:\ drive, it may be possible to use a program like ShadowExplorer to restore files that were stored on other drives. In some cases the Shadow Volumes were not properly deleted at all and you will be able to restore files from the C: drive as well. The command used to delete the Shadow Volumes is:
vssadmin.exe delete shadows /for=C: /all /quiet
While the install process is occurring, it will also search for processes related to known malware analysis tools and will check if the malware is running within a virtual machine. If it detects that the infection is running in VMware or VirtualBox it will self-terminate. It will also self-terminate if it detects any of the following processes running:
It does this to protect itself from being analyzed by security researchers who may possibly be able to help Locker's victims.
Now that the computer's data has been encrypted it will display the Locker application. The title of the screen will be Locker and then a random version number, such as Locker 1.7 or Locker 2.89. Below are screenshots of the various screens.
The Locker screen is broken up into four sections. These are:
- Information Screen - This screen contains information about what has happened to your files.
- Payment Screen - This screen contains your unique bitcoin address and information on how to send payment.
- Files Screen - This screen lists the files that were encrypted.
- Status Screen - This screen will list the amount of files encrypted and check your payment status.
In order to pay the ransom a victim needs to send .1 bitcoins to the assigned bitcoin address. The Locker application will then periodically contact blockchain.info to see if there is a balance for the associated bitcoin address. If blockchain.info indicates that there is a correct balance, the Locker application will then do a second check against the malware's TOR command and control server located at jmslfo4unv4qqdk3.onion. If both requests indicate that a payment has been made, the application will download the priv.key file and store it in the C:\ProgramData\rkcl folder on the infected computer. This file contains the private decryption key used to decrypt your files. The Locker application will then begin to decrypt all of your files.
There are other files created in the C:\ProgramData\rkcl folder. These files are described below:
data.aa0 - This file contains a list of the encrypted files.
data.aa1 - Unknown purpose
data.aa6 - The victim's unique bitcoin address
data.aa7 - An RSA key. This is not the decryption key.
data.aa8 - Contains the version number for the Locker graphical interface.
data.aa9 - The date the ransomware became active
data.aa11 - Unknown purpose
data.aa12 - Unknown purpose
priv.key - This file contains the private decryption key that can be used to decrypt your files. It only appears after you pay the ransom.
What to do if your computer is infected with the Locker Ransomware
If you are infected with Locker then you can use Emsisoft, Malwarebytes, Hitman, or pretty much any other antivirus program to remove the infections files from your computer. Now that a decrypter has been released, it is no longer necessary to keep the C:\ProgramData\rkcl folder. Before you remove it, though, we suggest you write down and save your bitcoin address as it will make it easier to use the free decrypter.
To manually remove the infection, you can remove the folders and files found in the following locations:
C:\ProgramData\-
C:\ProgramData\Tor\
C:\ProgramData\rkcl
C:\ProgramData\Digger
C:\ProgramData\Steg\
C:\Windows\SysWow64\<random>.exe
C:\Windows\SysWow64\<random>.bin
C:\Windows\SysWow64\<random>.dll
C:\Windows\System32\<random>.bin
If you need help identifying the files to remove, please ask in the Lock Support Topic.
What happens when the 72 hour timer runs out?
When you become infected with the Locker ransomware it will display a 72 hour countdown and state that you must pay the ransom before it runs out or your encryption key will be deleted. The exact message you will see within the Locker screen is:
This message is being displayed to scare you into purchasing the key and your decryption key will not be deleted. Instead the ransom amount will increase to 1 bitcoins and you will still have the opportunity to pay the ransom. The malware developers treat this as a business and it is not good business to take money off the table by deleting your encryption key.
How do you become infected with the Locker Ransomware?
At this time the only known vector for this ransomware is the Trojan.Downloader that is installed through a cracked version of Minecraft. As some people have stated that they do not, and never had, Minecraft installed on their computer there are mostly likely other vectors that are unknown at this time. The known Minecraft related Trojans are:
and
It is possible that this infection is also installed through exploit kits that use security vulnerabilities in insecure programs installed on your computer. Therefore, it is imperative that everyone keeps Windows and their installed programs up-to-date so that they have the latest security patches. You can use these tutorials for more information on keeping your Windows installation and installed programs updated:
How to update Windows
How to detect vulnerable and outdated programs using Secunia Personal Software Inspector (PSI)
Locations encrypted by Locker
The Locker ransomware will encrypt data files found on any local drive or mapped network drive. It will only encrypt files on network shares if it mapped as a drive letter on the infected computer. If it is not mapped as a drive letter, then Locker will not encrypt any files on a UNC network share.
It is still strongly suggested that you secure all open shares by only allowing writable access to the necessary user groups or authenticated users. This is an important security principle that should be used at all times regardless of infections like these.
Will paying the ransom actually decrypt your files?
First and foremost, only pay the ransom if you have absolutely no choice. By paying the ransom you just encourage the malware developers to continue making ransomware like Locker. With that said it is understood that sometimes you simply have no choice and must pay the ransom to get your files back.
If you pay the ransom then Locker will decrypt your files. When you pay the ransom, the Locker application will download your private decryption key and save it in the C:\ProgramData\rkcl\priv.key file. Once the key file is made, it will begin decrypting the files on your computer.
How to restore files encrypted by the Locker ransomware
Now that the private decryption keys have been released, you can decrypt your files for free using Locker Unlocker by Nathan Scott. More information can be found in this section:
If the Locker Unlock did not work, then you need to use one of the following other methods:
Method 1: Backups
The first and best method is to restore your data from a recent backup. If you have been performing backups, then you should use your backups to restore your data.
Method 2: File Recovery Software
When the Locker ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you can use file recovery software such as R-Studio or Photorec to possibly recover some of your original files. It is important to note that the more you use your computer after the files are encrypted the more difficult it will be for file recovery programs to recover the deleted un-encrypted files.
Method 3: Shadow Volume Copies
As a last resort, you can try to restore your files via Shadow Volume Copies. Unfortunately, this infection will attempt to delete any Shadow Volume Copies on your computer, but sometimes it fails to do so and you can use them to restore your files. For more information on how to restore your files via Shadow Volume Copies, please see the link below:
How to restore files encrypted by Locker using Shadow Volume Copies
Method 4: Restore DropBox Folders
If you had your dropbox account mapped as a drive letter then it is possible that its contents were encrypted by Locker. If this is the case you can use the link below to learn how to restore your files.
How to restore files that have been encrypted on DropBox folders
How to decrypt your files using Locker Unlocker
As the malware developer has released the private decryption keys, you can decrypt your files for free using Locker Unlocker by Nathan Scott. To get started, download Locker Unlocker from the following link.
Once the program is downloaded, double-click on the LockerUnlocker icon to start the program. Once started you will see a screen similar to the one below:
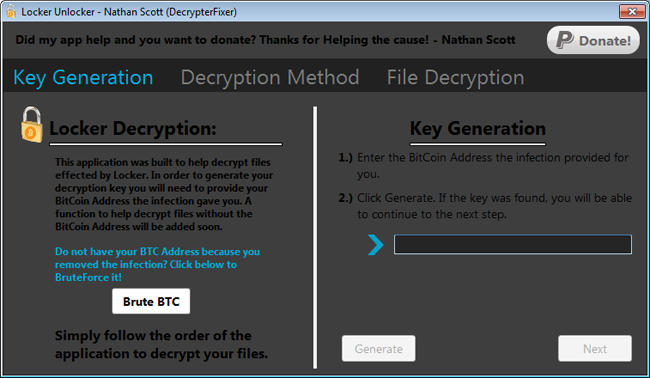
At the above screen, if you know your bitcoin address enter it in the field on the right. Otherwise, if you do not know the bitcoin address that was assigned to you by the Locker ransomware, you need to click on the Brute BTC option and then browse to an encrypted file. Locker Unlocker will then attempt to match all of the known private decryption keys against your selected file and when a match is found, it will automatically add the bitcoin address to the field on the right.
Once the bitcoin address is entered into the field, whether because you knew it or you brute forced it, click on the Generate button to create your private key file, and when it's done, click on the Next button. You will now be at a screen asking if you wish to use the List Decryption or Directory Decryption methods, which are described below.
List Decryption (Preferred Method):
It is suggested that you use the List Decryption as it will use the list of encrypted files that was generated by the ransomware. To use this feature click on the List Decryption button and then browse to the C:\ProgramData\rkcl\data.aa0 file. Once you have selected your encrypted file list, click on the Start button and Locker Unlocker will begin to decrypt your files.
Directory Decryption:
If you wish to copy all of your encrypted files to a specific directory and decrypt that directory, then you should select the Directory Decryption option. Once you select this option, you will be prompted to select the directory that you wish to decrypt and then click on the Start button. It should be noted that every file in that directory will be decrypted even if the file is not encrypted. If you have files that are not encrypted in that folder, then they will become unusable.
Advanced Options:
Both the List Decryption and Directory Decryption methods have two options that you can use:
Create Log on Desktop - This option will create a log on your desktop detailing what files were decrypted.
Remove Encrypted Files - This option will remove the encrypted file when it is decrypted. It is not advised that you do this unless you know for sure that the decryption works properly with your files.
If there are any questions or issues using Locker Unlocker, please post them in our Locker Support Topic.
How to restore files encrypted by Locker using Shadow Volume Copies
If you had System Restore enabled on the computer, Windows creates shadow copy snapshots that contain copies of your files from that point of time when the system restore snapshot was created. These snapshots may allow us to restore a previous version of our files from before they had been encrypted. This method is not fool proof, as even though these files may not be encrypted they also may not be the latest version of the file. Please note that Shadow Volume Copies are only available with Windows XP Service Pack 2, Windows Vista, Windows 7, & Windows 8.
In this section we provide two methods that you can use to restore files and folders from the Shadow Volume Copy. The first method is to use native Windows features and the second method is to use a program called ShadowExplorer. It does not hurt to try both and see which methods work better for you.
Using native Windows Previous Versions:
To restore individual files you can right-click on the file, go into Properties, and select the Previous Versions tab. This tab will list all copies of the file that have been stored in a Shadow Volume Copy and the date they were backed up as shown in the image below.
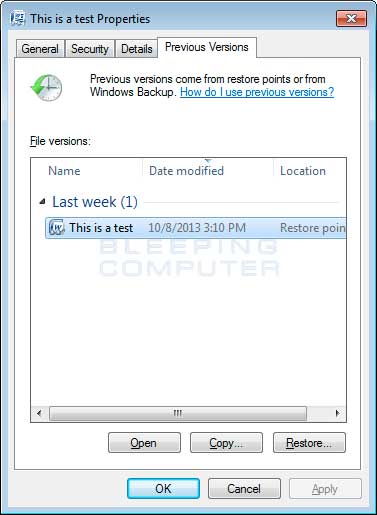
To restore a particular version of the file, simply click on the Copy button and then select the directory you wish to restore the file to. If you wish to restore the selected file and replace the existing one, click on the Restore button. If you wish to view the contents of the actual file, you can click on the Open button to see the contents of the file before you restore it.
This same method can be used to restore an entire folder. Simply right-click on the folder and select Properties and then the Previous Versions tabs. You will then be presented with a similar screen as above where you can either Copy the selected backup of the folder to a new location or Restore it over the existing folder.
Using ShadowExplorer:
You can also use a program called ShadowExplorer to restore entire folders at once. When downloading the program, you can either use the full install download or the portable version as both perform the same functionality.
When you start the program you will be shown a screen listing all the drives and the dates that a shadow copy was created. Select the drive (blue arrow) and date (red arrow) that you wish to restore from. This is shown in the image below.
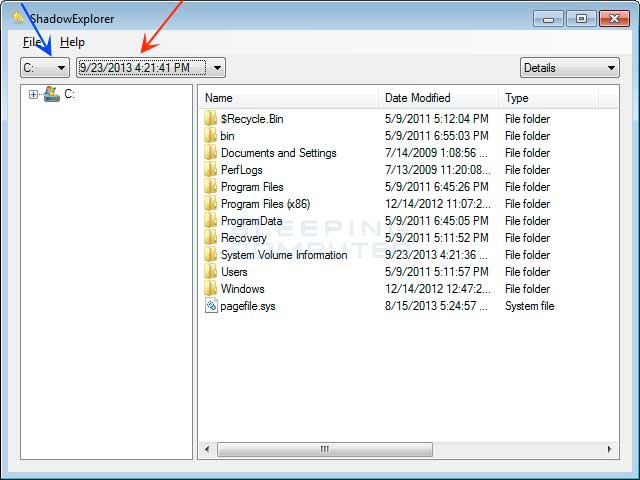
To restore a whole folder, right-click on a folder name and select Export. You will then be prompted as to where you would like to restore the contents of the folder to.
How to restore files that have been encrypted on DropBox folders
If you have DropBox mapped to a drive letter on an infected computer or synchronized to a folder, Locker will attempt to encrypt the files on it. DropBox offers free versioning on all of its accounts that will allow you to restore encrypted files through their website. Unfortunately, the restoral process offered by DropBox only allows you to restore one file at a time rather than a whole folder. If you need instructions on restoring an entire folder in DropBox, please click here.
To restore a file, simply login to the DropBox web site and navigate to the folder that contains the encrypted files you wish to restore. Once you are in the folder, right-click on the encrypted file and select Previous Versions as shown in the image below.
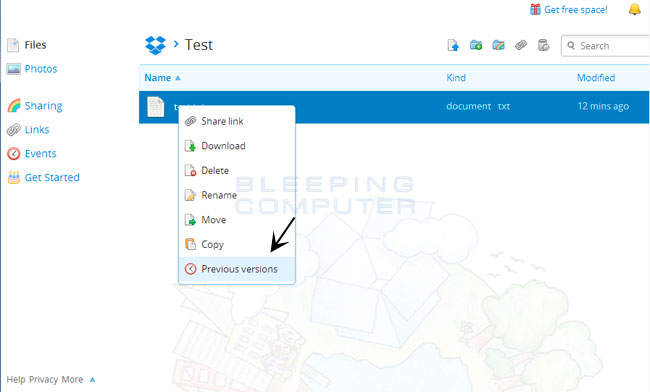
When you click on Previous versions you will be presented with a screen that shows all versions of the encrypted file.
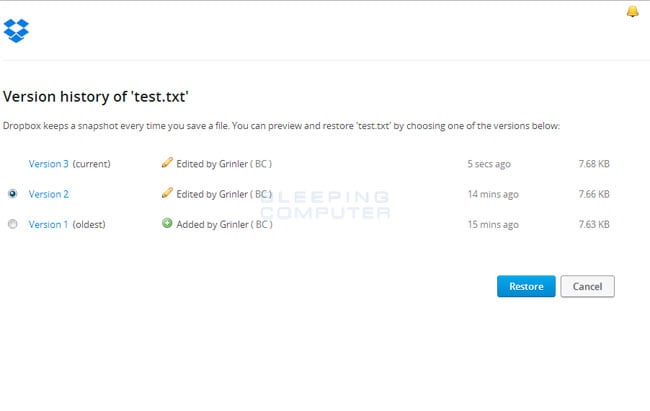
Select the version of the file you wish to restore and click on the Restore button to restore that file.
Unfortunately the process outlined above can be very time consuming if there are many folder to restore. In order to restore an entire folder of encrypted files, you can use the dropbox-restore python script located here. Please note that this script requires Python to be installed on the encrypted computer to execute the script. Instructions on how to use this script can be found in the README.md file for this project.
How to prevent your computer from becoming infected by Locker
There are a few methods and utilities that we recommend in order to protect your computer from ransomware infections. Three of the methods are the Emsisoft Anti-Malware, HitmanPro: Alert, and the Malwarebytes Anti-Ransomware and HitmanPro: Alert programs. The fourth option is to utilize Software Restriction Policies that prevent programs from being allowed to execute from certain locations. In full disclosure, BleepingComputer.com makes a commission off of the sales of Emsisoft Anti-Malware, HitmanPro: Alert, and CryptoPrevent, but does not from Malwarebytes Anti-Ransomware.
Emsisoft Anti-Malware:
Emsisoft Anti-Malware, or EAM, has a feature called behavior blocker that has a proven track record of blocking ransomware before it can start encrypting data on your computer. Unlike traditional antivirus definitions, EAM's behavior blocker examines the behavior of a process and if this behavior contains certain characteristics commonly found in malware it will prevent it from running. Using the detection method, behavior blocker detects when a process is scanning a computer for files and then attempting to encrypt them. If it discovers this behavior, it will automatically terminate the process.
According to an article at Emsisoft's site, EAM's behavior blocker was able to block 20 crypto-ransomware families without the use of signatures.
You can find more information about Emsisoft Anti-Malware and behavior blocker here: https://www.emsisoft.com/en/software/antimalware/
HitmanPro: Alert:
HitmanPro: Alert is a great program as well but is designed as a full featured anti-exploit program and is not targeted exclusively at ransomware infections. Alert provides protection from computer vulnerabilities and malware that attempts to steal your data. Unfortunately, because this program has a much broader focus it sometimes needs to be updated as new ransomware is released. As long as you stay on top of the updates, HitmanPro: Alert offers excellent protection.
You can find more information about HitmanPro: Alert here: http://www.surfright.nl/en/alert
Malwarebytes Anti-Ransomware
Malwarebytes Anti-Ransomware is another program that does not rely on signatures or heuristics, but rather by detecting behavior that is consistent with what is seen in ransomware infections. At this point, Malwarebytes Anti-Ransomware is currently in beta, so be careful about using this on a production environment until the kinks are worked out.
You can download and get more information information about Malwarebytes Anti-Ransomware here: https://www.bleepingcomputer.com/download/malwarebytes-anti-ransomware/
Software Restriction Policies:
You can use the Windows Group or Local Policy Editor to create Software Restriction Policies that block executables from running when they are located in specific paths. For more information on how to configure Software Restriction Policies, please see these articles from MS:
http://support.microsoft.com/kb/310791
http://technet.microsoft.com/en-us/library/cc786941(v=ws.10).aspx
The file paths that have been used by this infection and its droppers are:
%Temp%
C:\Windows\SysWow 64
C:\ProgramData
In order to block the Locker ransomware you want to create Path Rules so that it is not allowed to be started. To create these Software Restriction Policies, you can either use the CryptoPrevent tool or add the policies manually using the Local Security Policy Editor or the Group Policy Editor. Both methods are described below.
How to use the CryptoPrevent Tool:
FoolishIT LLC was kind enough to create a free utility called CryptoPrevent that automatically adds the suggested Software Restriction Policy Path Rules listed above to your computer. This makes it very easy for anyone using Windows XP SP 2 and above to quickly add the Software Restriction Policies to your computer in order to prevent Locker from being executed in the first place. This tool is also able to set these policies in all versions of Windows, including the Home versions.
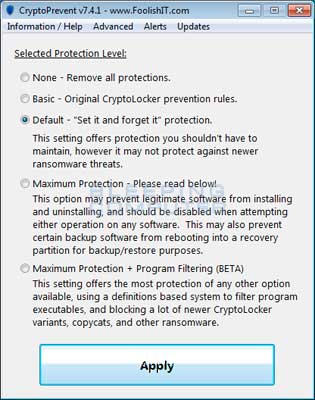
A new feature of CryptoPrevent is the option to whitelist any existing programs in %AppData% or %LocalAppData%. This is a useful feature as it will make sure the restrictions that are put in place do not affect legitimate applications that are already installed on your computer. To use this feature make sure you check the option labeled Whitelist EXEs already located in %appdata% / %localappdata% before you press the Block button.
You can download CryptoPrevent from the following page:
For more information on how to use the tool, please see this page:
Once you run the program, simply click on the Apply Protection button to add the default Software Restriction Policies to your computer. If you wish to customize the settings, then please review the checkboxes and change them as necessary. If CryptoPrevent causes issues running legitimate applications, then please see this section on how to enable specific applications. You can also remove the Software Restriction Policies that were added by clicking on the Undo button.
How to manually create Software Restriction Policies to block Locker:
In order to manually create the Software Restriction Policies you need to be using Windows Professional or Windows Server. If you want to set these policies for a particular computer you can use the Local Security Policy Editor. If you wish to set these policies for the entire domain, then you need to use the Group Policy Editor. Unfortunately, if you are a Windows Home user, the Local Policy Editor is not available and you should use the CryptoPrevent tool instead to set these policies. To open the Local Security Policy editor, click on the Start button and type Local Security Policy and select the search result that appears. You can open the Group Policy Editor by typing Group Policy instead. In this guide we will use the Local Security Policy Editor in our examples.
Once you open the Local Security Policy Editor, you will see a screen similar to the one below.
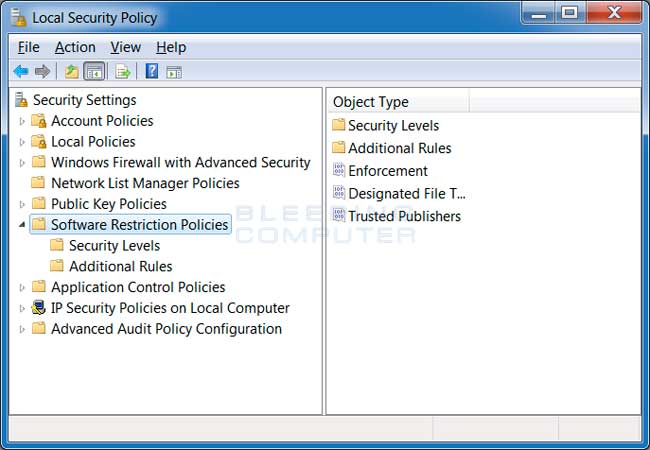
Once the above screen is open, expand Security Settings and then click on the Software Restriction Policies section. If you do not see the items in the right pane as shown above, you will need to add a new policy. To do this click on the Action button and select New Software Restriction Policies. This will then enable the policy and the right pane will appear as in the image above. You should then click on the Additional Rules category and then right-click in the right pane and select New Path Rule.... You should then add a Path Rule for each of the items listed below.
If the Software Restriction Policies cause issues when trying to run legitimate applications, you should see this section on how to enable specific applications.
Below are a few Path Rules that are suggested you use to not only block the infections from running, but also to block attachments from being executed when opened in an e-mail client.
Block Locker executable in %AppData%
Path: %AppData%\*.exe
Security Level: Disallowed
Description: Don't allow executables to run from %AppData%.Block Locker executable in %ProgramData%
Path: %ProgramData%\*.exe
Security Level: Disallowed
Description: Don't allow executables to run from %ProgramData%.Block Locker executable in %LocalAppData%
Path if using Windows XP: %UserProfile%\Local Settings\*.exe
Path if using Windows Vista/7/8: %LocalAppData%\*.exe
Security Level: Disallowed
Description: Don't allow executables to run from %AppData%.Block executables run from archive attachments opened with WinRAR:
Path if using Windows XP: %UserProfile%\Local Settings\Temp\Rar*\*.exe
Path if using Windows Vista/7/8: %LocalAppData%\Temp\Rar*\*.exe
Security Level: Disallowed
Description: Block executables run from archive attachments opened with WinRAR.Block executables run from archive attachments opened with 7zip:
Path if using Windows XP: %UserProfile%\Local Settings\Temp\7z*\*.exe
Path if using Windows Vista/7/8: %LocalAppData%\Temp\7z*\*.exe
Security Level: Disallowed
Description: Block executables run from archive attachments opened with 7zip.Block executables run from archive attachments opened with WinZip:
Path if using Windows XP: %UserProfile%\Local Settings\Temp\wz*\*.exe
Path if using Windows Vista/7/8: %LocalAppData%\Temp\wz*\*.exe
Security Level: Disallowed
Description: Block executables run from archive attachments opened with WinZip.Block executables run from archive attachments opened using Windows built-in Zip support:
Path if using Windows XP: %UserProfile%\Local Settings\Temp\*.zip\*.exe
Path if using Windows Vista/7/8: %LocalAppData%\Temp\*.zip\*.exe
Security Level: Disallowed
Description: Block executables run from archive attachments opened using Windows built-in Zip support.
You can see an event log entry and alert showing an executable being blocked:
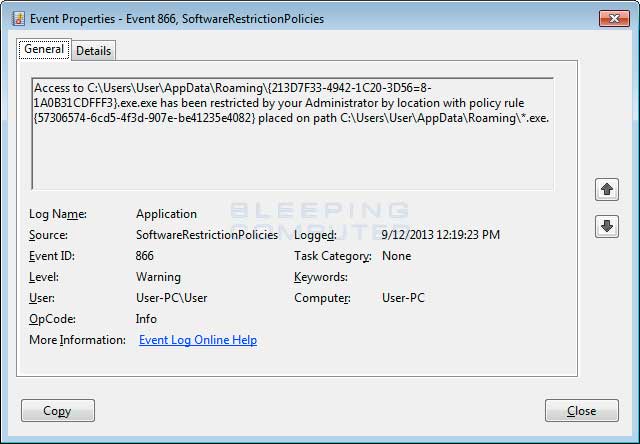
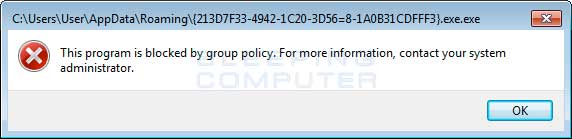
If you need help configuring this, feel free to ask in the Locker Ransomware Support Topic.
How to allow specific applications to run when using Software Restriction Policies
If you use Software Restriction Policies, or CryptoPrevent, to block Locker you may find that some legitimate applications no longer run. This is because some companies mistakenly install their applications under a user's profile rather than in the Program Files folder where they belong. Due to this, the Software Restriction Policies will prevent those applications from running.
Thankfully, when Microsoft designed Software Restriction Policies they made it so a Path Rule that specifies a program is allowed to run overrides any path rules that may block it. Therefore, if a Software Restriction Policy is blocking a legitimate program, you will need to use the manual steps given above to add a Path Rule that allows the program to run. To do this you will need to create a Path Rule for a particular program's executable and set the Security Level to Unrestricted instead of Disallowed as shown in the image below.
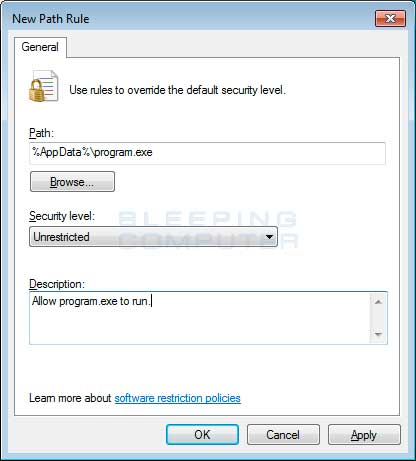
Once you add these Unrestricted Path Rules, the specified applications will be allowed to run again.
